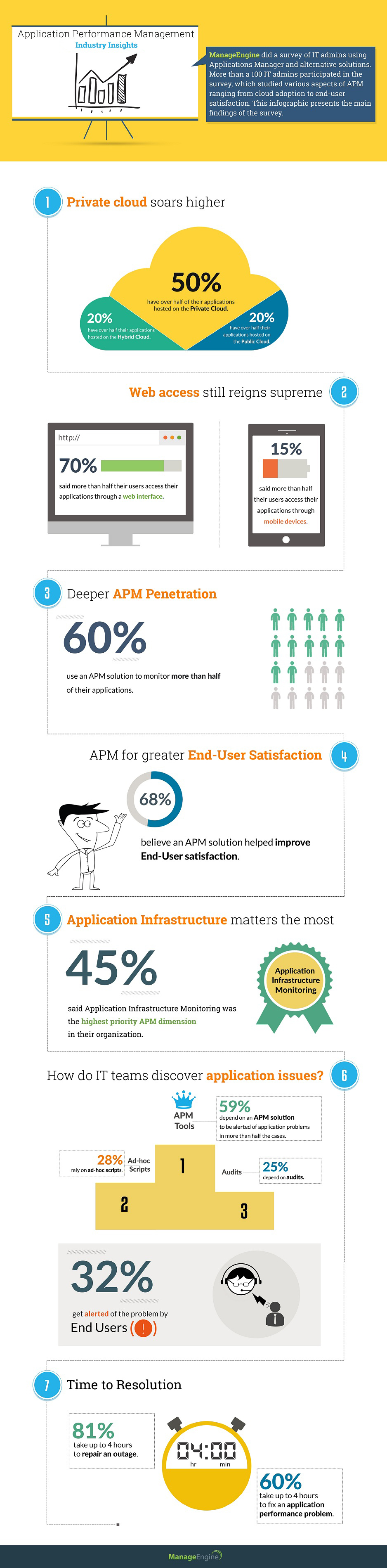
Nearly one out of every three businesses (32%) become aware of most application performance issues from their end users, according to a recent ManageEngine Application...

UserConf vignettes.
We just wrapped up our user conference on IT service management (ITSM), and boy, it was one phenomenal experience. It was amazing and reassuring to see...

Salute the “Lord of the Links” on World SysAdmin Appreciation Day
While you get a pat on your back, they disappear in the shadows of the server rack. While the office celebrates your success, they never...
IT Security: The New Target for CEO Performance
As Gregg Steinhafel steps down as chairman and CEO of Target, we’re witnessing more than just an act of contrition for one of the largest and...

Five Lessons IT Can Learn from Flappy Bird
Hi, my name is Mason, and it’s been 36 minutes since I last played Flappy Bird. My current high score is 24. If you are...
Microsoft Under Nadella: Reimagining Mobile and Cloud, Finally
Well, the white smoke from the Microsoft CEO search chimney signaled this week that the company had finally selected a new CEO – Satya Nadella....
Smartwatches, Google Glass and the Wearable Technology Chocolate Box
At $8 billion in 2013 revenues (projected), the wearable technology market is nascent but promising. By 2017, revenue from these new devices is projected to...