A catastrophic flaw in Linux sudo command with a simple fix using Desktop Central
A critical vulnerability in sudo has been disclosed, that when exploited, enables users to bypass security restrictions and execute commands as the root user. This security flaw has to be swiftly remediated as sudo is one of the most integral and commonly used functionalities in Linux operating systems.
Background on sudo
Sudo stands for "Super User Do." In order to run a command with elevated privileges like that of a super user, the word "sudo" is typically added as a prefix to that command. This makes sudo an effective security and management utility as it enables multiple users with proper credentials to make decisions at an administrative level.
Though there can be multiple users with elevated privileges, Linux still offers good security, as each user and their qualifications are meticulously managed. This rigidity also applies to the sudo command; only the users listed in the file /etc/sudoers are granted permission to execute sudo commands. Furthermore, these users are categorized into three levels of access:
1. The trusted few users who have permission to execute commands as all users including root users.
2. The users who are given permission to execute commands as all users except the root user.
3. The users who are given permission to execute commands as other specific users only.
Who can exploit this vulnerability using sudo?
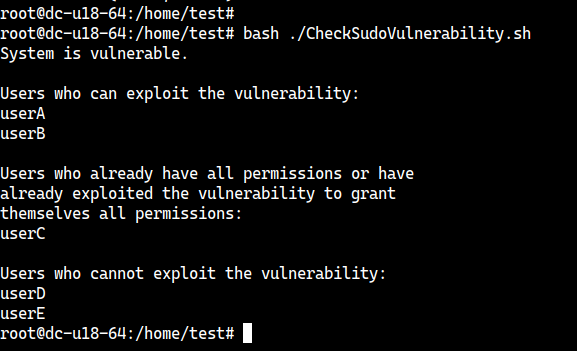
This vulnerability (CVE-2019-14287) can only be exploited by users included in the first two categories mentioned above. This is because in the /etc/sudoers file, in the RunAs specifications in the first two sections, the ALL keyword is mentioned within the brackets and after the equal sign.
As shown below in the /etc/sudoers file, for userA and userB (after the equal sign and within the brackets), the ALL keyword is mentioned first, and for userD and userE, it's not.
In this scenario, userA and userB have sufficient sudo privileges but not root access. They can exploit the vulnerability and elevate their privileges to that of userC, which does include root access. A summary of each user and their ability to exploit the vulnerability is shown below.
How exactly does the attack occur?
Users with sudo privileges would have to provide their own username and password to be given permission to carry out sudo commands. However, among the users in the first two levels of access, anyone with hostile intentions can target any Linux endpoint and hijack complete control just by entering the username as:
• -u# -1 id -u
OR
• -u# 4294967295 id -u
During the process of converting user IDs into usernames, the -1 or 4294967295 are mistranslated as 0, which is the user ID of the root user. Additionally, the -u format isn't recognized in the password database, meaning dynamic password authentication also doesn't happen.
As you can tell, attackers will be able to easily exploit this vulnerability. Fortunately for Linux administrators, fixing it is easy, too!
What can you do about this vulnerability?
For this vulnerability, discovered by Joe Vennix of Apple Information Security, as a precautionary measure, a script that can detect any intentional or unintentional ALL keywords mentioned in the levels of access in the /etc/sudoers file can be deployed manually using the script or via Desktop Central.
As shown below, in the Desktop Central console, if the vulnerability has not affected the system, the script configuration will be a successfully executed, however if the vulnerability has already been exploited, the execution will fail.
If the vulnerability has been exploited, Desktop Central's robust patch management feature (also available as stand alone solution: Patch Manager Plus) can quickly dispatch the most current sudo version and other relevant patches to Ubuntu and Debian endpoints.
Updates will also be made available for deployment to other major distributions such as RedHat and CentOS as soon as they're released by the associated vendors.
Get started on securing your systems with Desktop Central.