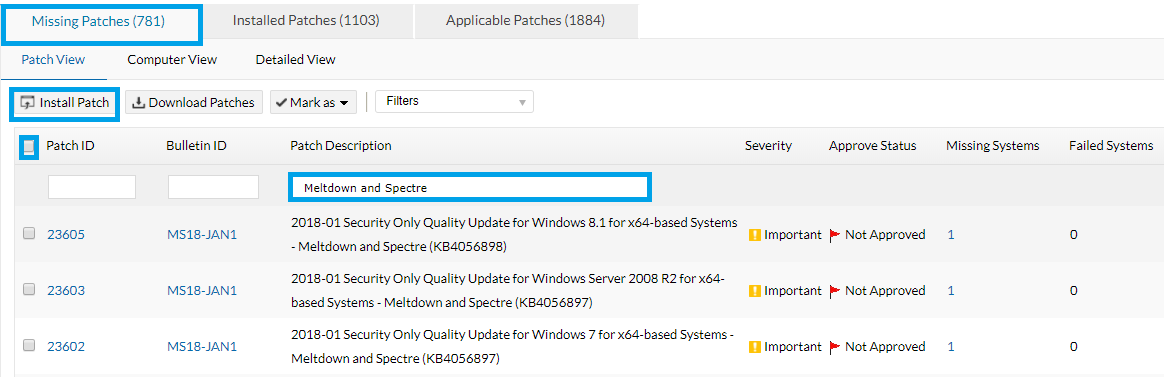
In preparing for GDPR compliance, you may have heard of Meltdown and Spectre—two new hardware bugs that exist in Intel, AMD, and ARM processors and are capable of...
Search results for: GDPR
Free webinar: Top five critical alerts you need for IT security
2018 promises to be another big year for IT security, with experts predicting even more large scale cyber attacks over the next 12 months. In light of the...

ManageEngine: Resumen del año 2017
Para ManageEngine, 2017 puede definirse en gran medida por una de nuestras citas favoritas de C.S. Lewis: “Tu nunca eres demasiado viejo para establecer otro...
2017 IT recap—Things we learned
2017 was full of new information, new technologies, and lessons learned. As I toured the world again, I was reminded of the commonality that the...

ManageEngine: 2017 at a glance
For ManageEngine, 2017 can be largely defined by one of our favorite C.S. Lewis quotes: “You are never too old to set another goal, or to...
How SIEM can help with auditing and compliance
Recent cyber breaches and tighter compliance regulations are pushing businesses to invest more heavily in IT security. You and your organization may very well be in the process of assessing your...
Active Directory from A to Z!
Now that summer is over, we are delivering a variety of webinars all geared to increase the security, productivity, and overall stability of your Active...
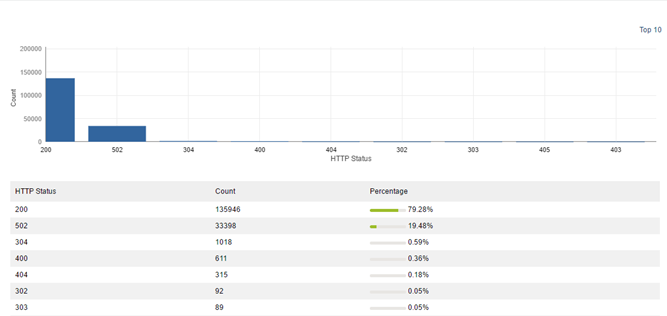
Log management and SIEM fundamentals: Comprehensive log collection and auditing
The first step in SIEM is collecting log data. Log data, as we saw in part 1, is what drives any SIEM solution. A SIEM...