Today we’ll see what’s present in the all new ‘Calls Report‘ section, found under VQManager’s “call” tab. For the sake of simplicity, VQManager broadly...
Blog archives
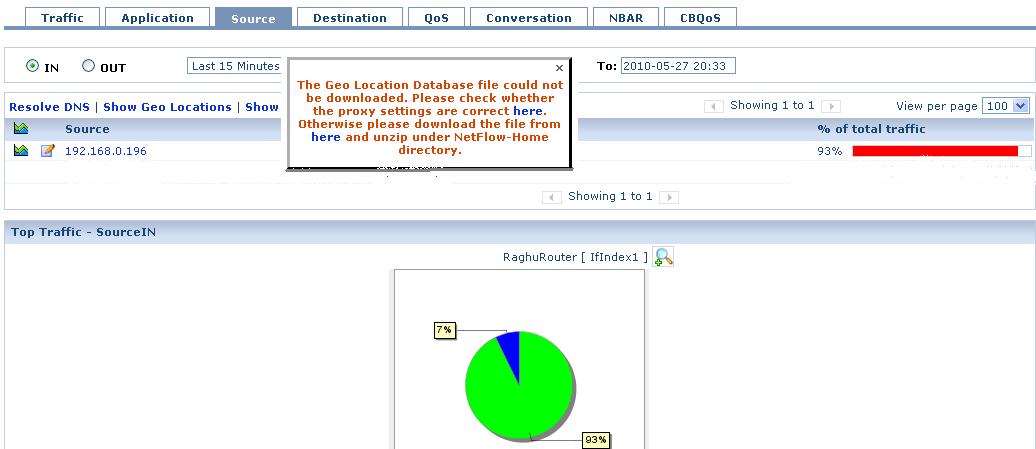
Location based Traffic Reports – GeoLocations in NetFlow Analyzer
NetFlow Analyzer has various reports which helps users monitor bandwidth, do traffic analysis, drill down on network spikes, do trend analysis and make capacity planning...
Frequently reported PXE error in OS Deployer
Hi Folks, We get requests related to PXE client-server related issue. Below given is one such popular query. The “PXE-E55 Proxy DHCP Service did not...
IT Asset Management Best Practice!
IT Asset Management (ITAM) is a vital business discipline that provides insight into a company’s information infrastructure and enhances the ability to control the performance...
Preventive Maintenance and FacilitiesDesk
Preventive maintenance is a systematic way of checking and repairing a asset, equipment, machine or vehicle. Asset life can be significantly extended by simply tightening...

What's new with OpManager 8.7 – Webinar
We’re just about ready with the latest OpManager release – version 8.7. While a lot’s there under the hood, we’re particularly pleased with two additions:...
Service Level Agreement – Hows & Whats ?
Service Level Agreements are fundamental to both providers and recipients of services. They define the terms of engagement – the rules that will govern the...
The Fastest way for Analyzing Network Spikes – NetFlow Analyzer
Traffic spikes are unavoidable in most networks – The reasons can be many, ranging from increased network traffic due to a large online backup to...
The wolf in sheep's clothing often goes unnoticed. We help trace, thwart and combat!
The biggest threat to the information security of your enterprise might be germinating inside, right at your organization! The business and reputation of some of...
