For organizations to maintain security and reduce their threat exposure, it’s critical to understand the vulnerabilities and challenges of Windows authentication protocols. For instance, the inherent...
Zooming in on UEBA: Answering the “what” and the “how”
What is UEBA? User and entity behavior analytics (UEBA) is a relatively new category of cybersecurity tools that utilize machine learning (ML) algorithms to detect abnormalities in the behavior of...

Find out which of your employees pose the greatest security risk
Among the different types of cyberattacks, insider threats are the hardest to track and have the highest rate of success. This can be attributed to...

User and entity behavior analytics: The intelligent guardian of your business
Identities are easy to fake, but not actions. Closely monitoring the behavior of a person can reveal a lot about their true intentions. Similarly, keeping...

Dealing with three pathbreaking scenarios under the CCPA
The “right to be forgotten” is one of the new rights consumers will have under the CCPA. “I’d like to pay with my credit card.”...
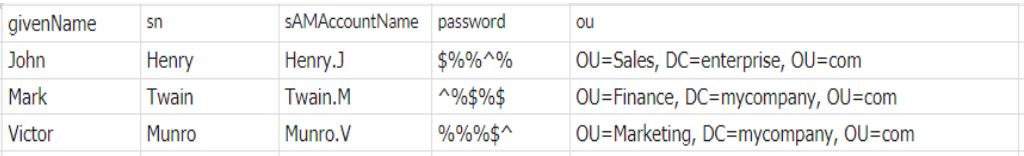
How to create bulk users in Active Directory using a CSV file
Dear admin, Please create Active Directory user accounts, cloud app accounts, home folders, mailboxes, and other requirements for the following new employees. Attached is the list of 100 new members....
2FA based on OU/group membership in hybrid Active Directory
In a previous blog, we saw how two-factor authentication (2FA) secures access to cloud apps in hybrid AD. 2FA adds an extra level of security...

Three critical password management blunders that hackers regularly exploit and best practices to replace them
IT teams often shoulder a number of important security-related responsibilities. It’s essentially up to them to ensure organizations’ networks are secure. For most organizations, comprehensive password...
