With the number of applications used by companies hitting an all-time high, users are forced to remember a multitude of passwords for applications like Salesforce, G...
Use change monitoring to never let a change go unnoticed in Active Directory
Active Directory relies on services distributed across many, interdependent devices in different locations. To ensure consistent security throughout such a large environment, monitoring changes is...

Streamlining Office 365 user provisioning using ADManager Plus
In this blog, we’ll talk about the challenges in using native tools to provision Office 365 users, as well as how ADManager Plus can help streamline Office 365 user provisioning...
Up your Exchange security game with this free webinar
Did you know experts have predicted that global spending on information security will exceed $93 billion in 2018? You read that right, and now’s as good a time as any to...
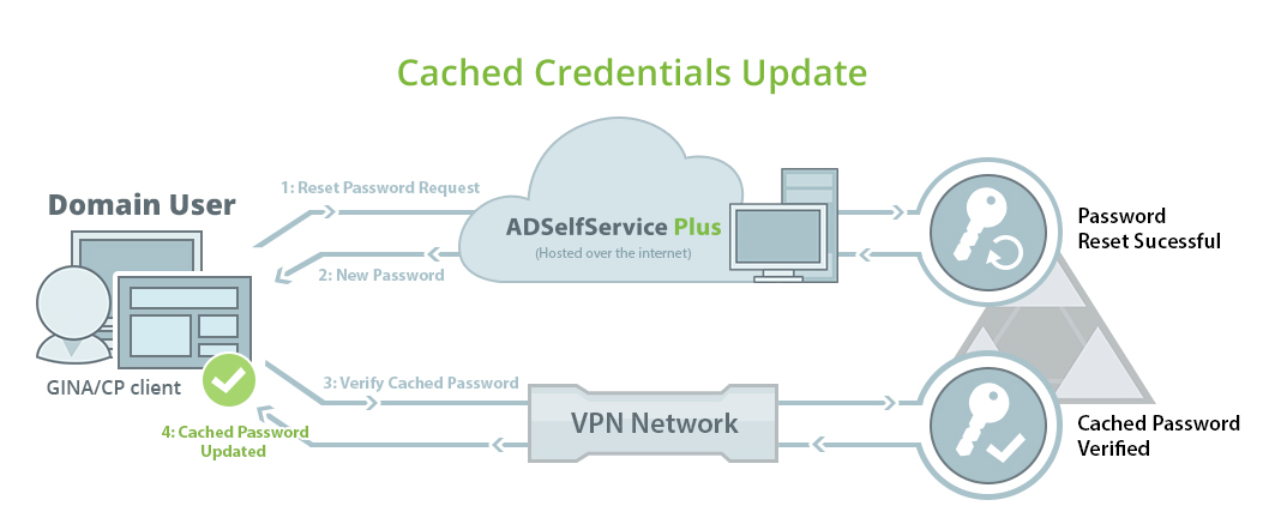
Let your users work on the go without any hassle
With many of today’s businesses functioning at a global scale, some employees find themselves constantly traveling. Amidst the chaos of travel, it’s only natural to forget login credentials, especially when switching between many applications. No matter...

Webinar: Negating insider threats
Organizations need to be keenly aware of the actions their employees take, especially with the advanced computer knowledge that most employees possess today. A disgruntled...
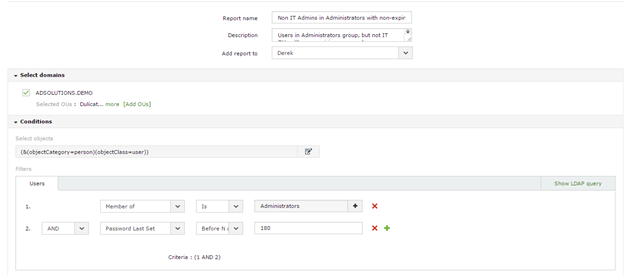
How to find objects in Active Directory
Active Directory (AD) administrators have always had to come up with unique ways of finding objects in Active Directory. I am not talking about the...

Overcoming the shortcomings of native password policy controls in Active Directory
With the constant threat of hackers trying to get their hands on your sensitive information, you need your passwords to be nothing less than hack-proof....
How syncing passwords between Active Directory and Salesforce reduced one IT team’s workload
Every IT help desk is burdened with password-related requests, which are especially tough on IT administrators who cater to a large number of end users,...

