E-commerce continues to be a game changer in the retail industry. But the change isn’t always for the better. Along with its promise of enormous...

Braving the cyberattack storm: a refresher on security essentials.
This has certainly been a busy summer for hackers worldwide. First, it was the U.S. federal agencies. This recent hack, aimed at the Office of...

Success Story: A Leading Bank in Netherlands Centrally Controls Privileged Access with Password Manager Pro
Against the backdrop of the ever-increasing cyber attacks, government and industry regulations prescribe stringent security measures for banking and financial institutions to safeguard customer data....
Combat Identity Thefts and Advanced Cyber Threats with Password Manager Pro Enterprise Edition
No one is safe out on the virtual streets of cyber world, and security breaches surface quite frequently to remind us of the same. Lately, the...

Microsoft LAPS: Honest Obituary or False Eulogy to the Death of Passwords?
The famous Latin phrase De mortuis nil nisi bonum (Of the dead, nothing unless good) came to mind last week when Microsoft announced the release of LAPS (Local Administrator Password...
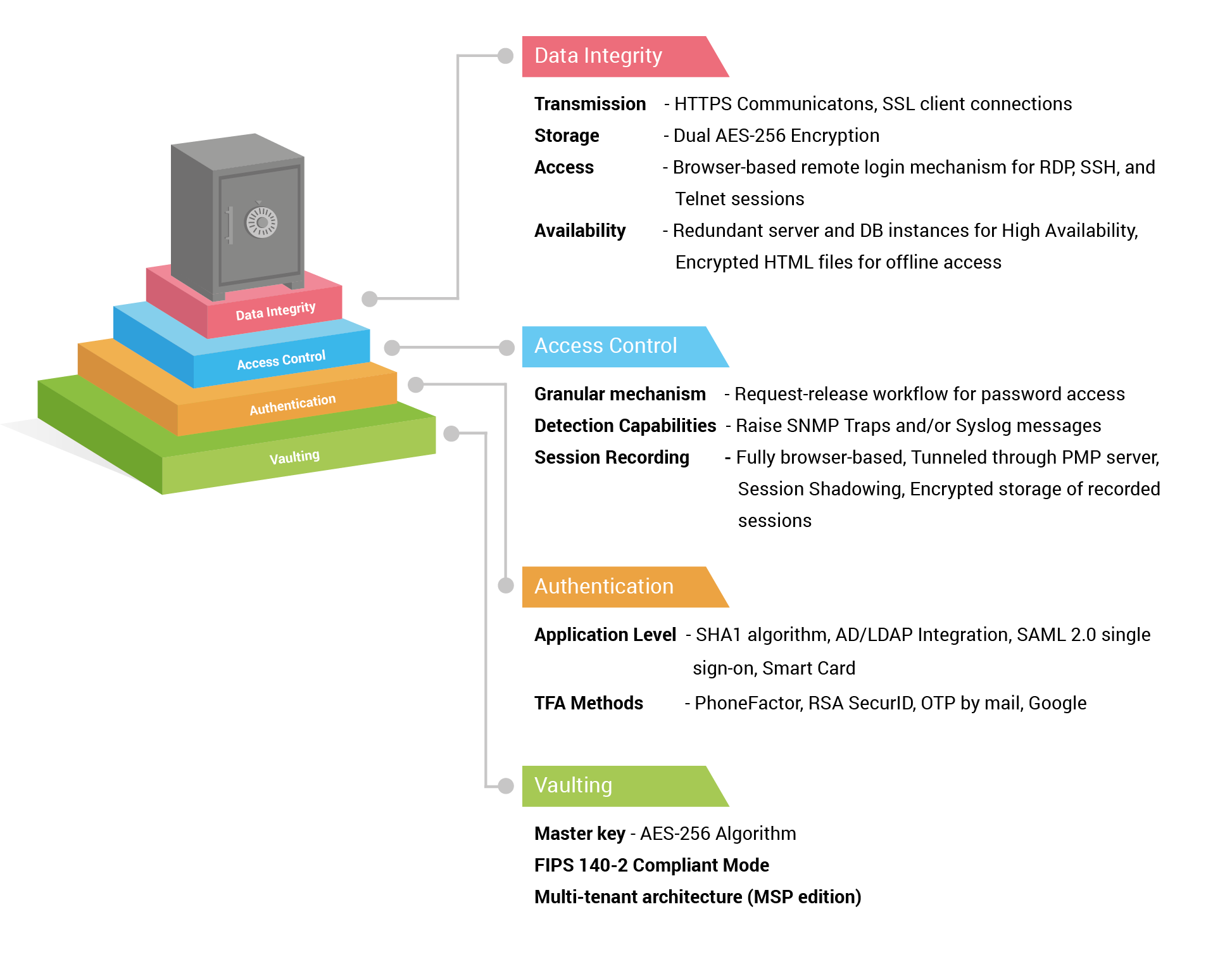
How Secure Is Password Manager Pro?
Gone are the days when all you needed was a strong password to guard your data. Now, we live in an era where you not...

Hacking Hospitality: How to Fight the Cyber-criminals Targeting Business Travelers
Traditionally, financial institutions have remained the top targets of cyber-criminals across the globe. Of late, hackers are eyeing so many other things that, one would normally...
Protective, GPG13-Compliant Monitoring Using EventLog Analyzer
The journey to a thousand IT problems begins with a single compliance lapse. Yes, this is the first time you are hearing it! So, tell...
Jimmy Kimmel Sheds Light on Password Security
Ace comedian Jimmy Kimmel, who is known for tickling our funny bones through his television shows, tried a social engineering experiment last week. In the...

