2017 was full of new information, new technologies, and lessons learned. As I toured the world again, I was reminded of the commonality that the...
Preparing for the GDPR: Designing Active Directory groups
One aspect of the GDPR is the fact that all users who have access to personal data must be monitored. As a best practice, only...
GDPR preparation—Testing
GDPR compliance auditing will be new to many organizations that have never been under a compliance regulation before. Therefore, many of the logistics around the...
Common mistakes administrators make when applying GPOs – Part 1
Active Directory (AD) and Group Policy (GP) are essential components of most enterprises, so it goes without saying that making changes to AD and GP...

Optimize GPO processing: How does Group Policy work?
Group Policy is a great mechanism for deploying numerous settings across different Active Directory (AD) objects. In this blog, we’ll discuss the basics of Group...
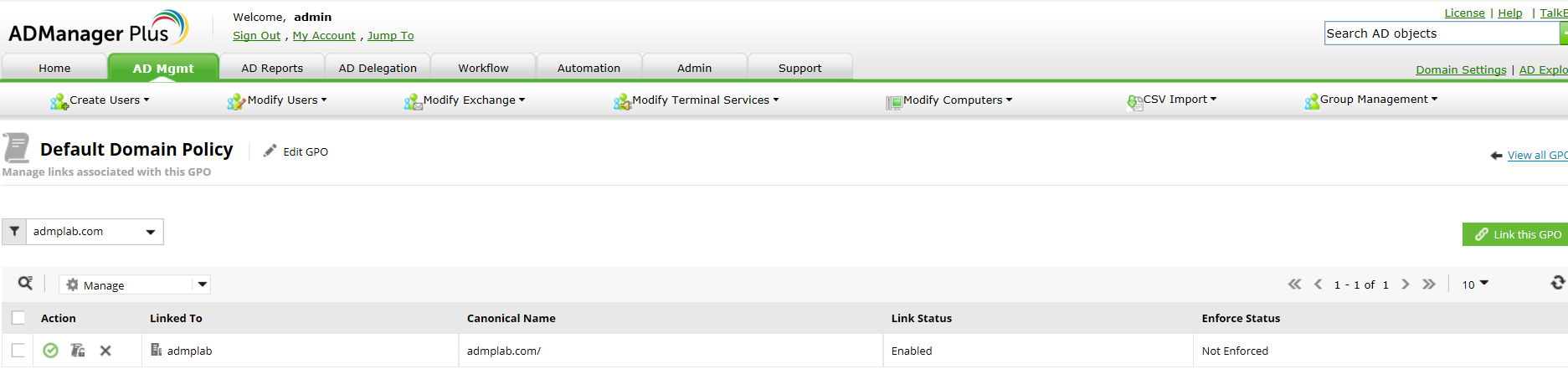
How to easily find a GPO’s Administrative Template settings
I’d like to propose a challenge for all you users working with native Active Directory tools: find a way to change the period of inactivity before Windows begins hibernating for every system...
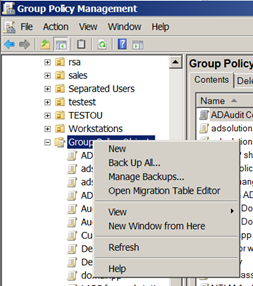
Common mistakes administrators make when applying GPOs – Part 3
Although it’s not directly related to the application of Group Policy Objects (GPOs), administrators typically do not back up their GPOs so they can recover...
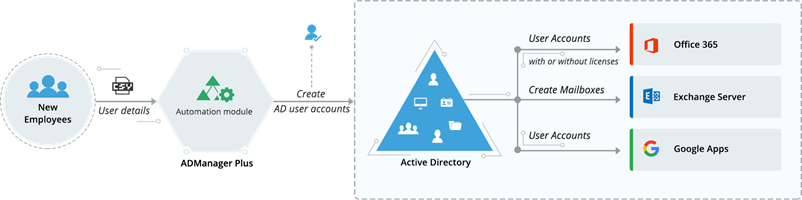
The future of Active Directory management: User onboarding
One domain that can definitely benefit from automation is Active Directory (AD) management, which forms the epicenter for all IT operations. For decades, AD management has been taxing,...
