ManageEngine is participating in GISEC (Gulf Information Security Exhibition and Conference) next week. We would love to see you there! GISEC offers cutting-edge IT solutions...
Search results for: Firewall Analyzer

ManageEngine in the News!
A round up of the global coverage ManageEngine has received in the last three weeks. Privileged Password Management Software for MSP’s: At Infosecurity Europe, ManageEngine launched the industry-first...

$45 million ATM heist turns focus again on insider threats, controlling privileged access!
New wave of cyber-attacks on banks lend credence to the belief that insider threat is getting complex and cyber-criminals are increasingly targeting to siphon-off the...
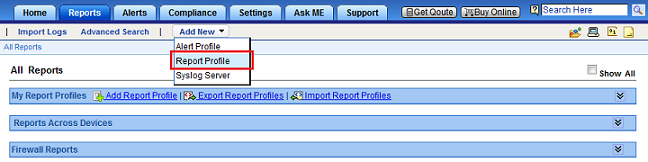
How companies can implement Internet fair use policy for corporate users?
Internet fair use policy or acceptable use policy defines the appropriate Internet usage behavior expected from employees in their workplace. The policy aims to protect the employees...
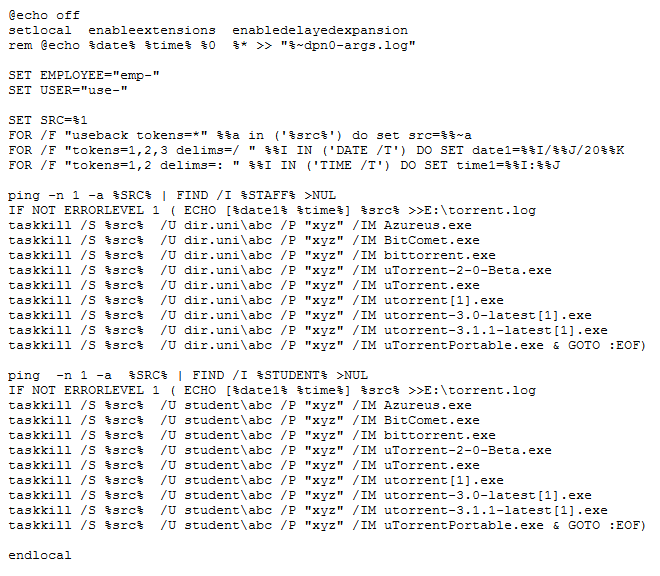
Security Event Management: Real-time Alerts and Instant Remediation
You may come across a situation, where there was a virus attack on you IT network. In another situation some of the corporate users may...

Guest Post: How ‘Credit Union of Denver’ secures its network and provides business continuity to their customers…cost-effectively!
By Benjamin Shumaker, Vice President of IT/ISO at Credit Union of Denver ManageEngine EventLog Analyzer and ManageEngine Firewall Analyzer offers a huge set of features,...
Bridge the gap between IT Operations & IT Security
Traditionally, IT operations and IT Security have remained at loggerheads. IT operations team is tasked with the responsibility of carrying out the the day-to-day activities,...
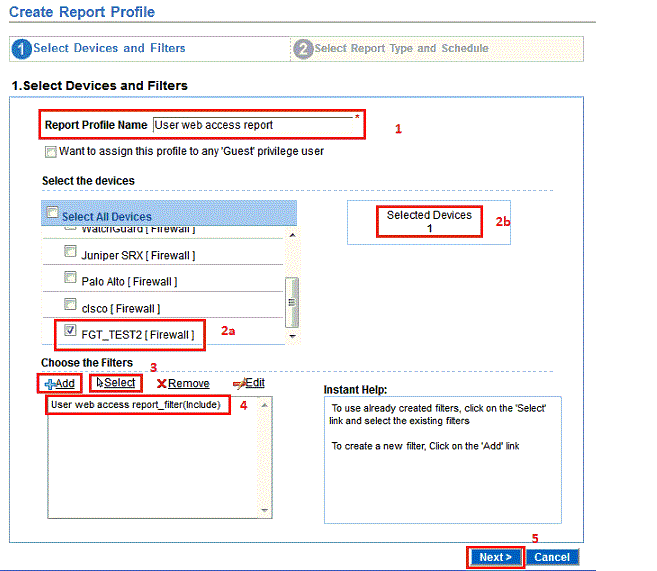
Non-intrusive & Real-time Monitoring of Corporate Users Internet Activity – Part IV
In continuation to our earlier postsNon-intrusive & Real-time Monitoring of Corporate Users’ Internet Activity Part – I,Part – II, and Part – III,we will now show...
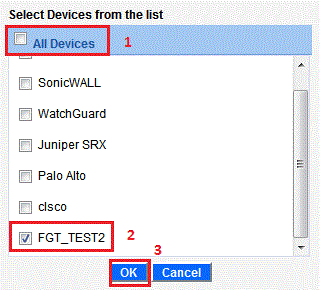
Non-intrusive & Real-time Monitoring of Corporate Users Internet Activity – Part III
In continuation to our earlier post Non-intrusive & Real-time Monitoring of Corporate Users’ Internet Activity Part – I and Part – II, we will now...
