By Benjamin Shumaker, Vice President of IT/ISO at Credit Union of Denver ManageEngine EventLog Analyzer and ManageEngine Firewall Analyzer offers a huge set of features,...
Bridge the gap between IT Operations & IT Security
Traditionally, IT operations and IT Security have remained at loggerheads. IT operations team is tasked with the responsibility of carrying out the the day-to-day activities,...
Non-intrusive & Real-time Monitoring of Corporate Users Internet Activity – Part IV
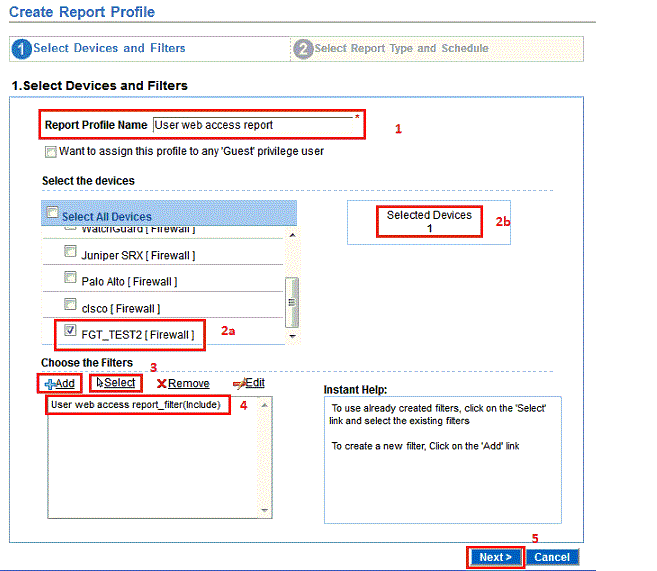
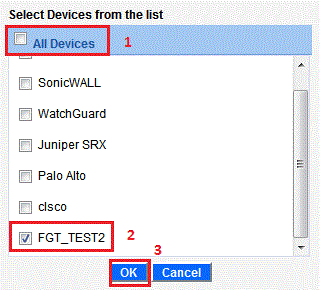
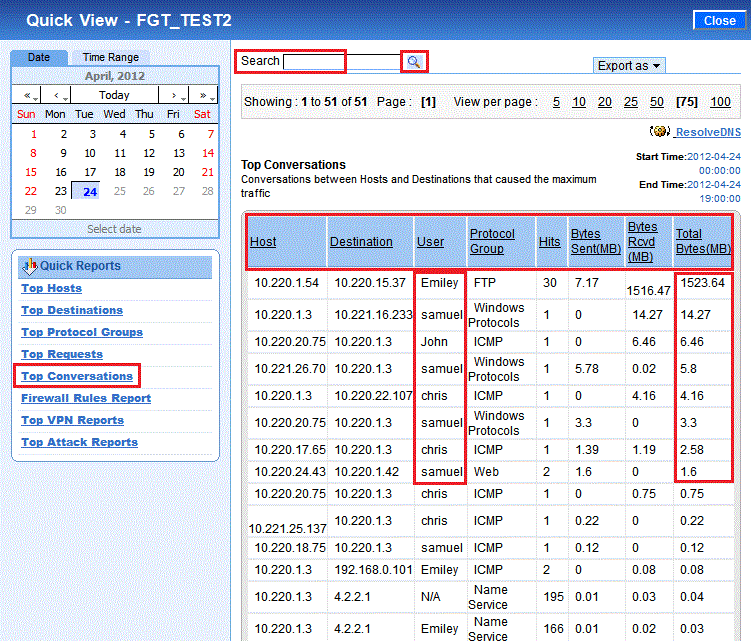
In continuation to our earlier postsNon-intrusive & Real-time Monitoring of Corporate Users’ Internet Activity Part – I,Part – II, and Part – III,we will now show...
Non-intrusive & Real-time Monitoring of Corporate Users Internet Activity – Part III
In continuation to our earlier post Non-intrusive & Real-time Monitoring of Corporate Users’ Internet Activity Part – I and Part – II, we will now...
Non-intrusive & Real-time Monitoring of Corporate Users Internet Activity – Part II
In continuation to our earlier post Monitoring Corporate Users’ Internet Activity, we will now show you how to monitor corporate users’ Internet activity with Firewall...
Non-intrusive & Real-time Monitoring of Corporate Users Internet Activity – Part I
Like unrestricted privileges to administrative users in a network (PUMA), uncontrolled web access in companies has its own set of problems. Irresponsible Internet usage tends...
EventLog Analyzer – a perfect log management tool
Until recent years, enterprise IT infrastructure comprised of a few basic network devices. IT managers used simple tools to collect generated logs and analyzed them manually to generate log reports. IT heads and...
DNS Network Hacking on UK sites
It is one of the most popular technology news sites in UK and worldwide, The Register. The first news I read was “The Register Hacked”, posted...
Get your requirements in to the Firewall Analyzer product
Refer the forum post in the URL: https://forums.manageengine.com/#Topic/49000004953975 Ragavan S

