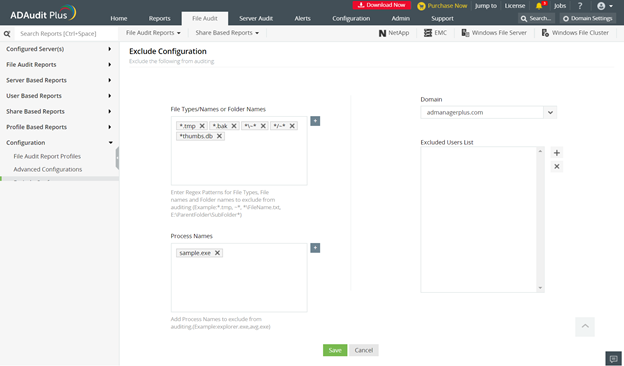
IT administrators have tough jobs. From keeping the network running to servicing piles of support requests, their hands are always full. Even with so much on their...

Quick tips to ensure your Azure AD is safe from threats
Being the gatekeeper of Microsoft’s cloud solutions, Azure AD comes with a wide range of default security measures; these include insights on risky sign-ins and user accounts that...
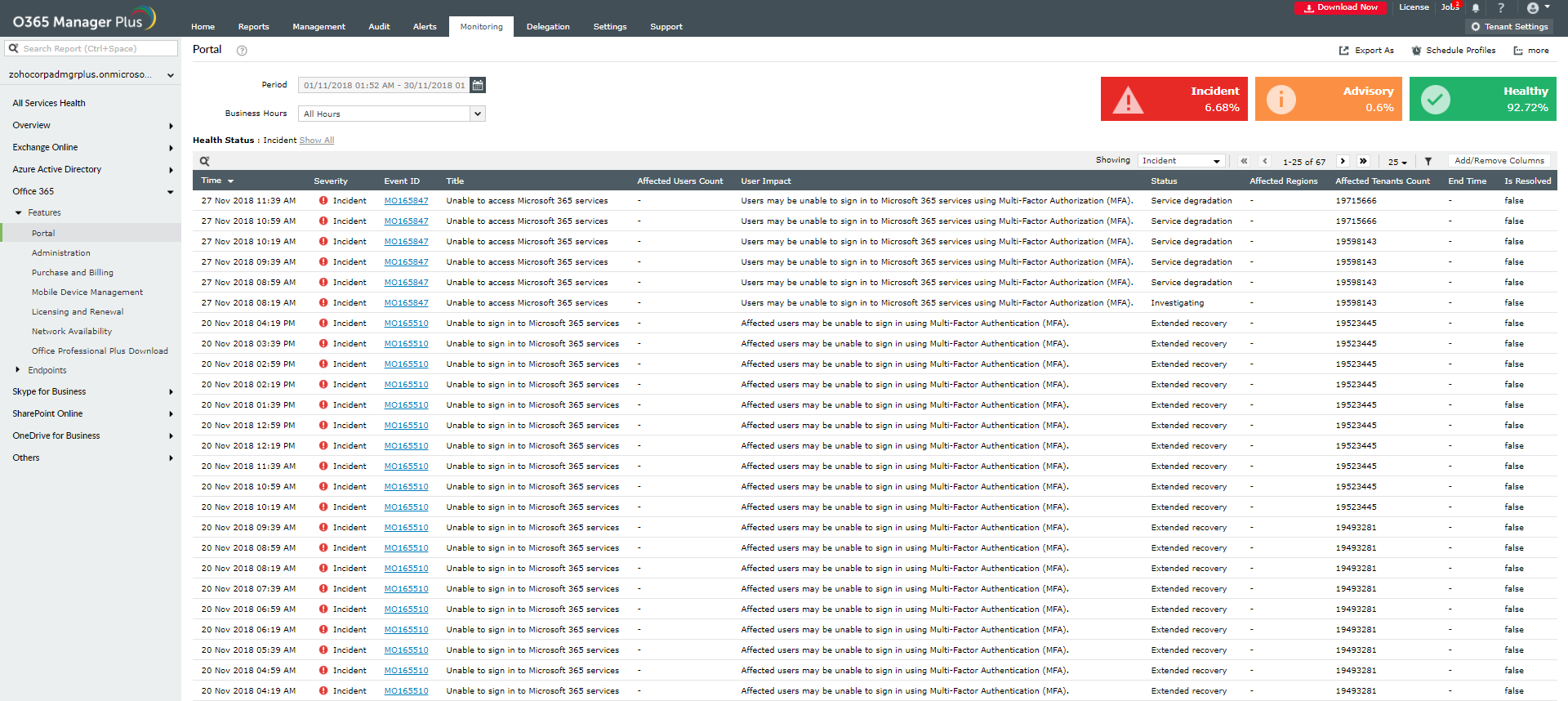
All you need to know about the November Azure AD MFA outages
In early November of 2018, Microsoft’s Azure Active Directory (AD) multi-factor authentication (MFA) service suffered two global outages. The first outage occurred on November 19, 2018, and users of Azure AD authentication services—including...
Securing Hybrid Active Directory webinar series
Active Directory (AD) administrators are heading into 2019 with security on their minds. The attacks of the past combined with the movement toward hybrid environments...

Five best practices for Active Directory password management [Free webinar]
Passwords are an unavoidable part of both employees’ and IT administrators’ lives. Organizations need a solution that can combat redundant IT service calls, manage passwords...
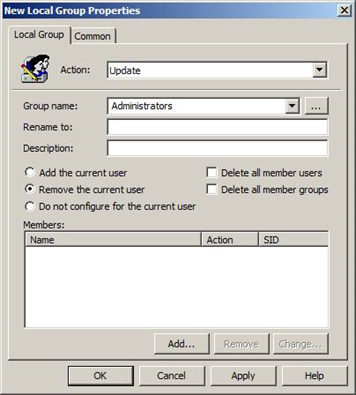
Minimizing membership in the local Administrators group on workstations
If you have a long list of users with administrative rights, there’s a good chance you’ve offered excessive amount of privilege to accounts that don’t...