Cast your vote for ManageEngine EventLog Analyzer which is nominated for the Best Security Information Event Management (SIEM) Solution in the SC Awards 2013 US –...
ManageEngine Thoughts: Software Defined Networking #1
With Software Defined Networking (SDN) being the new industry buzzword, more and more people including network architects, CIOs and CTOs have started exploring SDN and...

World’s leading virtualization platform provider relies on Password Manager Pro to consolidate and secure privileged accounts
Success Story The R&D division of a US-based virtualization platform provider, global leader in virtualization and cloud infrastructure solutions serving over 300,000 customers experienced proliferation...
Dropbox hack unveils the absolute need for Password Managers!
In the aftermath of the data breach at Linkedin last month in which over 6.4 million hashed passwords were stolen, we had highlighted the implications...
Super-Administrator as ‘Break Glass Account’ in Password Manager Pro
In the previous post, we were discussing how to manage emergency access to IT resources when an administrator is away. The ‘Super-Administrator’ role in Password...
How do you manage emergency access to IT resources when an administrator is away?
Assume one of the administrators in your IT department happens to be away from office and an emergency situation arises when you need to access...
Bridge the gap between IT Operations & IT Security
Traditionally, IT operations and IT Security have remained at loggerheads. IT operations team is tasked with the responsibility of carrying out the the day-to-day activities,...
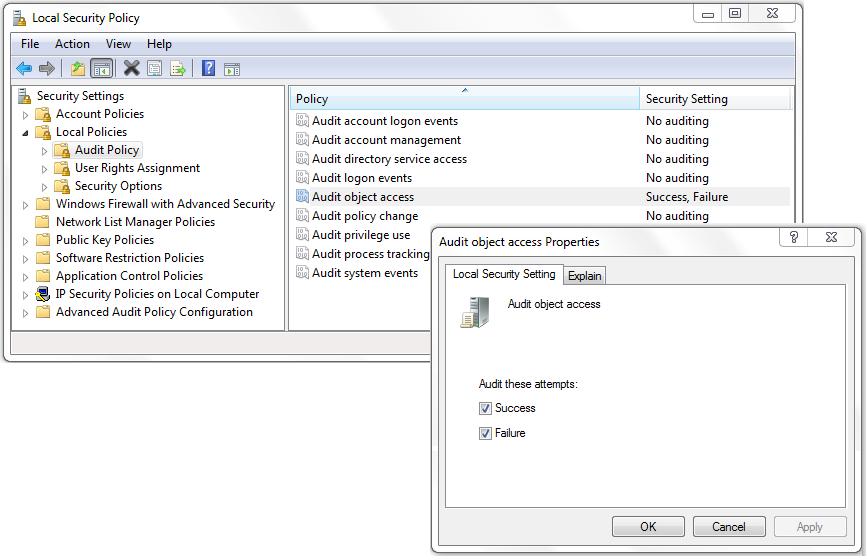
Object access auditing simplified: Find the who, what, when, and where of file and folder accesses
For many administrators face knowing what actually happened to their files and folders can be a challenge–who accessed them, deleted them, edited them, moved them,...
Data Breach at LinkedIn: Time to Seriously Consider Using a Password Manager!
Just in the last post, we were discussing how even some of the world’s mightiest enterprises were falling prey to hackers. Now comes the bad...

