Intel SA-00086 vulnerability: Is your enterprise at risk?
 2017 is about to end. But is your fight against vulnerabilities just beginning?
2017 is about to end. But is your fight against vulnerabilities just beginning?This Thanksgiving, Intel decided to talk turkey about a string of vulnerabilities, Intel SA-00086, that external researchers discovered in their chips. When one of every 10 machines runs on Intel, you can imagine how many of your enterprise machines might be at risk.
After conducting a comprehensive review of their Intel® Management Engine (ME), Intel® Trusted Execution Engine (TXE), and Intel® Server Platform Services (SPS), Intel verified that systems running ME firmware versions 11.0/11.5/11.6/11.7/11.10/11.20, SPS firmware version 4.0, and TXE version 3.0 are impacted by the Intel SA-00086 vulnerability.Why is the Intel SA-00086 vulnerability so critical?
Intel’s internal review indicated that attackers could use this vulnerability to gain unauthorized access to systems that use Intel ME, SPS, or TXE. That means an attacker could:- Run arbitrary code to spy on your enterprise without being detected by users or your operating system.
- Exploit machines with spyware and invisible rootkits.
- Cause system instability or a system crash.
- Extract confidential or protected information from your computer’s memory.
Which systems are vulnerable?
Any system using one of those Intel chips listed earlier is vulnerable. That leaves most enterprise hardware, servers, IoT platforms, and high-end Windows and Linux laptops at risk.
