Privileged password management has now emerged a key aspect of IT management. With ever-increasing number of privileged identities in shared environment, protecting the administrative passwords...
Do you still keep your administrative passwords in text files and spread sheets?
Modern IT and other enterprises are heavily dependent on servers, databases, network devices, security infrastructure and other software applications for their day-to-day operations. These infrastructure...
Don’t let your administrative passwords become Pulcinella’s Secrets!
If you wonder what the phrase ‘Pulcinella’s Secret’ means, let me start with explaining that: Pulcinella is a popular comic character in Commedia dell’Arte, a...
Lessons from Sony PSN breach
The breach at Sony Play Station Network (PSN) breach creates a lot of doubts in the IT Security manager’s mind. We can take our lessons...
Is PCI DSS enforcement is only banking companies?
No, PCI DSS compliance may not be limited to Banking and Payment Card companies. It may be enforced for any company handling customer credit card...
Brute force attacks could crack 20% of the passwords of government agencies: Audit Report
An audit conducted by the Australian National Audit Office (ANAO), has concluded that brute force attacks could result in compromising about 20 per cent of...
ManageEngine – The Virtual Fortress for Your Enterprise!
Today’s enterprises are facing unprecedented security threats. As organizations embrace new technologies, newer threats keep pace. Safeguarding the enterprise from evolving, sophisticated threats is the...
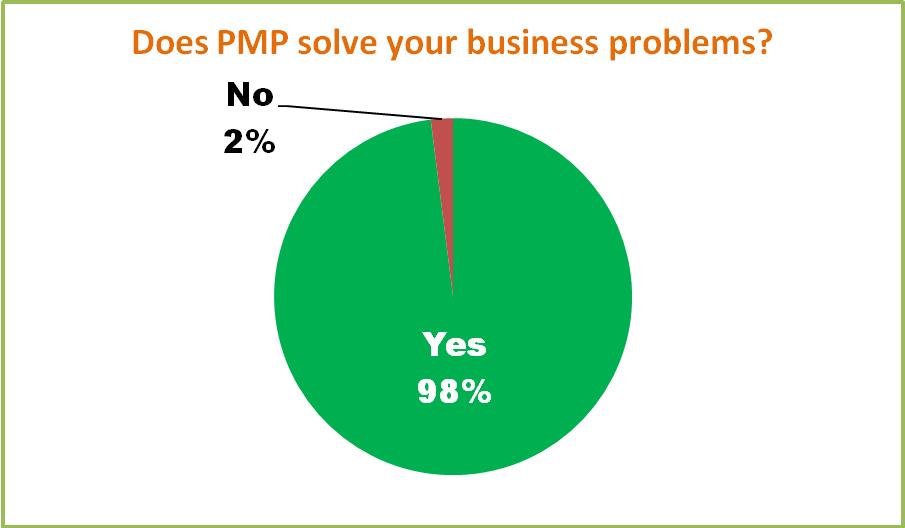
98% of the customers repose trust in Password Manager Pro
After purchasing a product – be it a domestic commodity or a software, quite often, we might end up feeling that the product is just...
2011: A New Year’s resolution to protect your data, sensitive information & business!
Bidding adieu to 2010, the old year and a brand new 2011 is at the doorsteps! It is again that time of the year when...

