Group Policy is undoubtedly one of the most powerful features of Active Directory. It renders administrators a secure and stable platform to establish and manage...

Preventing active password attacks using ADManager Plus’ Custom Reports
In this blog, we’ll discuss how Kerberos pre-authentication helps mitigate password attacks. We’ll also discuss how native tools fail to provide a list of user accounts that have disabled Kerberos pre-authentication, and how to detect and enable...

ADManager Plus’ Custom Reports, part 4: Creating custom LDAP query-based reports
In the first three parts of this blog series, we saw how ADManager Plus’ Custom Reports feature helps you create your own Active Directory reports...
The Microsoft Meltdown-Spectre patches…the real story
Microsoft has released patches for the Meltdown and Spectre CPU vulnerabilities, but you might find that you can’t install them or that they aren’t showing...

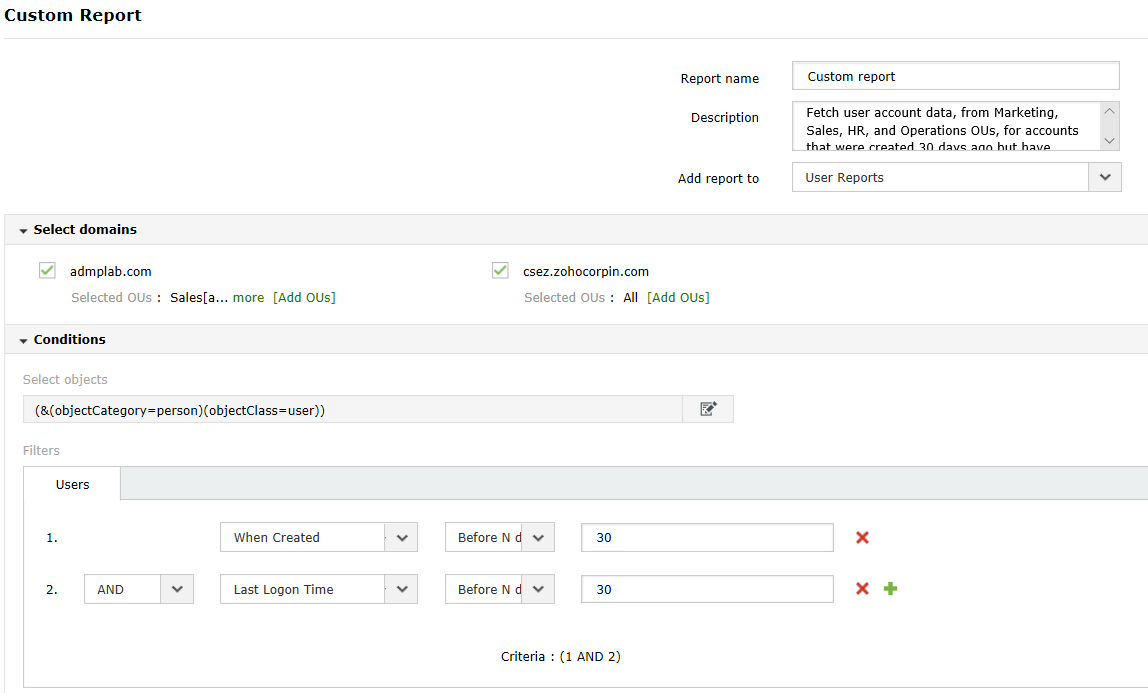
ADManager Plus Custom Reports, Part 1: Unrestricted reporting
This blog will discuss the constraints of prebuilt reports and how ADManager Plus helps overcome these limitations by providing unrestricted reporting capabilities. Prebuilt reports provided by...
A New Year’s resolution for Windows administrators
Did you make your personal New Year’s resolution? How about your professional one? With 2018 now here, I suggest that all Windows administrators make a...