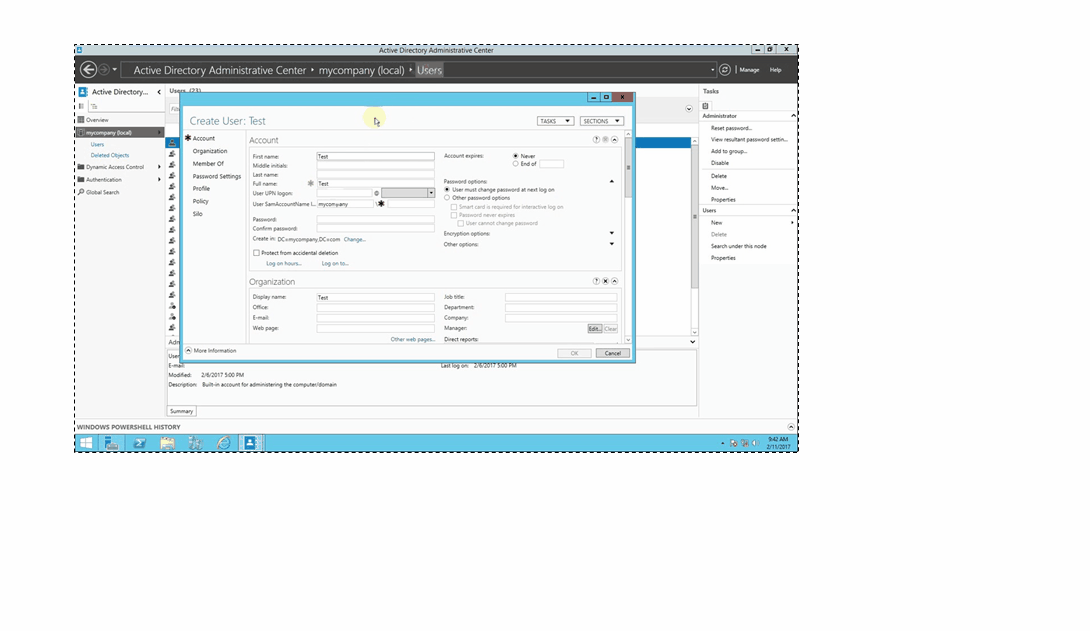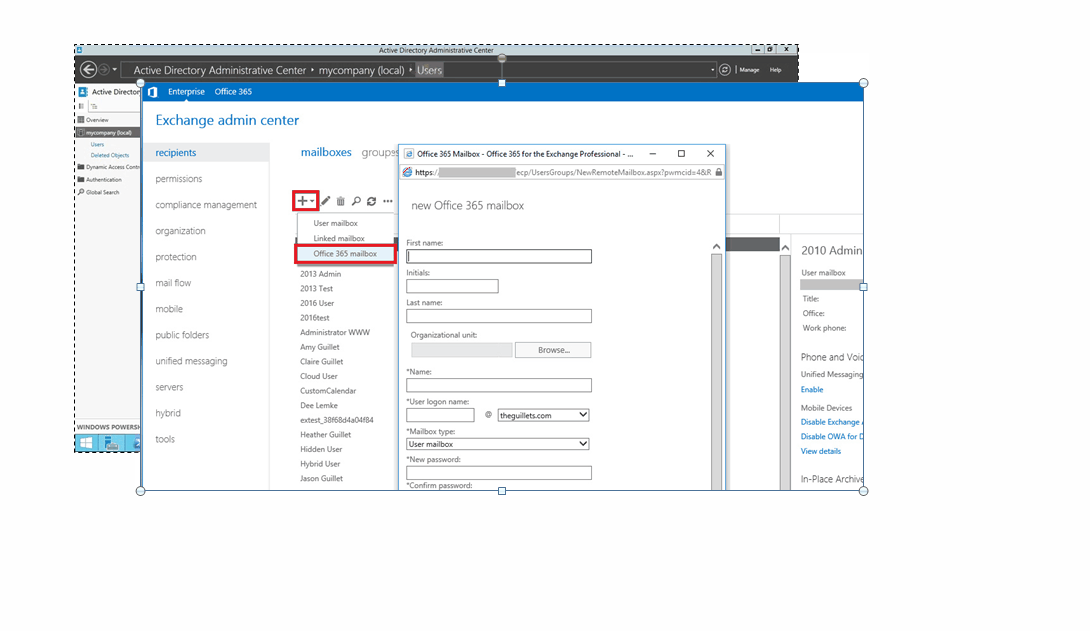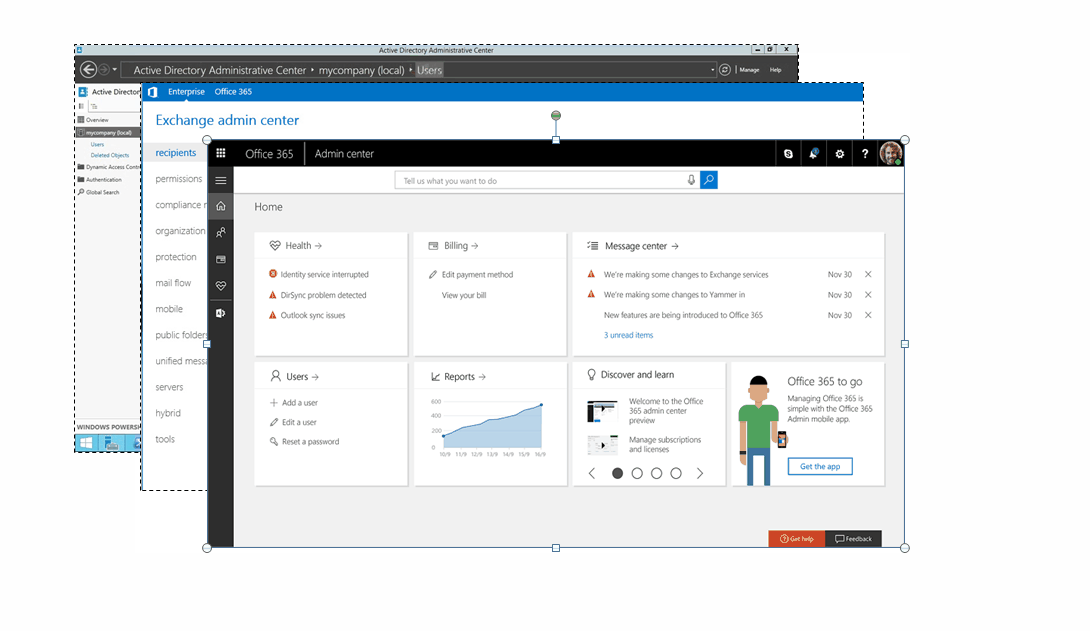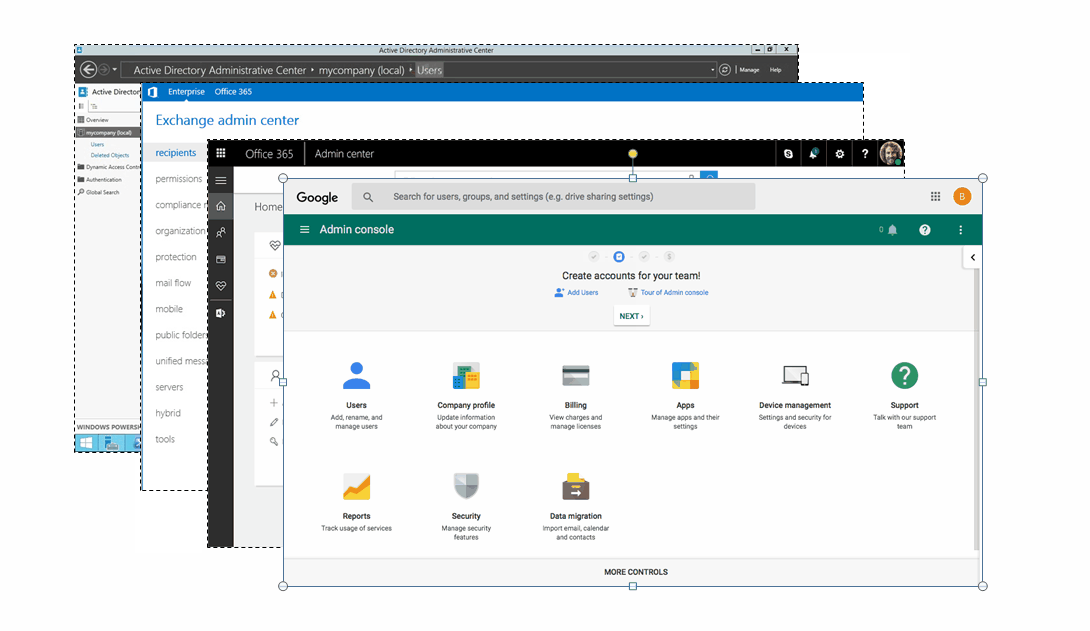
Manage Active Directory from ServiceDesk Plus? Now you can!
Why don’t help desk applications manage Active Directory (AD)? Given the wide array of features that ITSM tools natively offer, it seems like AD management...
