As enterprises transition to a hybrid Active Directory (AD) environment, it’s important that they address identity management challenges. For example, employees often struggle to remember a different password for each...

Five reasons to choose Log360, part 1: User-friendly deployment and UI
SIEM solutions are a must-have in any organization’s security toolkit. They allow you to analyze events from your network, gain actionable insights into network activity,...

[Infographic] Top three approaches to dealing with account lockouts
In the previous blog of this series, “[Infographic]Three tips to simplify Active Directory compliance and auditing”, we discussed the tips and tricks to achieve compliance....

[Infographic]Three tips to simplify Active Directory compliance and auditing
In the previous blog of this series, “[Infographic] Still manually onboarding users into Active Directory? There’s a better way!“, we discussed the tips and tricks to...
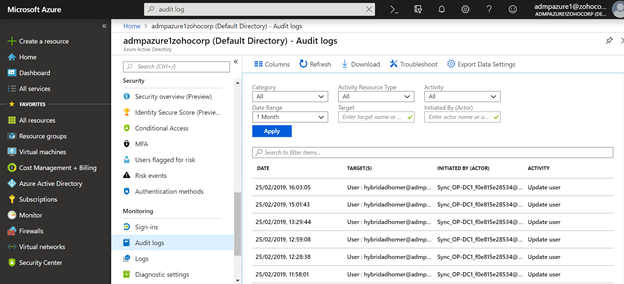
Detecting changes in privileged accounts in Azure AD
Monitoring and protecting privileged accounts is paramount because failure to do so can lead to loss or theft of sensitive information, or enable malware to...

[Infographic] Top three password-related issues that plague IT admins
Managing user identities is an everyday affair for an IT administrator. However, in large organizations with complex IT hierarchies, things spiral out of control very quickly. Below...
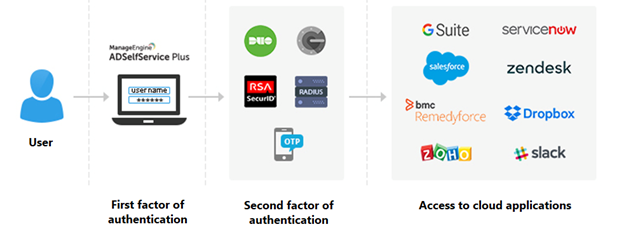
Two-factor authentication for secure access to cloud apps in hybrid AD
In an earlier post, we dealt with the benefits of single sign-on (SSO) for cloud apps in hybrid Active Directory (AD). While SSO is good...