Do you love your ManageEngine products, but aren’t sure you’re getting the most out of them? Have any burning IT questions that you can’t seem to...

Learn how password synchronization can benefit your organization [Free webinar]
When you increase the number of applications in your organization, you’re forcing your end users to remember more passwords. The more passwords end users have...

Third biggest data breach in history emphasizes the need for the GDPR
The top two data breaches in history, when you look at the number of affected users, comes down to Yahoo in 2013 (3 billion users) and FriendFinder in 2016 (412 million...

Microsoft Patch Tuesday April 2018 updates
For this month’s Patch Tuesday, Microsoft fixed 66 security issues. Luckily, in this round of updates, Microsoft didn’t find any zero-day vulnerabilities that needed patching, but there are a few major...

Lessons from data breaches that every enterprise should take to heart
“Four years later, Yahoo still doesn’t know how 3 billion accounts were hacked” read TechCrunch on November 8, 2017. The 2013 Yahoo breach is still as big...
Learn how to protect your environment from ransomware [Free webinar]
Back by popular demand, the Everything you need to know about ransomware webinar will be held on April 12th. Whether you’re an administrator, analyst, or a CIO, ransomware is unsettling to...

ManageEngine wins Network Management & Monitoring Vendor of the Year at the NWME Awards 2018
The results of the ninth annual Tahawul Tech’s Network World Middle East Awards have been announced, and ManageEngine has won the title for Network Management & Monitoring Vendor...

The GDPR: Correcting data security negligence from companies like Facebook, Swisscom and L’express
Incident 1: Facebook, Cambridge Analytica data leak According to The New York Times, Cambridge Analytica tried to influence the 2016 Presidential elections in America. This was executed by using data collected from over...
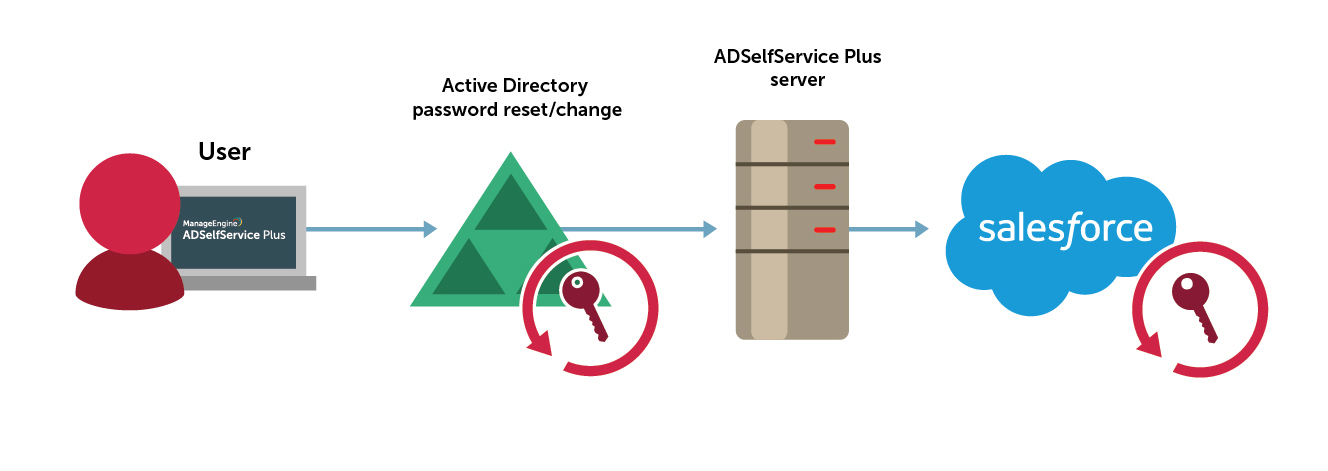
Password synchronization between Active Directory and Salesforce accounts
As the number of Salesforce user accounts increases within your organization, managing those accounts becomes a challenge. This adds mundane password management tasks to the...