How can you secure your network from Intel SA-00086 using Desktop Central?
Intel released the Intel SA-00086 detection tool that runs on Windows and Linux systems to help you identify if the Intel SA-00086 vulnerability has impacted your systems. As a system administrator, you cannot—in any practical sense—manually scan thousands of computers individually with Intel's detection tool. Using Desktop Central, however, you can absolutely scan thousands of computers all at once to identify which ones are affected by the Intel SA-00086 vulnerability.For Windows systems, just open Desktop Central and go through the steps below:1. Sync your script templates by clicking Configurations -> Script Repository -> Templates -> Sync.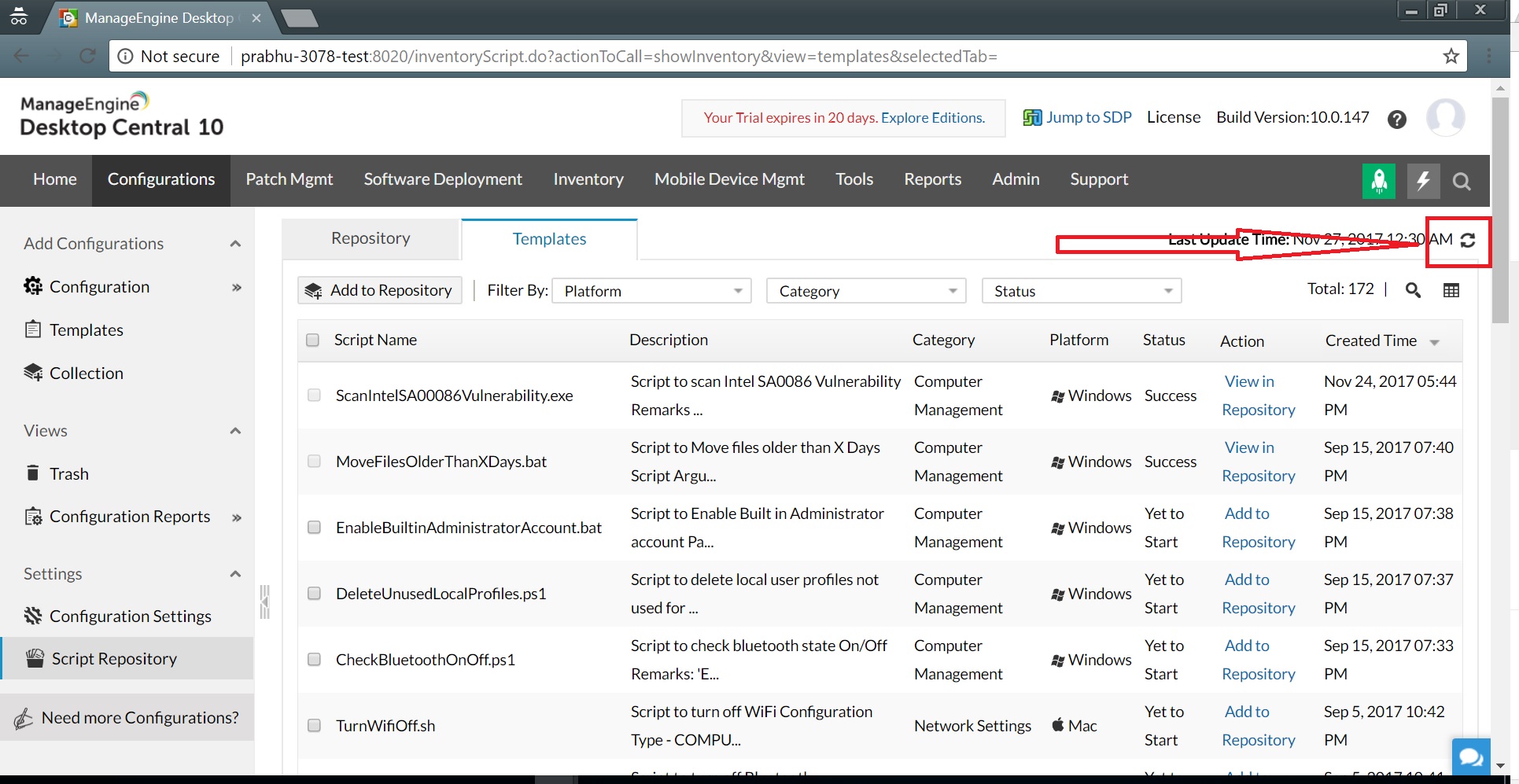 Sync Script templates2. Add the script "ScanIntelSA0086Vulnerability.exe" to Desktop Central's Script Repository. From there, deploy this script as a computer configuration.
Sync Script templates2. Add the script "ScanIntelSA0086Vulnerability.exe" to Desktop Central's Script Repository. From there, deploy this script as a computer configuration.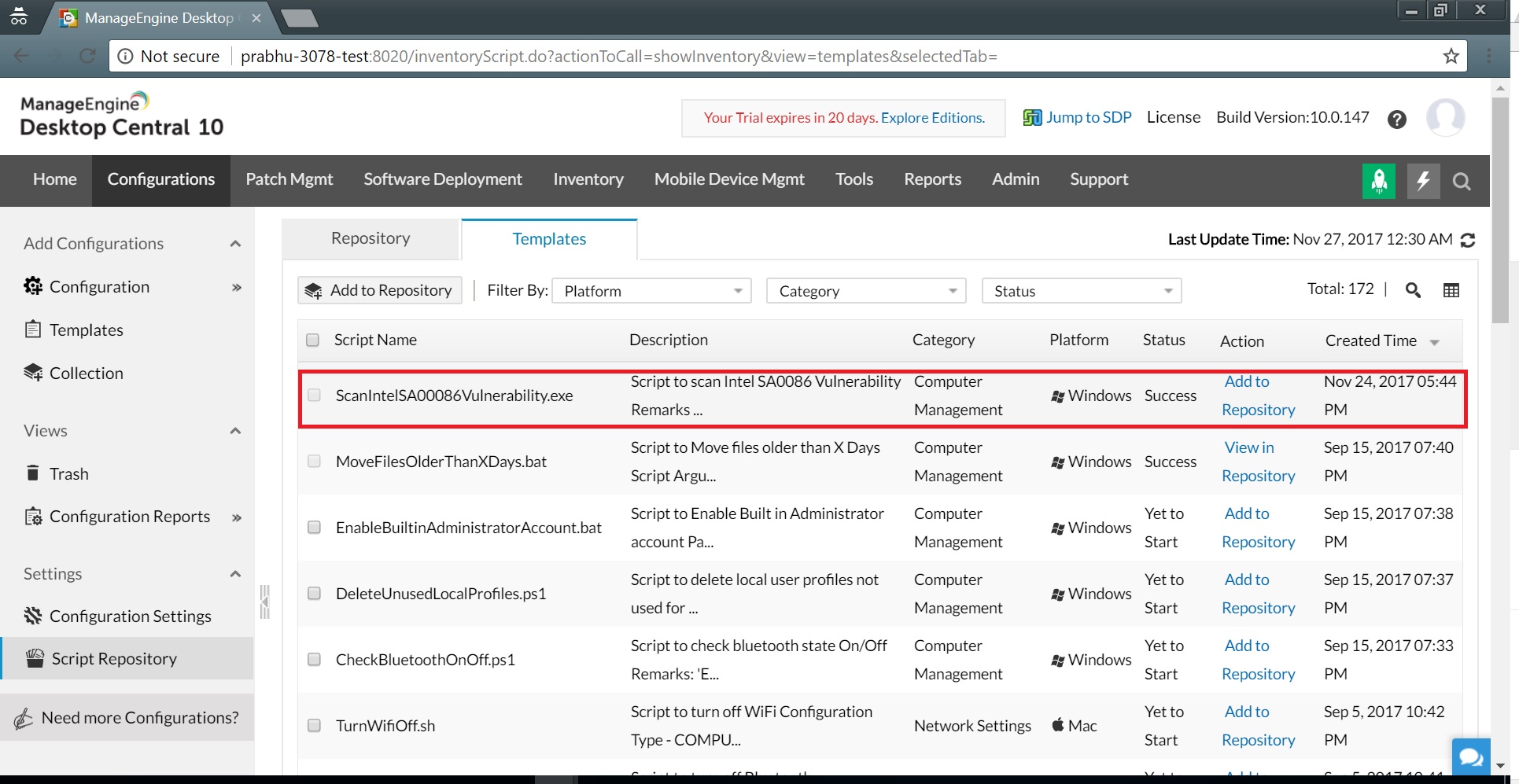 Add script to repository
Add script to repository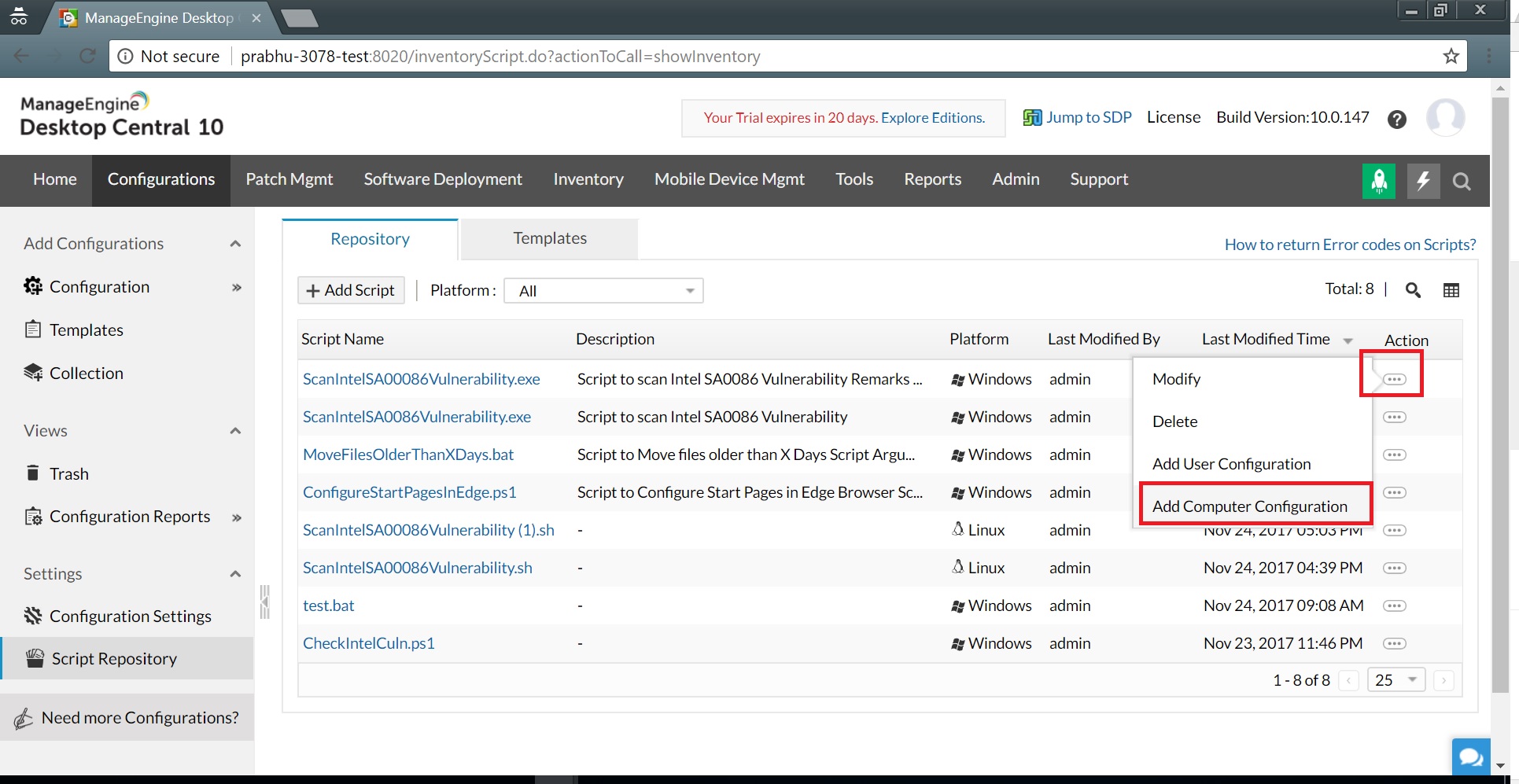 Add computer configuration3. Add the Intel SA-00086 detection tool (SA00086_Windows.zip) as a dependency file.
4. Select Enable Logging for Troubleshooting. This feature will provide a log of impacted systems.
Add computer configuration3. Add the Intel SA-00086 detection tool (SA00086_Windows.zip) as a dependency file.
