Details about cyberattacks on small-and-medium-sized businesses (SMBs) may not make it to the headlines, but numerous industry reports and surveys have highlighted the grim reality...
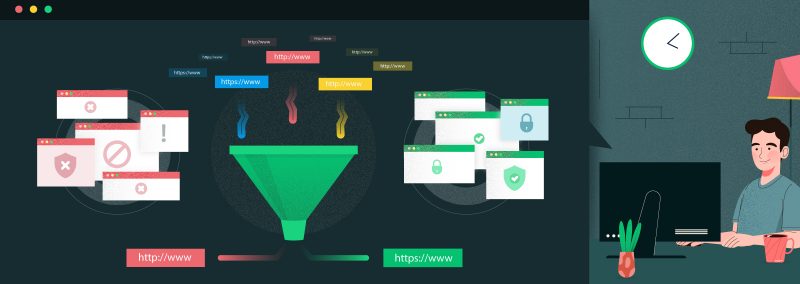
Why companies need URL filtering for enhanced cloud protection
The cloud landscape is rife with unsafe URLs and inappropriate content. This—coupled with the accelerated adoption of cloud applications in the workplace—has created an urgent...
The role of endpoints in the security of your network
Endpoint security is a hot topic of discussion, especially now with so many businesses shifting to remote work. First, let’s define what endpoints are. Endpoints are...

Healthcare cybersecurity: Our 6-step plan to secure healthcare data
The HIPAA Journal reported that “2020 was the worst ever year for healthcare industry data breaches.” In the US alone, there were 642 reported data...
Operation panopticon: How a weak IAM strategy led to the security camera hack across organizations
On March 9, 2021, Verkada, a software company that specializes in making security cameras for monitoring physical access control, was subject to a security hack....
The road ahead: McKinsey’s top 5 cybersecurity predictions for 2021 and beyond
What is a bigger threat to mankind: nuclear weapons or cybercrime? While most would say nuclear weapons, Warren Buffett says cybercrime would take the cake....
Azure security 101: Security essentials, logs, authentication, and more
“Where necessity speaks, it demands”. This old saying seems particularly apt right now with the pandemic forcing organizations to completely change the way they think...
Windows logon auditing: Everything you need to know in only 10 minutes [Free e-book]
User logon activity needs to be audited to meet various security, operational, and compliance requirements of an IT environment, such as: Detecting suspicious activities like...

