Building a complete network security checklist
Understanding what to audit in a network can be chaotic and confusing. Building a complete network security checklist is crucial for organizations with computers connected to the internet or to each other. Think of it like an antivirus scan you might run on your computer to find Trojans or malware, except you're scanning your entire network to find anything that may cripple it.
The aim of this blog is to provide sufficient insights to help you get started on building a basic checklist that covers the critical aspects of network security. You can alter it based on your the components you need to audit in your network. Have a checklist already? Great! Take a look anyway—you never know what you're missing.
Defining the scope of your audit checklist
Start easy. Here are three simple questions you need to ask yourself before you start planning your checklist:
Where is critical data hosted in your network?
Which users have access to the data?
- Which configurations, i.e., server configurations or security policies, directly determine the security of your data?
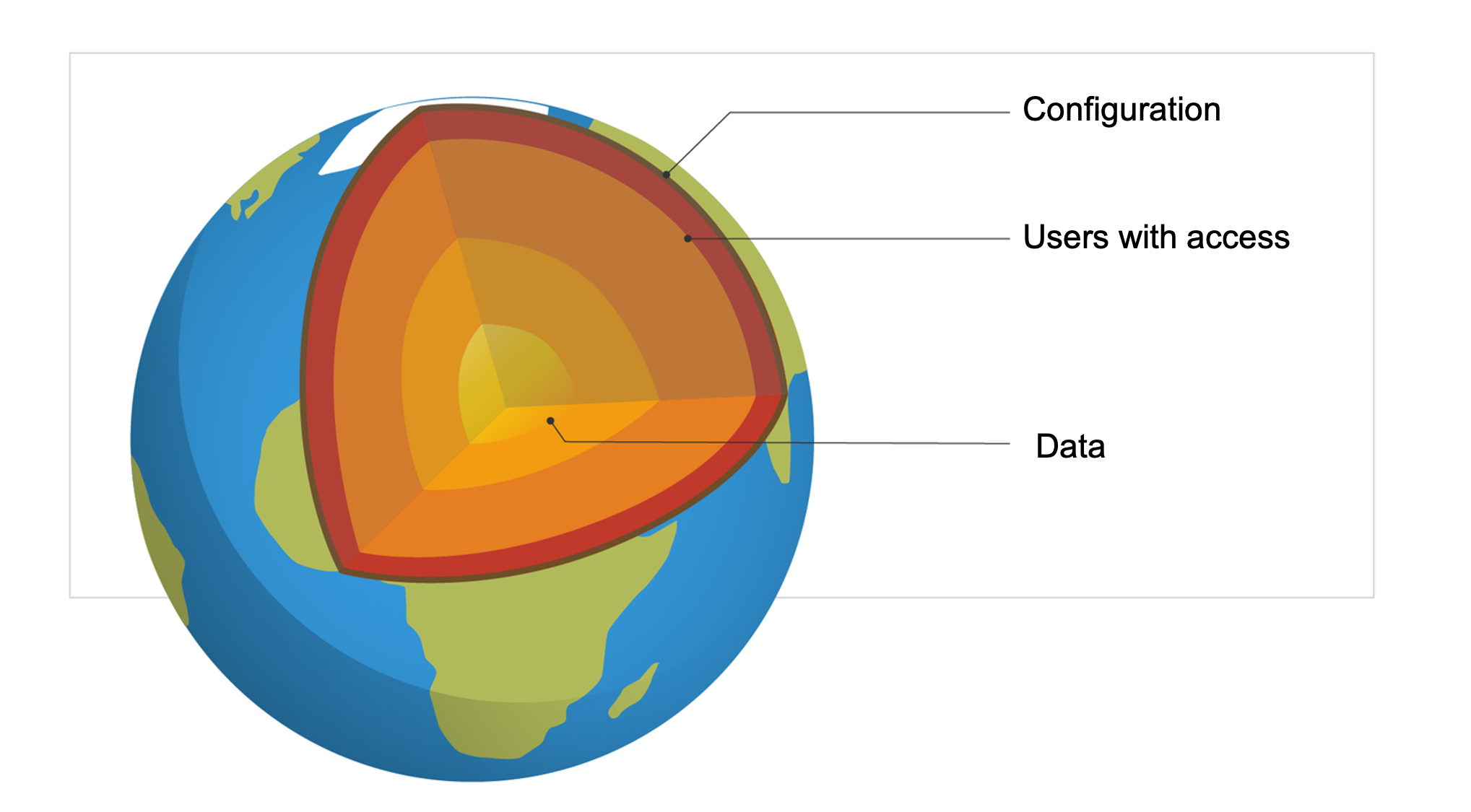
The end goal of every security attack, internal or external, is to gain access to your business-confidential data. Every network misconfiguration, each inappropriate permission granted to a user—these are all stepping stones to get to the crown jewels: your data.
Figuring out where the data is
You might already know where your data is stored, but let's break it down anyway.