4. Select Enable Logging for Troubleshooting. This feature will provide a log of impacted systems.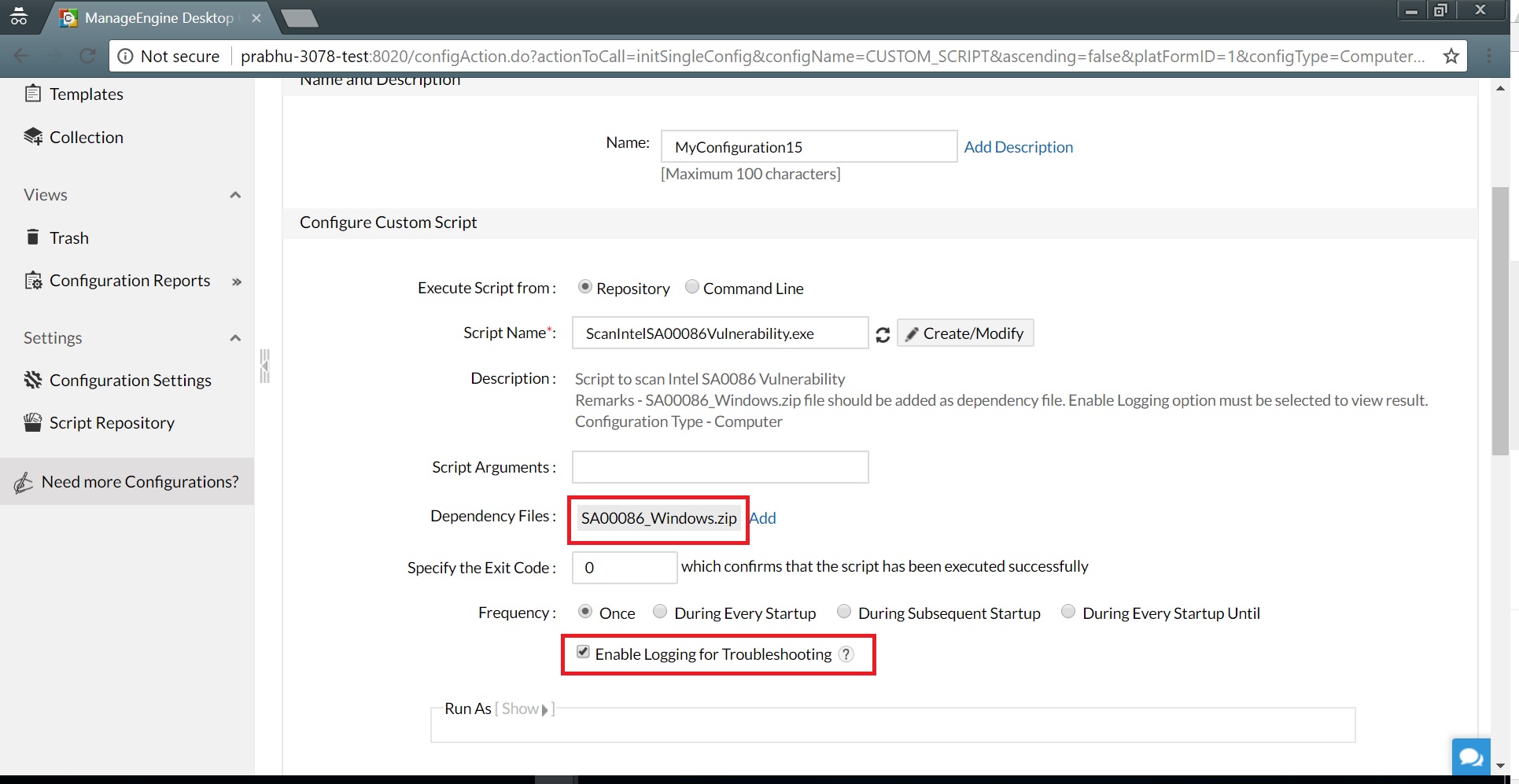 Add Intel-SA00086 detection tool as dependency file5. Run this configuration on your desired target machines, whether they're located in different branch locations or used by roaming users in any part of the world.
6. Once the configuration is executed successfully on all target systems (within 90 minutes), you can view the execution status of the configuration.
Add Intel-SA00086 detection tool as dependency file5. Run this configuration on your desired target machines, whether they're located in different branch locations or used by roaming users in any part of the world.
