”The complexity of APM solutions will continue to decrease, making them lower cost and easily implemented.” Jonah Kowall Research Director in Gartner’s IT Operations Research...
Search results for: 7 problem management

Take Control of Multi-Vendor Storage Environments with ManageEngine OpStor
Today, more enterprises are adopting a multi-vendor storage strategy to meet their exploding storage requirements. Why? Because introducing a second storage vendor helps companies get the best prices...

Passwords, King of Authentication: Long Live the King!
This post is a reproduction of an article I wrote that was originally published in Business Computing World. “When you play the Game of Thrones, you...

Improve Your IT Productivity with OpManager’s New Fluidic UI
Today, enterprises handle 10 times more alarms than they did a decade ago. At $70,000 a year, a systems administrator costs $35 per hour. A...
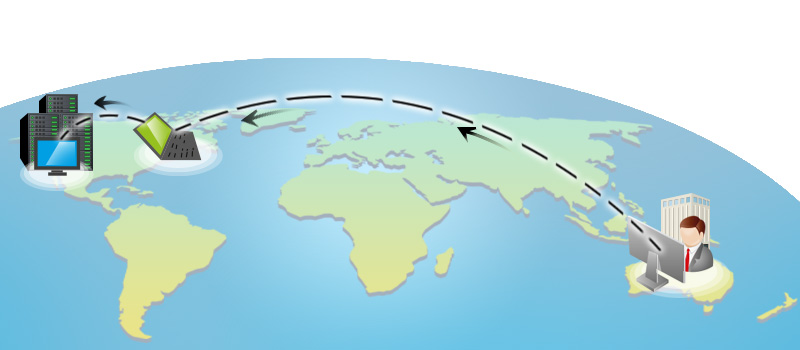
Fully Controlled and Closely Monitored Remote Access, a Critical Aspect of DCIM
Without proper data center remote access management, administrators invite security issues and waste time. With more organizations adopting cloud computing and virtualization, data center operations...
Guest blog: Upheaval in the service desk space
This is a guest post by Peter Dorfman. Help desk software is now a free download! The wheels turn slowly in the enterprise software business....
IT Security and Auditing Framework – A Glass Half Full or Half Empty?
Log Management, Compliance Reporting and SIEM Corporate islands with no connectivity to the external world and/or employees seeking permission to share company critical information with...
The Burn-Proof CIO: 5 Tactics For Surviving The Red-Hot Tech Sector
Technology is on fire. Technology-related sectors may have single-handedly pulled the economy back from the brink of disaster. A recent report by Ibis World reveals...