Data may be stored in file servers such as a Windows Server or Cluster; databases like SQL or Oracle; in the cloud on Azure storage accounts or Amazon Web Services (AWS) S3 buckets; in member servers and workstations by users; or other data storage mediums like NetApp, EMC, or NAS.
Now that you know all the places where your data could be stored, let's examine how end users can gain access to this data.
Who has the keys to the safe?
Think of your data like valuables stored in a safe, and permissions as the keys to it. The most common way users gain access to data is via misconfigured permissions. Apart from explicitly assigned permissions on file servers and other data storage devices, here are a few other ways things can go wrong:- Access via nested group permissions: A random user being granted access to a folder is something you might notice. However, an anonymous user backdoored into a security group with access to a folder is something you probably won't catch.

Exposed user credentials: A remote user's VPN credentials are exposed in a website breach. An attacker uses these credentials to log in to the network and can now access files as the authorized user. The only way to detect attack attempts like this is by monitoring rogue logons and file accesses from unknown sources.
Leaked cloud data: A developer working with Azure accidentally embeds the keys to a storage account in a script file uploaded to a public GitHub repository. Leaving passwords and keys to storage in cloud platforms is more common than you think, so verify they're not present before the data goes public. Sometimes, storage in the cloud may have unnecessary broad permissions applied to it. For example: In an AWS S3 bucket, the "block public access" parameter is disabled.
- Misconfigured group policies: A user or a security group is granted the privilege to take ownership of files and folders. This is fundamentally a privilege that can block the actual owner from accessing their folder, so consider these permissions carefully.
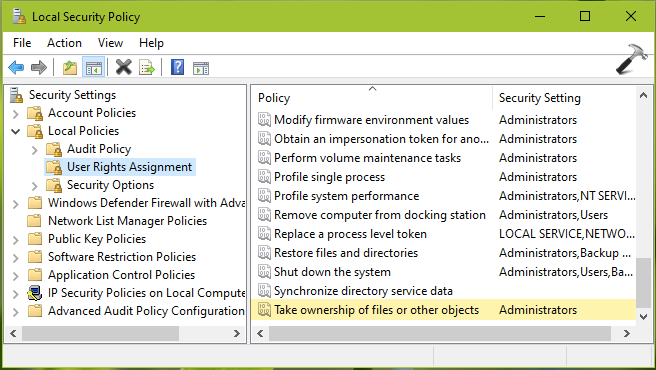
Incorrect roles assigned to users: An end user is granted a role on an SQL server, leading to a new, unauthorized login being created.
With so many different ways for permissions to go unchecked or misassigned, full-scale data compromise isn't far behind. Once a threat actor discovers a vulnerable permission on a user account or a server, they work laterally until data is acquired.
To prevent this, monitor various resources on your network along with the permissions assigned to or modified on user accounts 24/7. The permission change could be genuine, malicious, or triggered due to a process error. Either way, permission modifications need to be recorded and looked into.
Is the safe even locked?
While losing keys to a safe is a security risk, the safe also needs to be strong enough to withstand external force. In comparison, this is when the configuration of devices connected to the network plays a crucial role.
In simple words, an appropriate level of access for users and a secure network configuration together make up the security of your network. Let's take a look at a few examples:
Changes at the OS level:
Crucial Windows services, backup processes, event logging processes, etc. may have stopped. Alternatively, new processes and services were started
Firewall rules or registry keys were modified; Windows systems were restored to an older version
New packages were installed on Linux systems by running SUDO or Yum commands
Configuration changes were made on system security files like Program files (x86)
Configuration changes on devices connected to a network:
Configuration changes on VPN services running on your network
Monitoring firewall traffic can help detect intrusion attempts
Database changes like tables being deleted, or commands or queries executed to retrieve something from an existing database
Configuration changes on web servers like Microsoft Internet Information Services (IIS) or Apache
Reconfigured virtual machines with changed device IPs, or modified data stores and clusters
The use cases above should give you a good idea of the permission and configuration changes that may occur in your network. Monitoring these network changes can help you detect and prevent potential security attacks before they cause widespread damage.
However, such intense levels of monitoring can seem daunting, especially if you're dependent on the native capabilities of your OS or application. Most native monitoring tools have similar limitations; refer to the image below.

For a tool that can overcome these limitations and help you flesh out your security checklist, check out our integrated security information and event management (SIEM) solution, Log360. With Log360, you can examine the various security and configuration logs produced by devices connected to your network on a single screen. It provides granular search capabilities to instantly find any sensitive, suspicious, or malicious activity. It also instantly notifies authorized personnel of this activity and helps initiate mitigation steps to handle a security incident.
Want to see for yourself how the security changes discussed above could lead to a full-scale security breach? Visit our IT security under attack page to view live demonstrations of attacks on IT environments such as Active Directory (AD), Azure, and AWS, and OSs like Windows and Linux, and build a complete defense strategy with Log360.