HIPAA Security Rule updates: A proposed 15‑day patch mandate for critical vulnerabilities

Healthcare is facing a new urgency curve. Proposed updates to the HIPAA Security Rule for 2025 include a definitive patching clock: Remediate critical vulnerabilities within 15 calendar days of identifying the need—if a patch is available—or within 15 days of a patch becoming available. This means SecOps and ITOps teams managing clinical workstations, back-end servers, and multi-OS estates across hospitals and clinics might need to revise their patching cycles to stay compliant.
But first, a quick recap of how this standard has evolved:
Background of the HIPAA Security Rule
The last major revision of the HIPAA Security Rule was in 2013 with the HIPAA Omnibus Rule. This made business associates and covered entities directly liable for HIPAA compliance and increased the maximum fine from $25,000 per year to $1.5 million, escalating consequences for breaches due to noncompliance.
Over the past decade, healthcare IT has transformed. Devices now include workstations, tablets, phones, kiosks, BYODs, wearables, AR and VR devices, and medical IoT devices, expanding the attack surface and making healthcare a prime target for cyberattacks.
2024 saw the biggest ever attack impact in healthcare, with 14 data breaches affecting more than one million records and the largest healthcare breach of all time impacting over 190 million people.
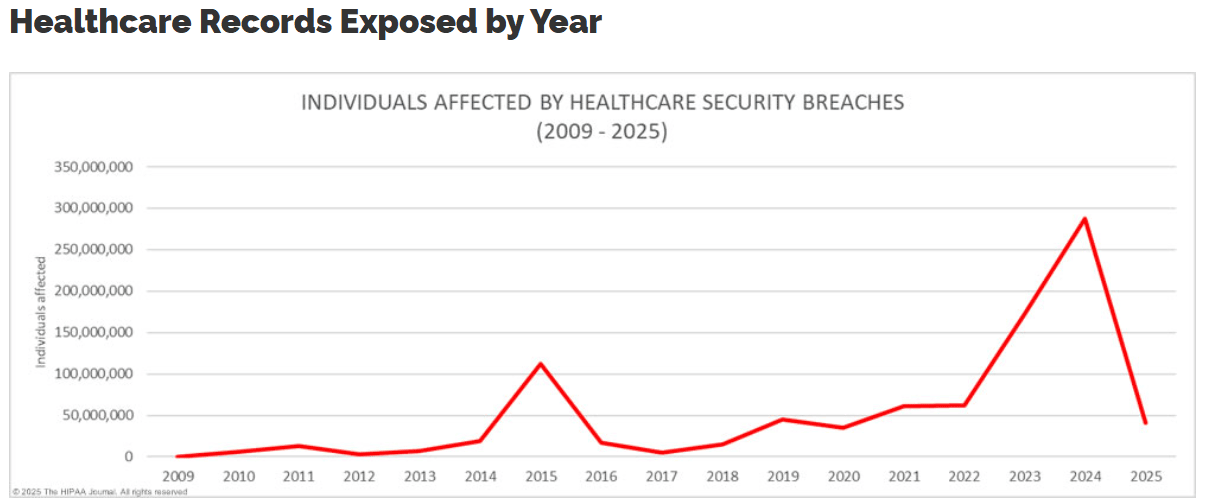
Source: The HIPAA Journal
The United States Department of Health and Human Services (HHS) has closely tracked the rise in healthcare attacks and conducted a landscape analysis to understand why healthcare remains an easy vector. It published its findings in a 2023 report, Hospital Cyber Resiliency Initiative Landscape Analysis, revealing the following:
Ransomware: The top threat
Ransomware has the highest impact due to the non-availability of services, thus affecting patient care.
Poor vulnerability assessments
Only 53% of hospitals have a documented response plan for vulnerabilities.
Only 20% of hospitals conduct advanced vulnerability tests.
Third-party gateways
46% of ransomware incidents involve third-party sources.
CISOs rank third-party risk as the third most important threat.
Antiquated assets
96% of hospitals use legacy systems with known vulnerabilities.
Rising cyber insurance premiums
Premiums increased 46% in 2021, leading some hospitals to self-insure.
The action plan? HHS released voluntary cybersecurity performance goals (CPGs), with a Healthcare Sector Cybersecurity concept paper highlighting that there would be changes to the HIPAA Security Rule to curb noncompliance further.
P.S. If you'd like to see a detailed evolution of the CPGs, you can check it out here.
A proposed update: A 15-day patch mandate
"Specifically, a reasonable and appropriate period of time to patch, update, or upgrade the configuration of a relevant electronic information system would be within 15 calendar days of identifying the need to address a critical risk where a patch, update, or upgrade is available; or, where a patch, update, or upgrade is not available, within 15 calendar days of a patch, update, or upgrade becoming available."
—HHS' Proposed Rule for the HIPAA Security Rule, Section 164.308(a)(4)(i)—Standard: Patch Management, page 970
The Proposed Rule is clear: Critical vulnerabilities must be patched within 15 calendar days of identifying them or within 15 days of a patch becoming available.
