Microsoft does not provide backup and recovery tools for its Office 365 services and has no plans to include them in the future. Some organizations use litigation holds as...

Monitoring user logon activity to identify compromised accounts
In a previous blog, we saw how ADAudit Plus’ user behavior analytics (UBA) capabilities allow administrators to monitor the file activity of users to identify anomalies. UBA in ADAudit...

Five reasons to choose Log360, part 2: Multi-environment support
In the previous post of this series, we looked at how easy it is to get Log360 up and running due to its various deployment...

Unmask malicious insiders with user behavior analytics
Insider threats are both the most successful way to exfiltrate sensitive business data and the hardest cyberattack to detect. This is because these attacks are carried out using...

Bringing SSO to hybrid Active Directory
As enterprises transition to a hybrid Active Directory (AD) environment, it’s important that they address identity management challenges. For example, employees often struggle to remember a different password for each...

Five reasons to choose Log360, part 1: User-friendly deployment and UI
SIEM solutions are a must-have in any organization’s security toolkit. They allow you to analyze events from your network, gain actionable insights into network activity,...

[Infographic] Top three approaches to dealing with account lockouts
In the previous blog of this series, “[Infographic]Three tips to simplify Active Directory compliance and auditing”, we discussed the tips and tricks to achieve compliance....

[Infographic]Three tips to simplify Active Directory compliance and auditing
In the previous blog of this series, “[Infographic] Still manually onboarding users into Active Directory? There’s a better way!“, we discussed the tips and tricks to...
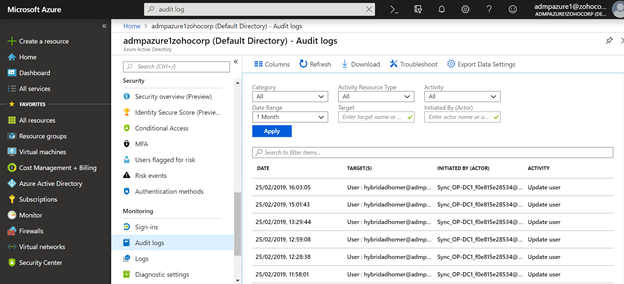
Detecting changes in privileged accounts in Azure AD
Monitoring and protecting privileged accounts is paramount because failure to do so can lead to loss or theft of sensitive information, or enable malware to...

