This Week’s Five is a weekly column of five interesting reads from all over the web, with a different topic each week. This week, we’ll try to...

This Week’s Five: SysAdmins are not humans, seriously!
Your network is safe, your computer is working, and your printer is running. Why? Because you’ve a great sysadmin who is keeping your business up...
Open Source Software: The Hidden Cost of Free
Recently, Michael Skok wrote that “open source is eating the software world.” As general partner at North Bridge Venture Partners, Skok should know. He’s witnessed the power of open...

Will mobile devices replace desktops in enterprises?
We keep hearing new concepts around mobile devices every passing day. BYOD, BYOA, MDM, MAM etc. have become the buzz words of IT industry. Are...

This Week’s Five: Active Directory Management & Beyond
This Week’s Five is a weekly column of five interesting reads from all over the web, with a different topic each week. This week, we’ll explore the...

IT outsourcing: When outsiders become insiders, how do you ensure information security?
Organizations outsource a part or whole of their IT services to third-party service providers for various reasons, such as cost savings, leveraging outside expertise, need...
The Next $100 Billion Technology Market?
Just as we are getting our arms around terms like B2B and BYOD, the latest technology acronym emerges — M2M. And this one is big...

IT Business Acquisitions And The Side Effects On Customers
Originally published in (Business Computing World) Like any other, the IT market has software vendors of different sizes ranging from small to large. The core...
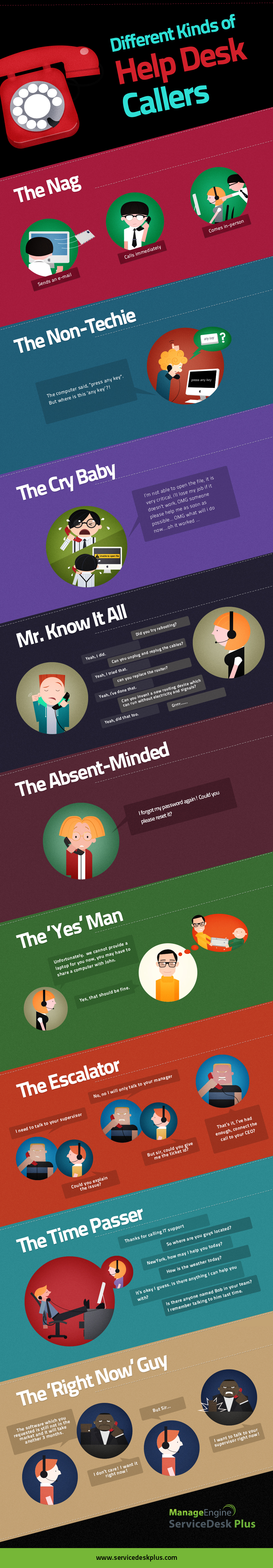
Different Kinds of Help Desk Callers – Helpdesk Humour
Embed Code: <img src=”http://www.manageengine.com/products/service-desk/images/helpdesk-infographics.jpg” alt=”Different kinds of Help Desk Callers” /><p><em>Image originally posted on <a href=”http://www.manageengine.com/products/service-desk/helpdesk-infographics.html”>Help Desk Infographics, ManageEngine ServiceDesk Plus</a></em></p> Share & Get a...