In the previous post, we had highlighted the casual manner in which privileged passwords are shared among various works groups in enterprises. Let us now...
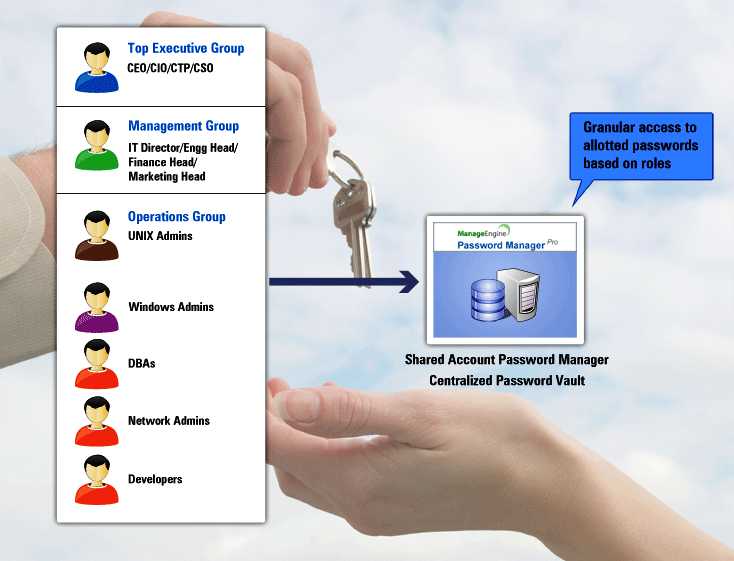
How do you share privileged passwords in your enterprise? [Part-1]
Assume that you are an IT administrator managing servers, databases, network devices and numerous other IT applications. All these resources are accessed/controlled through administrative passwords...
IT’s New Reality
Jason Hiner over at TechRepublic wrote a blog the other day entitled What the IT department will look like in 2015. He’s got some interesting...
The price for information security shortcomings …
Just about four weeks back, the security incident in that company came to light. Today, the company has filed for bankruptcy. The security breach has...
A Tale of Two Realities: IT Managers, What’s Keeping You from Adopting New Technologies?
I had a lot of fun talking to Michael Dortch recently. For those of you who don’t know Michael, he’s a charismatic IT analyst who...
Perils of ‘Static’ Windows Service Accounts
Windows Service Accounts, used by the system programs to run application software services or processes often possess higher or even excessive privileges than normal user...
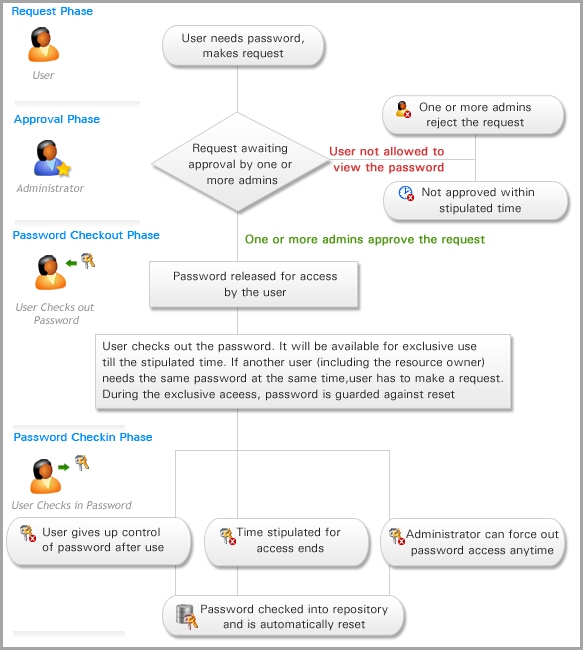
Allowing temporary access to sensitive IT resources
Assume the scenario below: You administer a sensitive IT resource – a database in production network containing important data. An emergency troubleshooting situation arises. A...

Deprovisioning administrative access: How careful are you?
FBI investigation on Shionogi security incident reveals the involvement of a former employee Lord Tennyson’s immortal words “Men may come and men may go, But...
An automated solution to enforce IT policy on standard password practices
Growing instances of information security incidents have forced IT enterprises to put an effective IT policy in place. All such policies stress three essentials, among...

