Detecting changes in privileged accounts in Azure AD
Monitoring and protecting privileged accounts is paramount because failure to do so can lead to loss or theft of sensitive information, or enable malware to compromise your network. Privileged accounts can include global administrators, Azure subscription administrators, and users who have administrator access in VMs or SaaS apps.
In Azure Active Directory (AD), auditing is enabled by default. You can check all activity in any given Azure AD environment using the Azure Portal, PowerShell cmdlets, and a security information and event management (SIEM) solution. In Azure AD, select Roles and Administrators to see the list of all available roles and their permissions. Any changes made to the accounts in Roles and Administrators can be viewed and monitored under Audit Logs as well, as seen here in Figure 1.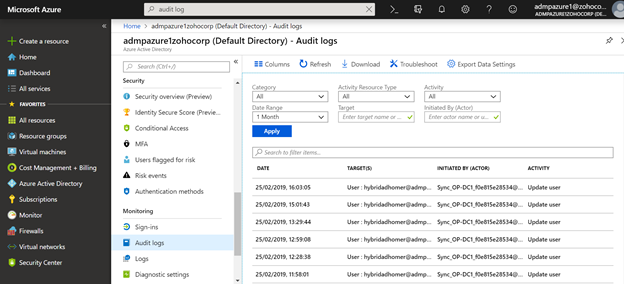 Figure 1. Audit Logs display all activity happening in an Azure AD environment.
Figure 1. Audit Logs display all activity happening in an Azure AD environment. Figure 2. Alerts that are set up to monitor Azure AD roles.
To use PIM, you must have one of the following paid or trial licenses:
Figure 2. Alerts that are set up to monitor Azure AD roles.
To use PIM, you must have one of the following paid or trial licenses: Figure 3. Configuring a new alert profile in ADAudit Plus.
Figure 3. Configuring a new alert profile in ADAudit Plus. Figure 4. You can set up filters to monitor and create alerts for specific activities in Azure AD using ADAudit Plus.
Figure 4. You can set up filters to monitor and create alerts for specific activities in Azure AD using ADAudit Plus.
 Figure 1. Audit Logs display all activity happening in an Azure AD environment.
Figure 1. Audit Logs display all activity happening in an Azure AD environment.Setting up alerts in Azure AD
Azure AD Privileged Identity Management (PIM) is a service that enables you to manage and monitor access to privileged accounts in your organization. It can generate alerts when there is suspicious or unsafe activity in your environment. When an alert is triggered, it shows up on the PIM dashboard. Select Alerts (Figure 2) to see the list of alerts generated, and select a report to see the user or roles that triggered the alert. Figure 2. Alerts that are set up to monitor Azure AD roles.
To use PIM, you must have one of the following paid or trial licenses:
Figure 2. Alerts that are set up to monitor Azure AD roles.
To use PIM, you must have one of the following paid or trial licenses:- Azure AD Premium P2
- Enterprise Mobility + Security (EMS) E5
Configuring alerts using ADAudit Plus
With more organizations implementing a hybrid AD environment, monitoring changes across both on-premises AD and Azure AD using native tools alone is complex and time-consuming. Be it on-premises AD or Azure AD, ADAudit Plus ensures complete change monitoring for privileged accounts. It gives you a single, correlated view of all activity happening across your hybrid AD environment. ADAudit Plus allows you to monitor changes made to privileged accounts from anywhere with notifications delivered directly to your inbox, so you can always stay on top of all changes within your IT environment. Apart from the 200 preconfigured reports, you can also customize reports to meet your specific auditing needs and schedule them as needed. To configure alerts in ADAudit Plus: Step 1: Click the Configuration tab in ADAudit Plus. Step 2: Select Create Alert Profile from the list on the left pane. Step 3: Select the Domain and Report Profile for which you need the alert, as seen below in figure 3. Step 4: Under Advanced Configuration, you can set up filters for the type of activity you need alerts for. For example, in figure 4 you see that alerts are set for adding or removing a member from the domain. Step 5: Save the alert profile. Now you will be notified of unauthorized changes no matter where you are, so you can act fast. Figure 3. Configuring a new alert profile in ADAudit Plus.
Figure 3. Configuring a new alert profile in ADAudit Plus. Figure 4. You can set up filters to monitor and create alerts for specific activities in Azure AD using ADAudit Plus.
Figure 4. You can set up filters to monitor and create alerts for specific activities in Azure AD using ADAudit Plus.