With a rapidly changing business landscape, applications usually drive the enterprise. As proof, a Gartner study reveals that in 2015, the annual IT application development...
Search results for: 7 problem management
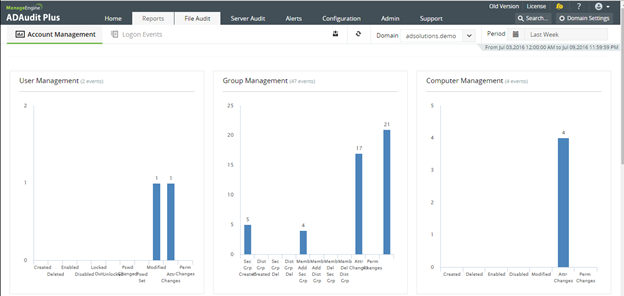
Powerful reporting of historical Active Directory activities
Every Active Directory administrator has needed to get a report of access, activities, and more from the past actions performed against Active Directory. When you...

This week’s five: CIOs – The true business transformers.
This week’s five is a weekly column on five recent reads from all over the web. This week, we’ll talk about the chief information officers. ...
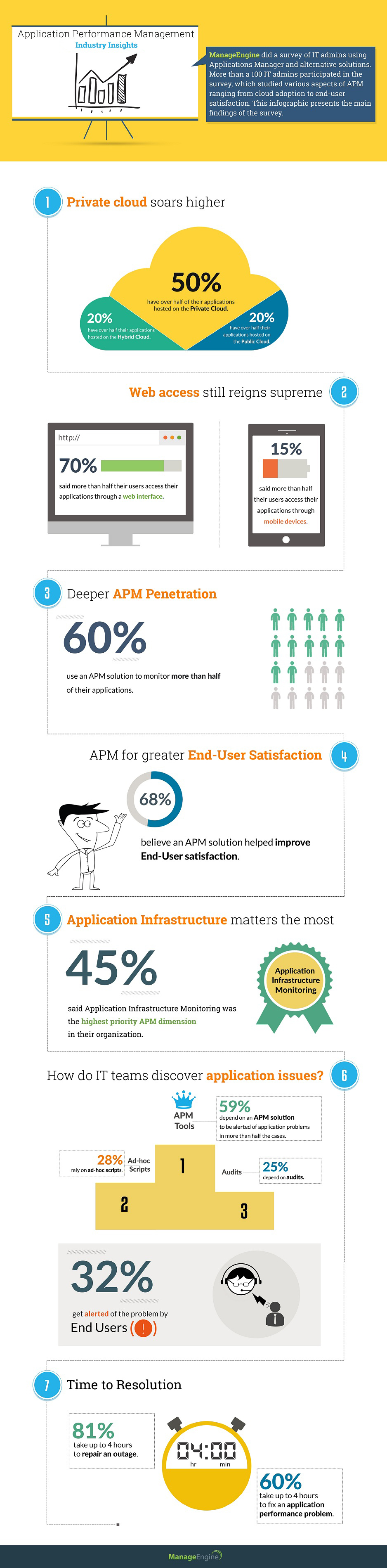
One-third of businesses depend on end users to report application performance issues
Nearly one out of every three businesses (32%) become aware of most application performance issues from their end users, according to a recent ManageEngine Application...
