A highly functional IT network is the basis of any successful modern business, and for effective operations, organizations must monitor the health and availability of...
Search results for: 7 problem management

6 top risk factors to triage vulnerabilities effectively
Common Vulnerability Scoring System (CVSS) scores have been viewed as the de facto measure to prioritize vulnerabilities. Vulnerabilities are assigned CVSS scores ranging from one...

Dealing with data glut: Why ROT data is an issue, and how to manage it
“Unstructured data accounts for as much as 80 percent of an organization’s data footprint.” – Gartner As file storage grows rapidly year after year, new...
Domain controller patch alert! Vulnerability grants domain admin access in 10 seconds
A critical Active Directory vulnerability (CVE-2020-1472) has been making headlines for being the most notorious elevation of privilege bug because it can affect all computers...

System extensions are replacing macOS kernel extensions. How will this affect you?
From the outset, Apple has been keen to protect user privacy and security, and deprecating kernel extensions is one of the company’s latest moves towards...

How to stop rampant, poor password practices
We’ve all heard about the consequences of poor password practices again and again. Yet, users still reuse their passwords for multiple accounts, create weak passwords,...

How to monitor IIS effectively
Microsoft Internet Information Services (IIS) is a popular web server for hosting web applications and is widely used in many sectors, such as healthcare, banking,...
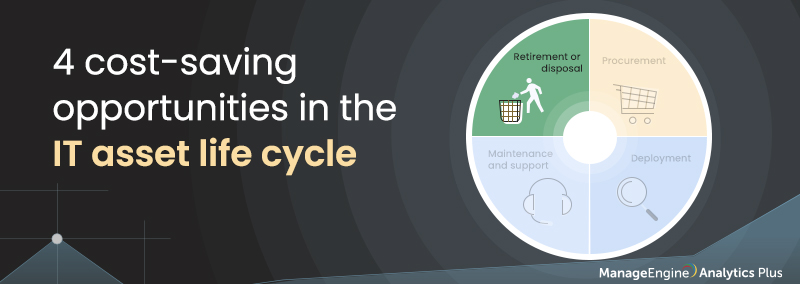
4 ways to save on IT costs in the asset life cycle [Part 4: Retirement and disposal]
Welcome back to the final part of our four-part blog series on saving on IT costs in the asset life cycle. In the last...

Monitoring NGINX with Applications Manager
NGINX is open-source software that started out as a web server and now provides various solutions such as web serving, reverse proxying, caching, load balancing,...
