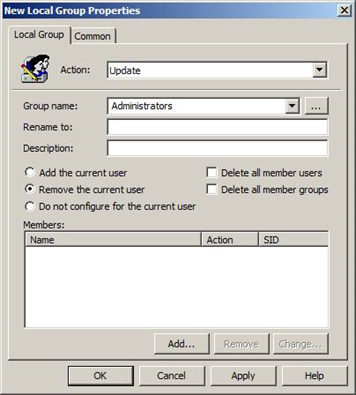
If you have a long list of users with administrative rights, there’s a good chance you’ve offered excessive amount of privilege to accounts that don’t...
Search results for: 7 problem management

Applications Manager: A game changer for multiple businesses
To retain a competitive advantage in today’s fast-paced digital market, organizations need to focus on their application stack. Error-prone or bug-ridden applications may deter potential customers from visiting a site...
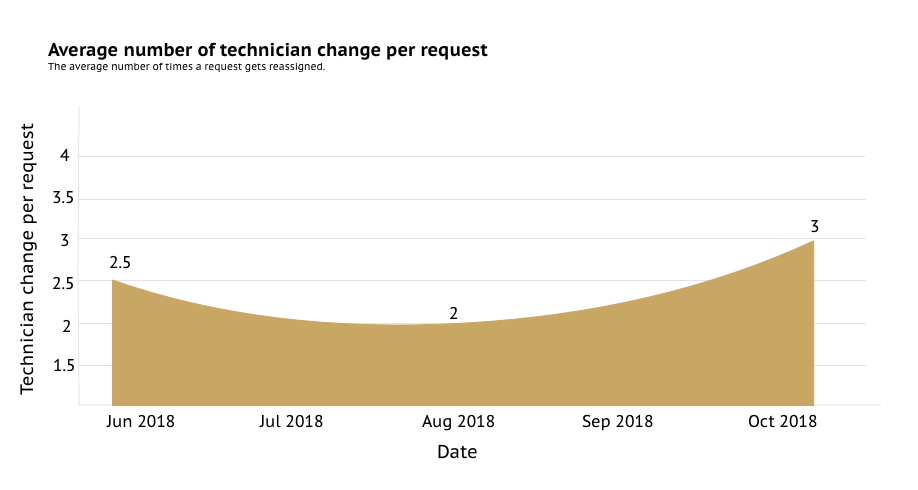
Advanced analytics for ServiceDesk Plus’ ticket history, projects, and knowledge base modules
We’re happy to announce the release of advanced analytics for three more ServiceDesk Plus modules: Request transition history—Visualize the complete request timeline, from ticket creation to ticket...

Conquer it with correlation—Part 2: The data breach
In my previous post, we looked at how event correlation can be used to deal with advanced persistent threats (APTs). The thing is, an APT...

Industry best practices for endpoint security
Lately, hackers on the lookout for vulnerable systems have kept the IT industry busy. While various OS and software vendors strive to keep their users’ data intact by...

Webinar: Learn a simple three-step approach to tackling threats
Technology has a lot to offer, from streamlining your business processes to protecting your network, but with all the advantages comes the risk of cyberthreats. Cybercriminals are always developing new...

Prevent Man-in-the-Disk attacks using the right mobile security procedures
Organizations that offer employees the freedom of mobility gain some advantages, which can include better productivity or saving workplace costs by allowing employees to work from home, but doing so comes...

ITOM seminar in Australia: Attend. Learn. Leverage.
The biggest challenge enterprises face today is embracing new technologies and using them to effectively meet their business requirements. In the past, technology only existed on-premises for enterprises, but now, almost 93...

Linux security and patching: Are you as safe as you think you are?
A common question posed by enterprises when it comes to defending against cyberthreats is “Which operating system is most secure?” There are only a few...