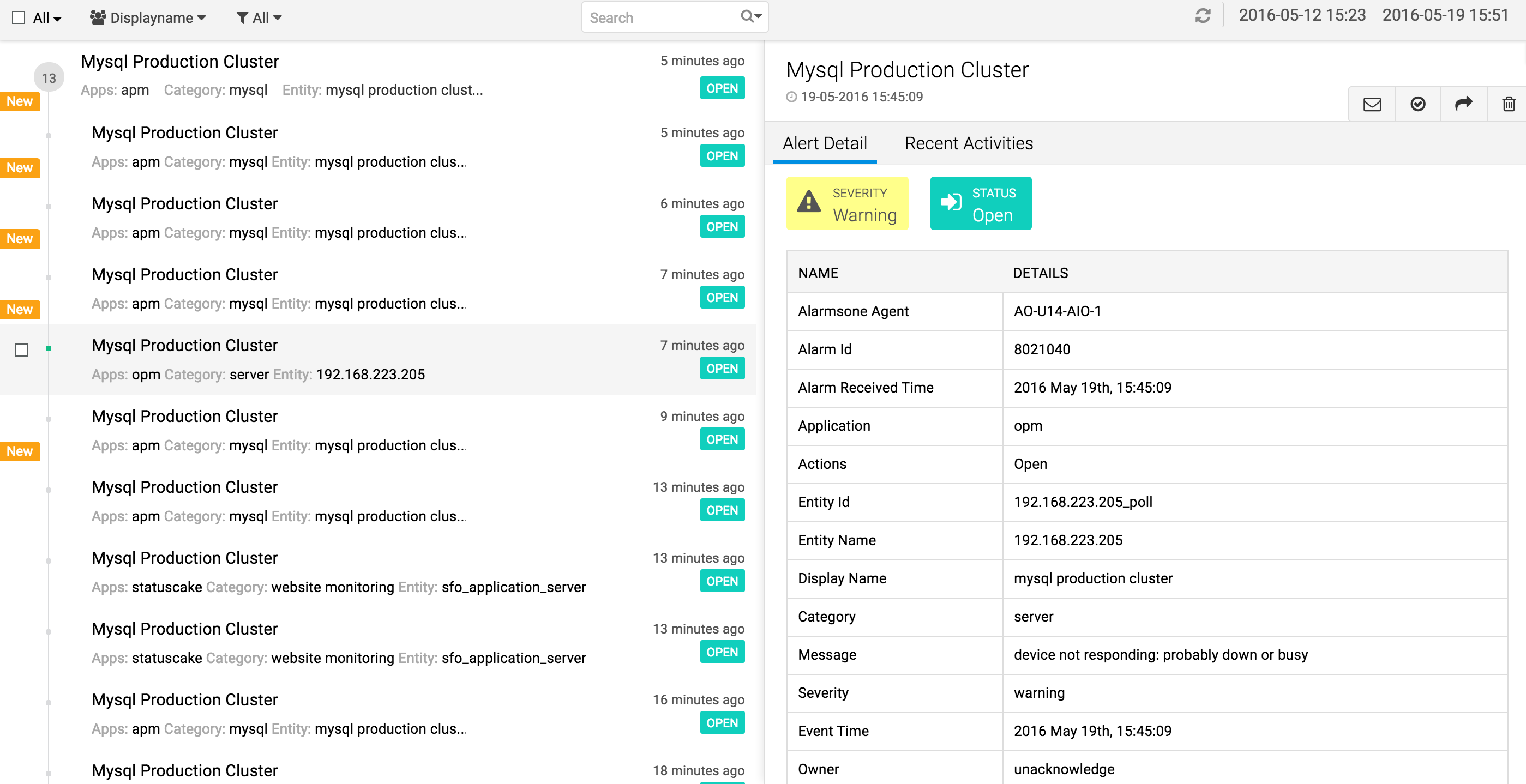
Group your alarms to focus on what matters
Let’s say that you pick up a dictionary to learn more about a word. What if the words in the dictionary aren’t in order? Then,...

Enhancing IT security with adaptive security architecture – part 2
In my previous blog, we learned about the basics of adaptive security architecture .We also learnt why enterprises need to focus on a more comprehensive...
What Private Equity Means for SolarWinds Users
Well, that was fast. Less than two weeks after SolarWinds committed to reviewing its “strategic alternatives,” the review is complete and the alternative chosen. The...
Time for SolarWinds Users to Explore Their Strategic Alternatives
Nothing like letting customers know they are important – until they are not! Recently, SolarWinds announced that it is “reviewing its strategic alternatives” with respect...
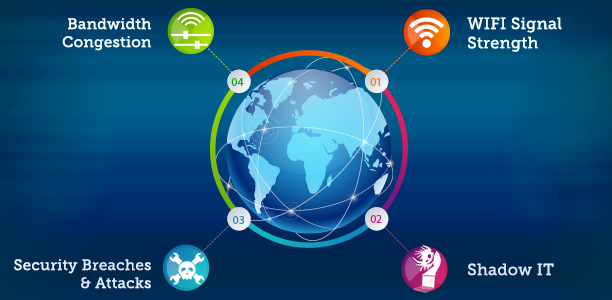
Four Things to Consider When Making Your Enterprise Network Mobile Ready
Mobile-device adoption for day-to-day business activities has been on the rise thanks to BYOD, smartphone proliferation and high-speed wireless networks. According to ABI Research, the...
