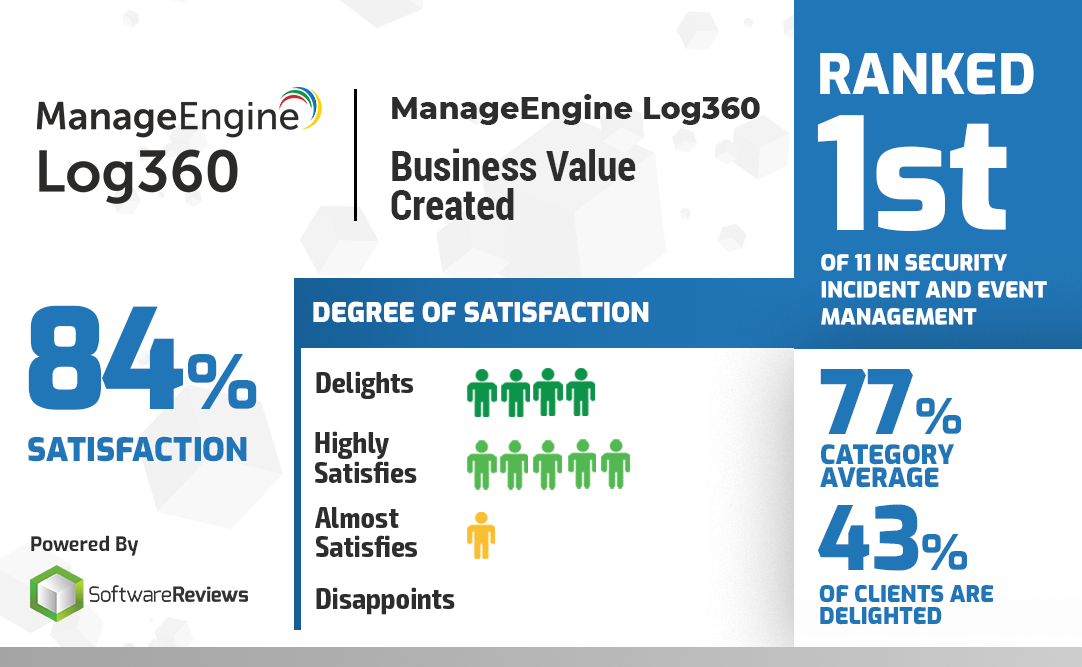
Software Reviews, a division of Info-Tech Research Group, has named Log360 a Champion in its recent Customer Experience Report. Out of eleven software vendors evaluated...

Free webinar on accelerating threat detection and response with user and entity behavior analytics (UEBA)
Most security personnel take measures to combat threats from outside the network. However, what happens when the threat originates from the place you least expect–your...

Conquer it with correlation—Part 3: Cryptojacking
In the previous posts of this blog series, we discussed advanced persistent threats and data breaches, highlighting the importance of data security in today’s times. In the...

Conquer it with correlation—Part 2: The data breach
In my previous post, we looked at how event correlation can be used to deal with advanced persistent threats (APTs). The thing is, an APT...

Conquer it with correlation—Part 1: The advanced persistent threat (APT)
Among all the pesky attacks that keep security administrators working late, advanced persistent threats (APTs) are possibly the most lethal. An APT is a long-term, targeted attack which involves stealthily spying on an organization’s...

Webinar: Learn a simple three-step approach to tackling threats
Technology has a lot to offer, from streamlining your business processes to protecting your network, but with all the advantages comes the risk of cyberthreats. Cybercriminals are always developing new...
Unravel security incidents using event correlation [Webinar]
Event correlation helps you wrap your head around the countless number of events going on in your organization. Our upcoming webinar, “Unraveling security incidents using event...
Webinar: Streamline incident management using SIEM
Organizations deal with several security incidents on a daily basis. Establishing accountability in resolving these incidents is a tough job. From detecting incidents to resolving them,...
Contest alert: Take part in the Log360 product pro challenge
We are delighted to announce our “Log360 product pro” challenge, a unique community contest. To participate, all you have to do is answer three simple questions over...