Let's just take a step back and see how realistic this proposed mandate is.
The healthcare device landscape is quite complex, with clinical workstations, critical servers, and shift-based devices running on multiple OSs, meaning that it might not be practical to take all devices all at once to patch them.
Imagine critical servers hosting important services like a PACS and EHRs that cannot afford to have downtime. The essential services must be supported on a failover server, then stopped on the group of servers that require patching. Once the patch is delivered, these services need to resume running on the primary servers. Additionally, critical patches usually require a reboot, but these servers cannot afford to be rebooted outside of their strict maintenance schedule because it would disrupt day-to-day patient care activities.
This is where it gets difficult to ride the compliance wave without disrupting care workflows. A large healthcare organization would follow a strict patch calendar tailored to support its diverse devices, as seen below.
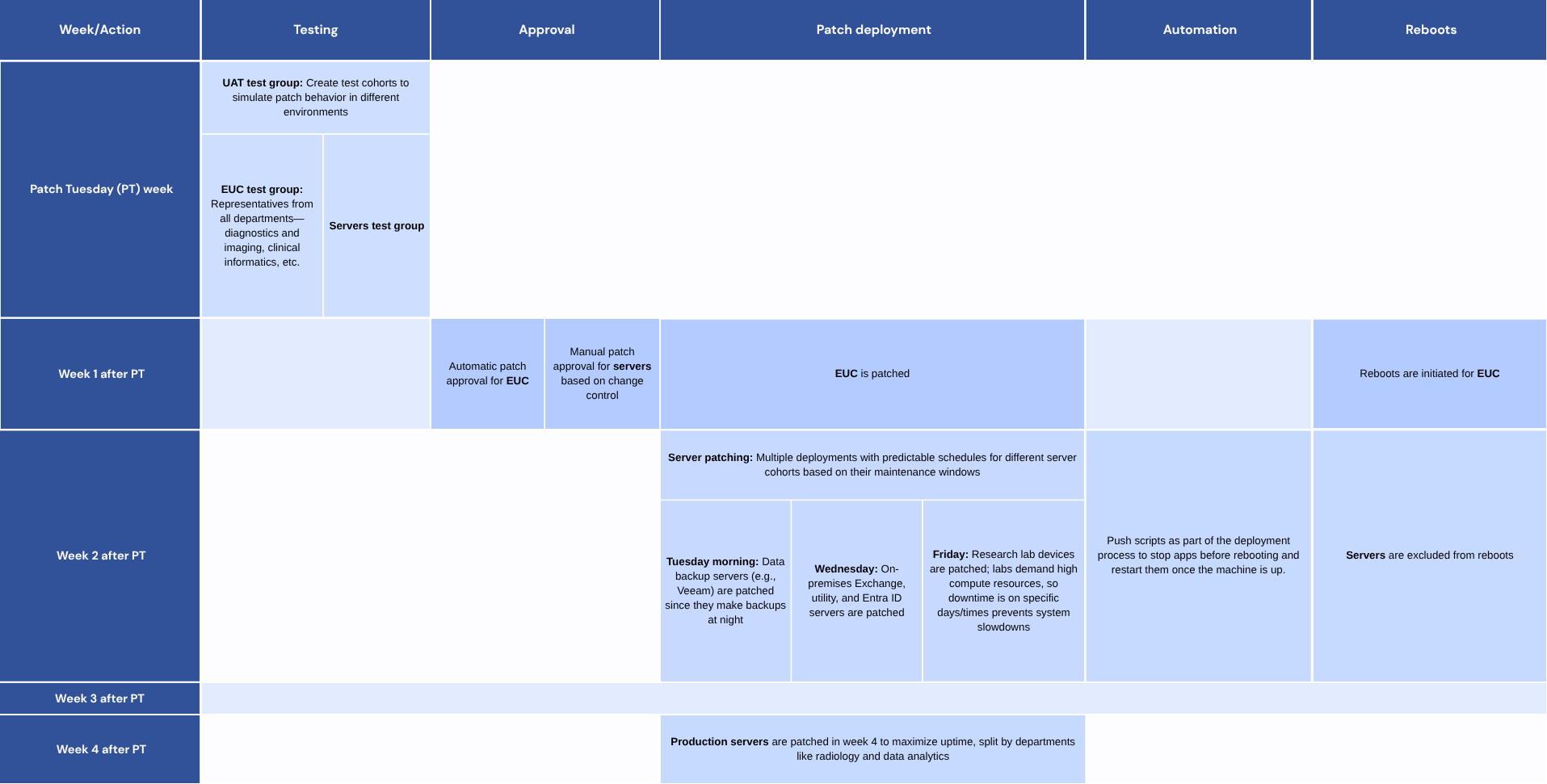
It is in such cases that the automation of patch cycles helps. Imagine having to wake up at odd times just to manually stop these services and then schedule reboots? This is exactly what a solution like ManageEngine Endpoint Central helps you resolve.