6. Once the configuration is executed successfully on all target systems (within 90 minutes), you can view the execution status of the configuration.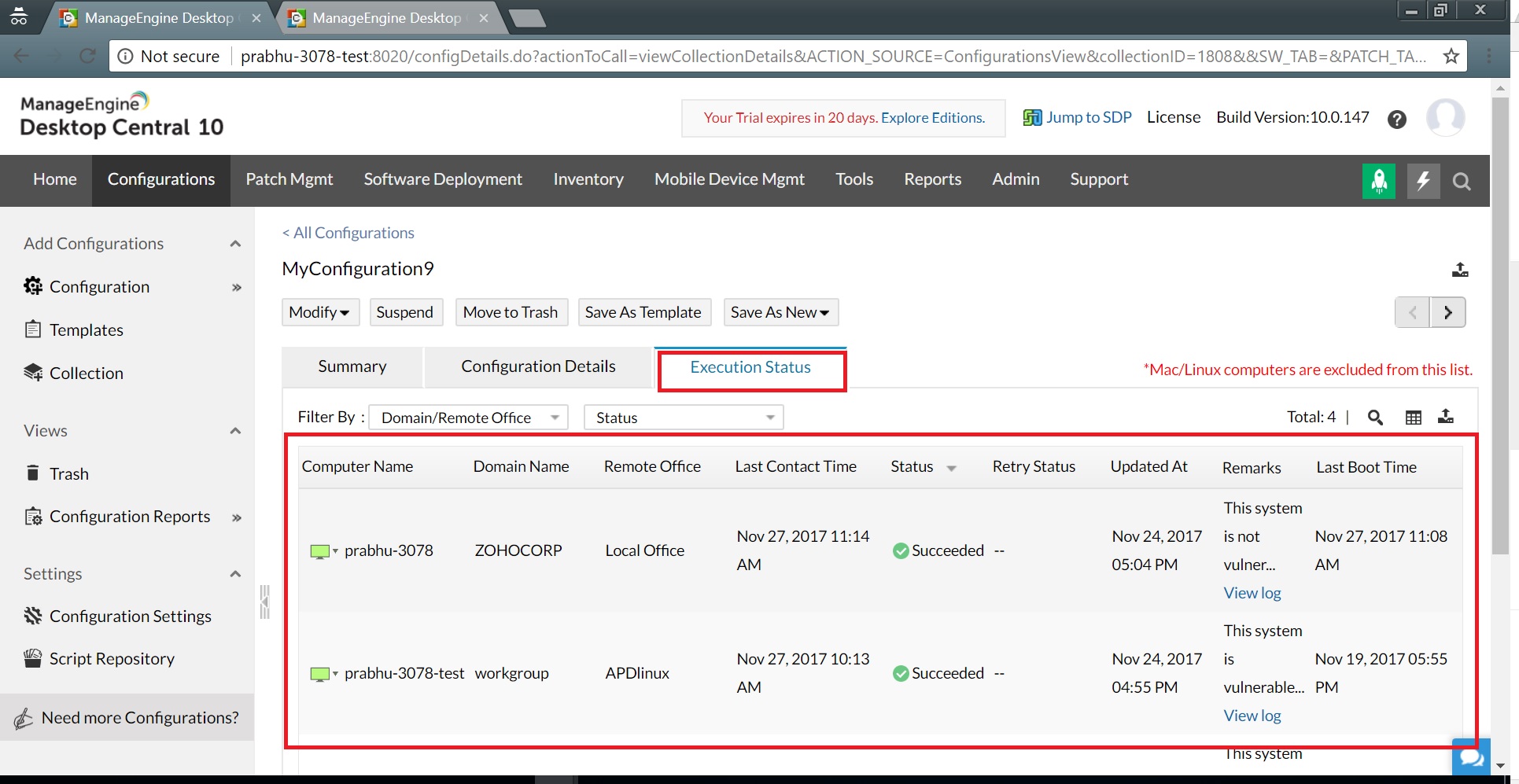 View the execution status7. Under the Remarks column, you can see if a system is vulnerable or not.
8. Click Export icon at the top right corner to download a report of all impacted systems (this is especially helpful during security audits).
View the execution status7. Under the Remarks column, you can see if a system is vulnerable or not.
8. Click Export icon at the top right corner to download a report of all impacted systems (this is especially helpful during security audits).For Linux systems, follow the steps below:
- Manually download the "ScanIntelSA0086Vulnerability.sh" script.
 Add Linux Script
Add Linux Script - Navigate to Script Repository and click on Add Script to add that script to Desktop Central's Script Repository.
- Add the Intel SA-00086 detection tool (SA00086_linux.tar.gz) as a dependency file.
- Follow steps 4 through 8 for Windows systems listed above.
With a new vulnerability being unleashed every day, enterprises have finally realized the need for an effective tool to secure their endpoints. Desktop Central is integrated desktop and mobile device management software that allows you to automatically patch Windows, Mac, and Linux endpoints; deploy configurations; and perform various other operations to secure your network against such security threats.