Chances are you’ve heard of traditional credential-based attacks on Active Directory (AD) and cloud applications—brute force attacks, dictionary attacks, and keylogging, to name a few. There’s now another attack type you should familiarize yourself with: password spray attacks. In this blog, we’ll analyze why you should be wary of them and the best way to tackle them.
How password spray attacks work
In password spray attacks, the hacker tries one common user password across multiple user accounts before moving on to a second password, which allows them to evade account lockouts. Let’s see a password spray attack in action. First, the hacker gets a list of the mailboxes that are accessible by all domain users using penetration tools such as MailSniper. Next, they try common passwords like “Password@123” for every account.
According to US-CERT, this attack frequently targets user IDs with single sign-on (SSO) access to cloud applications. This is because any correct guess at a user’s password who utilizes SSO gives the hacker access to all the connected applications. On top of this, the hacker’s malicious activity is hard to track because the failed login attempts are isolated.
ADSelfService Plus to the rescue
To keep credential-based attacks such as password spray attacks at bay, ADSelfService Plus, an integrated self-service password management and SSO solution, offers multiple identity verification techniques as the second factor of authentication, such as:
-
SMS and email-based OTPs
-
DUO Security (via phone call or push notification)
-
RSA SecurID
-
RADIUS
The solution also provides users secure access to all SAML-enabled cloud applications, including Office 365, G Suite, Salesforce, and more (watch video).
SSO + TFA = No success for credential-based attacks
For one-click access to all cloud applications via SSO, users only have to log in to the ADSelfService Plus portal. Let’s take a successful password spray attack as an example. The configured authentication methods in ADSelfService Plus allows only those users who have completed the second factor to access their accounts, shutting the password spray attack down.
As Microsoft’s CISO Bret Arsenault said at Ignite 2018, “If you have MFA and if you have strong proofing, then you’re really in a great state.”
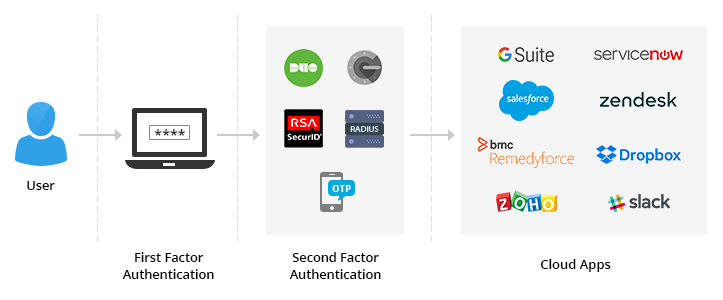
ADSelfService Plus’ authentication in action
-
In the ADSelfService Plus user login page, users enter their Windows login credentials as the first form of authentication.
-
Next, they authenticate their identity using the configured authentication technique.
-
Once users are logged in, a list of applications they have access to is displayed.
-
Users can securely access applications via SSO.
Policy-based access control
ADSelfService Plus allows you to create policies for SSO that determine who gets access to what cloud applications. For instance, ADSelfService Plus allows you to create a policy that provides access to CRM applications—such as Salesforce and SugarCRM—only to users in the Sales OU.
Monitor for exposure
Hackers will always come up with innovative ways to steal passwords. It’s time we accept the fact that we can never truly stop passwords from being stolen or sold. So it’s crucial that you invest in authentication techniques and custom password policies that thwart attacks like password spraying. If you stay vigilant when it comes to credential theft with ADSelfService Plus, your employees and your business will thank you for the ongoing protection.
Want to explore more? Go ahead and try ADSelfService Plus to see all these features in action yourself!