“For certain servers, I have to manually stop applications before rebooting, which means waking up at 5:30am once a month, which was a pain. But missing this means those servers stay vulnerable for longer. With Endpoint Central's patching workflows, I was able to schedule reboots and stop applications with its pre- and post-deployment functions.”
—Network system administrator at a community care organization based in Port Townsend, Washington, US
To learn more about how this Port-Townsend-based community care organization automated its patching schedule with extensive customization across its diverse device ecosystem, read the case study.
Independent validation to back these claims
We also commissioned Forrester, an independent research firm, to interview four of our largest enterprise customers across industry verticals to determine the Total Economic Impact™ of using Endpoint Central.
One of the most promising impacts that the customers mentioned was the savings they achieved with patch automation: a whopping $913,000 reduction in costs and a 95% reduction in time.
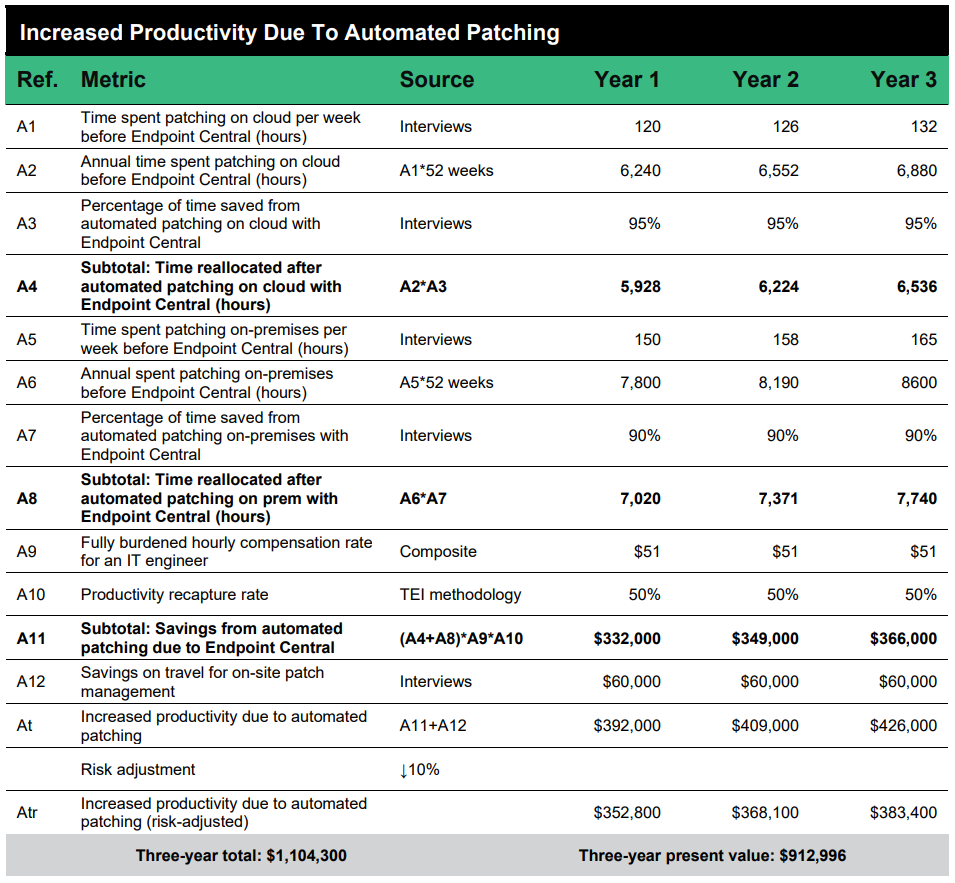
To get the details on Endpoint Central's Total Economic Impact, access the report here.
Hit the 15-day mark with Endpoint Central
In fact, we've seen customers cut down their patch cycles from months to just 14 days, even before the HIPAA Security Rule updates were a thing.
"We went from having a 90-day lead time to 14 days for updating patches and keeping patches up to date on our endpoints with Endpoint Central."
—Director of IT security at a large hospital in New Jersey, US
How did they do that? The answer is automation. With the healthcare IT ecosystem containing a multitude of devices (such as clinical workstations, critical servers, and shift-based devices) running on multiple OSs, the 15-day mark is quite hard to achieve. That is where a solution like Endpoint Central can help with cutting down on the patch time with the following capabilities:
Test and stage patches by the device type or group before broad rollouts.
Automate reboots by the shift schedule to avoid clinical downtime.
Pause or delay patches and reboots for critical care scenarios.
Patch Windows, macOS, Linux, and over 850 third‑party apps from one console.
Auto‑map CVE IDs to available patches to accelerate remediation.
Patch critical servers without fixed patching schedules on demand via the self-service portal.
Want to learn in detail how our capabilities can help you meet the proposed HIPAA 15-day patch mandate? Read here.