In what is perhaps the largest data breach in Brazil in recent times, a hacker group known as John Carter has stolen over 80,000 users’ personal...
Search results for: 7 problem management
How to overcome repeat IT requests
When you’re in IT, you see it all. Complicated issues, like that one Windows update that just won’t install, and quick fixes that you could do in...

Five worthy reads: Revolutionizing IT with artificial intelligence
Five worthy reads is a regular column on five noteworthy items we’ve discovered while researching trending and timeless topics. This week, we highlight the growing...

Lessons from data breaches that every enterprise should take to heart
“Four years later, Yahoo still doesn’t know how 3 billion accounts were hacked” read TechCrunch on November 8, 2017. The 2013 Yahoo breach is still as big...

Five worthy reads: Spectre, Meltdown, and chips that ooze data
Five worthy reads is a regular column on five noteworthy items we’ve discovered while researching trending and timeless topics. This week, we cover the Spectre and...

Let’s talk about STIX, TAXII, and threat intelligence
In terms of collaboration, Structured Threat Information eXpression (STIX) and Trusted Automated eXchange of Indicator Information (TAXII) represent a revolution in the security industry. These protocols transformed...

Training: Join us to learn best practices on applications performance monitoring
In an era fueled by innovation, it’s crucial for your organization to embrace the idea that customer satisfaction is the catalyst for commercial success....

Integrate Desktop Central with Zendesk to boost your productivity
With a unified endpoint management (UEM) solution, you can keep your IT assets and network resources secure while still providing the freedom your users need to creatively solve business problems. Imagine...
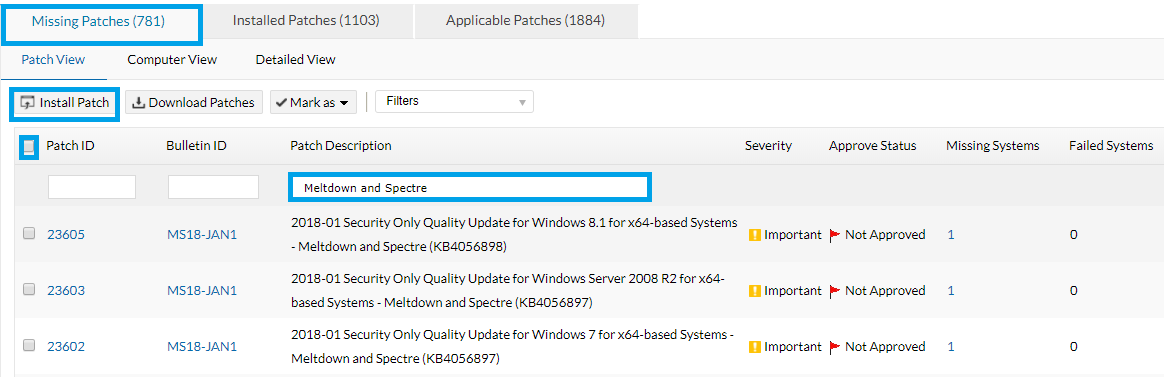
Meltdown and Spectre: Battling the bugs in Intel, AMD, and ARM processors
In preparing for GDPR compliance, you may have heard of Meltdown and Spectre—two new hardware bugs that exist in Intel, AMD, and ARM processors and are capable of...
