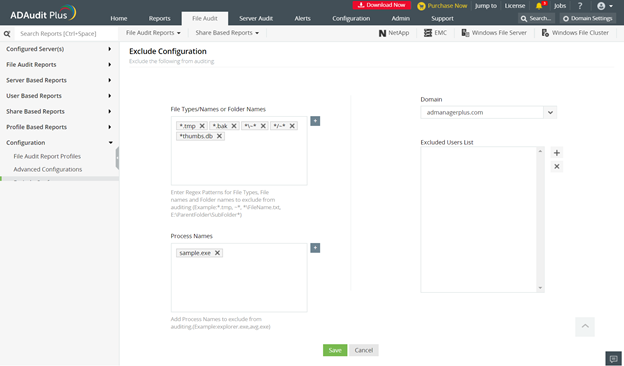
As an IT administrator, most of your tasks revolve around password management. With most organizations using Active Directory (AD) to manage their IT, a major...

Attend our Active Directory (AD) and IT security seminar from the comfort of your workplace
We’re thrilled to announce that our two-day Active Directory and IT security seminar will be available for online attendees. If you’ve always wanted to attend one of our seminars but haven’t been able...
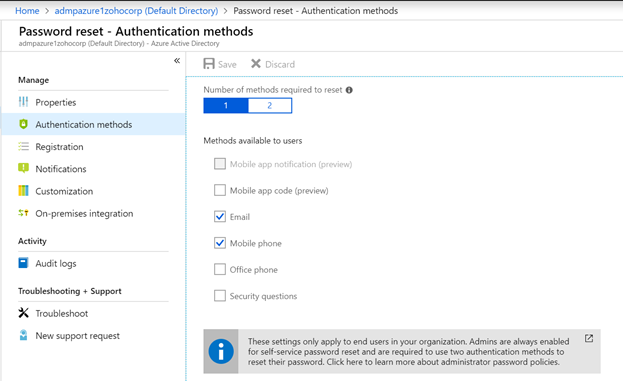
Self-service password reset in a hybrid Active Directory environment
Password reset tickets constitute a major chunk of the help desk ticket pile. Allowing users to reset their own passwords is a sure way of...

Gain insights into user behavior and detect insider threats
A whopping 60 percent of cyberattacks are caused by insiders. This could be due to excessive access privileges, an increasing number of devices with access...

[Free webinar] Bridging the gaps left by Active Directory password policies
IT administrators have tough jobs. From keeping the network running to servicing piles of support requests, their hands are always full. Even with so much on their...

Quick tips to ensure your Azure AD is safe from threats
Being the gatekeeper of Microsoft’s cloud solutions, Azure AD comes with a wide range of default security measures; these include insights on risky sign-ins and user accounts that...