Cyberattacks are fast becoming a part of our daily lives. Multiple sources such as Norton Security and Forbes suggest that since the pandemic, attacks are not only...
Search results for: shadow IT
Why companies need URL filtering for enhanced cloud protection
The cloud landscape is rife with unsafe URLs and inappropriate content. This—coupled with the accelerated adoption of cloud applications in the workplace—has created an urgent...

Tackling your network security challenges using ManageEngine ITOM solutions
Network security management typically entails end-to-end management of the entire network security infrastructure of an enterprise. However, in this rapidly changing security ecosystem, there’s an...

Curtail security exploits in applications and fortify your remote endpoints
The trend of working from home has hit the ground running, and businesses have turned to strategies and tools that will ensure a no-plummet productive environment. There...

Streamline application delivery with Desktop Central’s self-service portal
From automated airport check-in systems to advanced mobile banking platforms, self-help initiatives are spreading like wildfire. Additionally, self-help has become crucial in the workplace, where...
Webinar: Top 7 priorities for service desk managers in 2018
With chatbots enabling self-service, artificial intelligence playing a big role in building cognitive automation, and predictive analytics helping with decision-making, there is no denying the...

This week’s five: Gear up for the future of IT
This week’s five is a weekly column on five recent reads from all over the web. This week, we’ll talk about the future of IT...
ITAM best practice 1: Build your inventory using multiple discovery sources
The first of our best practice series on IT Asset Management will show you how to build your inventory using multiple discovery sources. The goal is to identify...
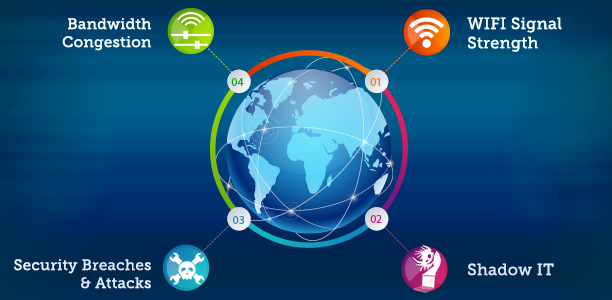
Four Things to Consider When Making Your Enterprise Network Mobile Ready
Mobile-device adoption for day-to-day business activities has been on the rise thanks to BYOD, smartphone proliferation and high-speed wireless networks. According to ABI Research, the...
