In continuation to our earlier post Monitoring Corporate Users’ Internet Activity, we will now show you how to monitor corporate users’ Internet activity with Firewall...
Search results for: Firewall Analyzer
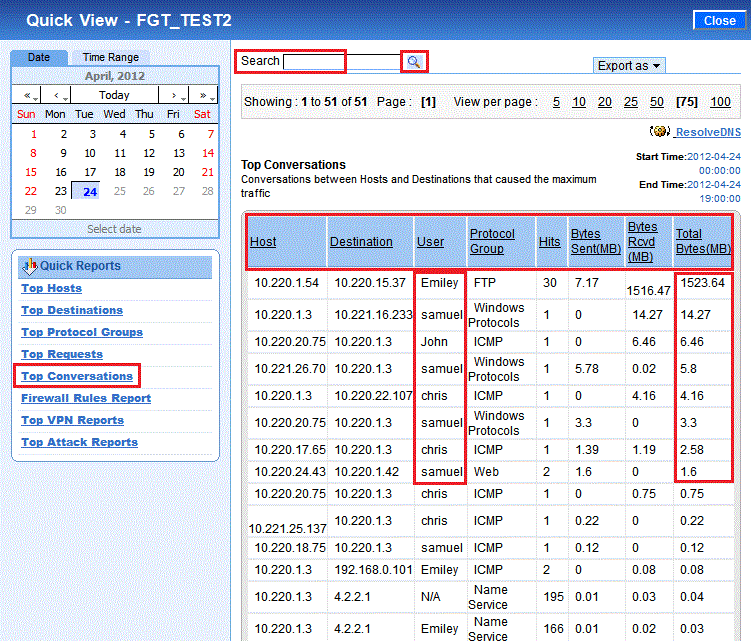
Non-intrusive & Real-time Monitoring of Corporate Users Internet Activity – Part I
Like unrestricted privileges to administrative users in a network (PUMA), uncontrolled web access in companies has its own set of problems. Irresponsible Internet usage tends...
Unauthorized access and use of protected health information is the most profitable crime in the USA: Are you fully prepared to combat? [Part-2]
In the previous post , we analyzed the magnitude of medicare fraud, protected health information stakeholders and their responsibilities. Let us now examine the causes...
Cyber-attack on Zappos: Information Security Lessons for Enterprises [Part-5]
In the previous four posts, we analyzed the causes for security incidents. We discussed how lack of internal controls, access restrictions, centralized management, accountability, strong...
Performance based IT Shop Part 3: Architect Level
IT problems usually need to be handled by the network engineer or Systems Engineer. These people are the craftsman of the IT trade. However, the...
DNS Network Hacking on UK sites
It is one of the most popular technology news sites in UK and worldwide, The Register. The first news I read was “The Register Hacked”, posted...
Performance based IT Shop Part 2
Not all IT problems come under the domain of the network engineer. In my previous Blog, I talked about IT shops having a hodge-podge set...
Lessons from Sony PSN breach
The breach at Sony Play Station Network (PSN) breach creates a lot of doubts in the IT Security manager’s mind. We can take our lessons...
Nominate ManageEngine for WindowsITPro 2010 Community Choice Awards
WindowsITPro has recently opened the nominations for 2010 Community Choice Awards. We request your support to nominate ManageEngine Products for the awards. Following is the...