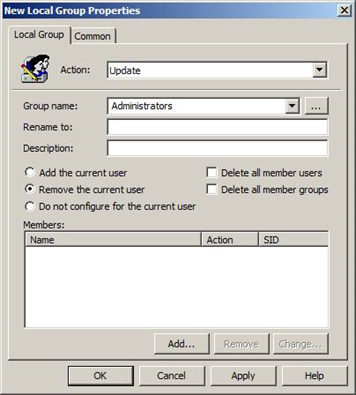
If you have a long list of users with administrative rights, there’s a good chance you’ve offered excessive amount of privilege to accounts that don’t...
Search results for: applications manager
One expired security certificate leaves millions of smartphones offline
Yes, you read the headline right. And no, this outage isn’t the first of its kind. Ericsson, the Swedish multinational networking and telecommunications company, joins the list of...

Microsoft Patch Tuesday updates for December 2018
Another month and another Patch Tuesday update from Microsoft. But this month, the buzz is all about a third-party patch from Adobe that addresses a...

Better functional invoices, new integrations, and more introduced in ServiceDesk Plus MSP 9410
Your trusted MSP service desk software just got a whole lot better with a set of new features and enhancements to take your IT support experience...

Industry best practices for endpoint security
Lately, hackers on the lookout for vulnerable systems have kept the IT industry busy. While various OS and software vendors strive to keep their users’ data intact by...

The Australian way of mitigating cybersecurity incidents
Many enterprises are actively building their IT security procedures to prevent the alarming number of cyberattacks businesses face today. According to the Australian Cyber Security Centre (ACSC) Threat Report 2017, 56 percent of self-reported...

What is mobile device management, and why will it enhance enterprise IT security?
Technological advancements aren’t hard to find. Just look at how huge CRT monitor computers have turned into slim, weightless laptops—or how brick-sized cellular phones have become...