IT security managers lay a lot of emphasis on conducting log forensics investigations. According to the SANS 2013 Digital Forensics Survey, 57% of the respondents...

8 Log Management Habits of Highly Effective IT Security Managers
In today’s business environment, data is the source that drives organizations in the proper direction. Data enables planning, forecasting, and strategy. For example, retailers rely...

Middle Eastern & African IT Professionals Often Pass On Secure Password Management
The GITEX Technology Week in Dubai gave ManageEngine the opportunity to interact with a cross-section of IT professionals from the Middle East and Africa, and we found that password...
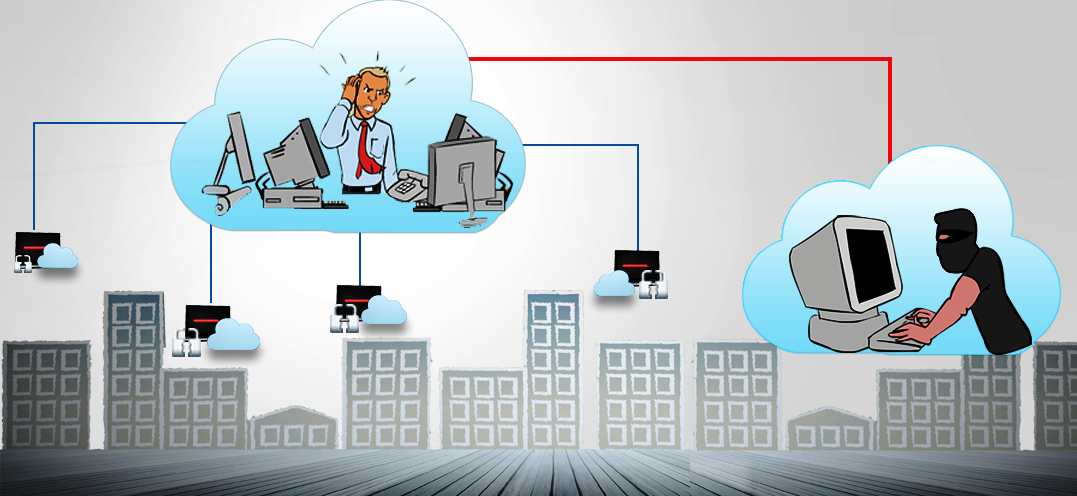
Code Spaces AWS Security Breach: A Sad Reminder of the Importance of Cloud Environment Password Management
In the recently concluded Black Hat USA, 2014, one of the topics that drew much attention was the session on the pitfalls in cloud environment...

Combat Advanced Cyber Attacks With Shared Security Intelligence
(Originally published in Cyber Defense Magazine, Black Hat special edition) In this information age, even the mightiest of enterprises and governments across the globe are worried...

Passwords, King of Authentication: Long Live the King!
This post is a reproduction of an article I wrote that was originally published in Business Computing World. “When you play the Game of Thrones, you...

Why MSPs Should Take Extra Care in Managing Client Passwords
Passwords on spreadsheets put client networks at risk, along with Managed IT service providers’ credibility and trustworthiness. Managed IT Service Providers (MSPs) deliver a variety of...
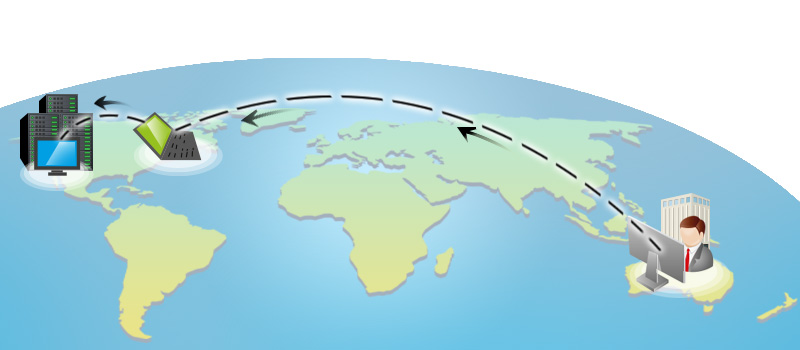
Fully Controlled and Closely Monitored Remote Access, a Critical Aspect of DCIM
Without proper data center remote access management, administrators invite security issues and waste time. With more organizations adopting cloud computing and virtualization, data center operations...

The Heartbleed Bug: How to Mitigate Risks with Better Password Management
– – – – – – – – – – – – – – – – – – – – – – – – –...

