For many administrators face knowing what actually happened to their files and folders can be a challenge–who accessed them, deleted them, edited them, moved them, and where the files and folders went. Object access auditing can help administrators meet this challenge head-on.
Object access auditing is a critical requirement for organizations and helps network administrators secure their enterprise network. With object access auditing, organizations can secure their business-critical data, such as employee data, accounting records, intellectual property, patient data, and financial data. One of the key goals of object access audits is regulatory compliance.
Industry standards such as
SOX,
HIPAA,
FISMA, and
PCI DSS require organizations to adhere to strict sets of rules related to data security and privacy. Unauthorized access, accidental access, files and folders deletion, changes in files and folders, or unregulated permissions opens the door for data theft and can result in your organization being non-compliant, which is not only a costly affair but will also tarnish your company’s brand value.
To enable Windows auditing for object access, first activate audits of successful object access attempts and failure access attempts via the local or domain security policy settings (see screenshot below).
 Figure 1: Enabling object access auditing in Windows
Figure 1: Enabling object access auditing in Windows
If you do not enable the above setting, you will have no record of when a file or folder was accessed. Most administrators only want to know about failed attempts to access the file or folder due to improper permissions. But it is highly recommended to audit both successful and failed activity. The reason successful accesses should be audited is that hackers can use administrator privilege and gain access to confidential files and folders.
Your enterprise will have crucial data stored in files and folders such as financial data, employee data, patient records, and bank account data. The next step is to find the files and folders containing this sensitive data and enable auditing on them. Each file and folder’s auditing settings must be modified to include those users you wish to audit.
Auditing can be enabled in Properties > Security > Advanced > Auditing. If you want to audit all access events by everyone, add the group containing everyone, and select Success > Full Control (see screenshot below).
Note:Select the attributes based on your requirements. Delete and Modify attributes are most recommended.
Enabling all the attributes to users will flood the event viewer in few seconds and consume more bandwidth. So judiciously select the attributes required for your auditing needs.
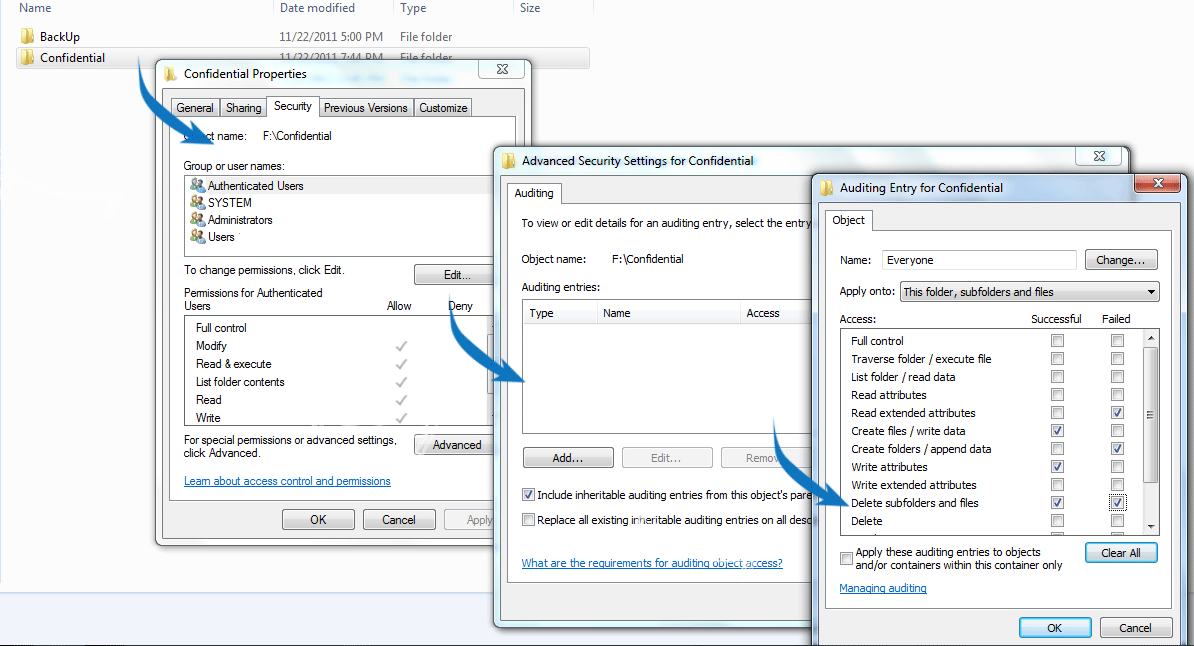
Figure 2: Object access auditing configuration on files and folders
Please refer the following links to configure object access to a specified folders and files for various Windows operating systems:
For XP: http://support.microsoft.com/?kbid=310399For Windows 2000: http://support.microsoft.com/kb/314955For Windows 2003: http://support.microsoft.com/kb/814595For Windows 2008: http://technet.microsoft.com/en-us/library/cc731607(WS.10).aspxThere are no objects configured to be audited by default. Once auditing for an object is configured, log entries on access attempts (successful and failed) start getting recorded, and you will be able to view the object-access-related events in the security log in Event Viewer (see screenshot below).
 Figure 3: Windows Event Viewer
Figure 3: Windows Event Viewer
The events must be opened up individually to inspect their contents, however, manually collecting, archiving, and analyzing object access log data is a long and mundane process and is far too time-consuming in an IT enterprise network. Automated log management solutions like
EventLog Analyzer can help network administrators automatically collect, archive, and analyze object access log data at a centralized location from all the machines present in your network.
Object access auditing with EventLog AnalyzerUsing
EventLog Analyzer, you can collect all your object access audit logs at a central location and manage your object access audit logs effectively. This log management solution can track successful and failed access attempts on folders and files in your enterprise.
EventLog Analyzer provides object access reports in user friendly formats (PDF and CSV) and sends real-time SMS and email alerts when your sensitive files and folders are accessed by unauthorized people. With EventLog Analyzer, you get precise information on object accesses, such as which user performed the action, what the result of the action was, on which server it happened, and on what user workstation or network device the action was carried out on.
The EventLog Analyzer Object Access Report dashboard is intuitively designed to shows the object access audit data in a graphical and tabular format (see screenshot below).
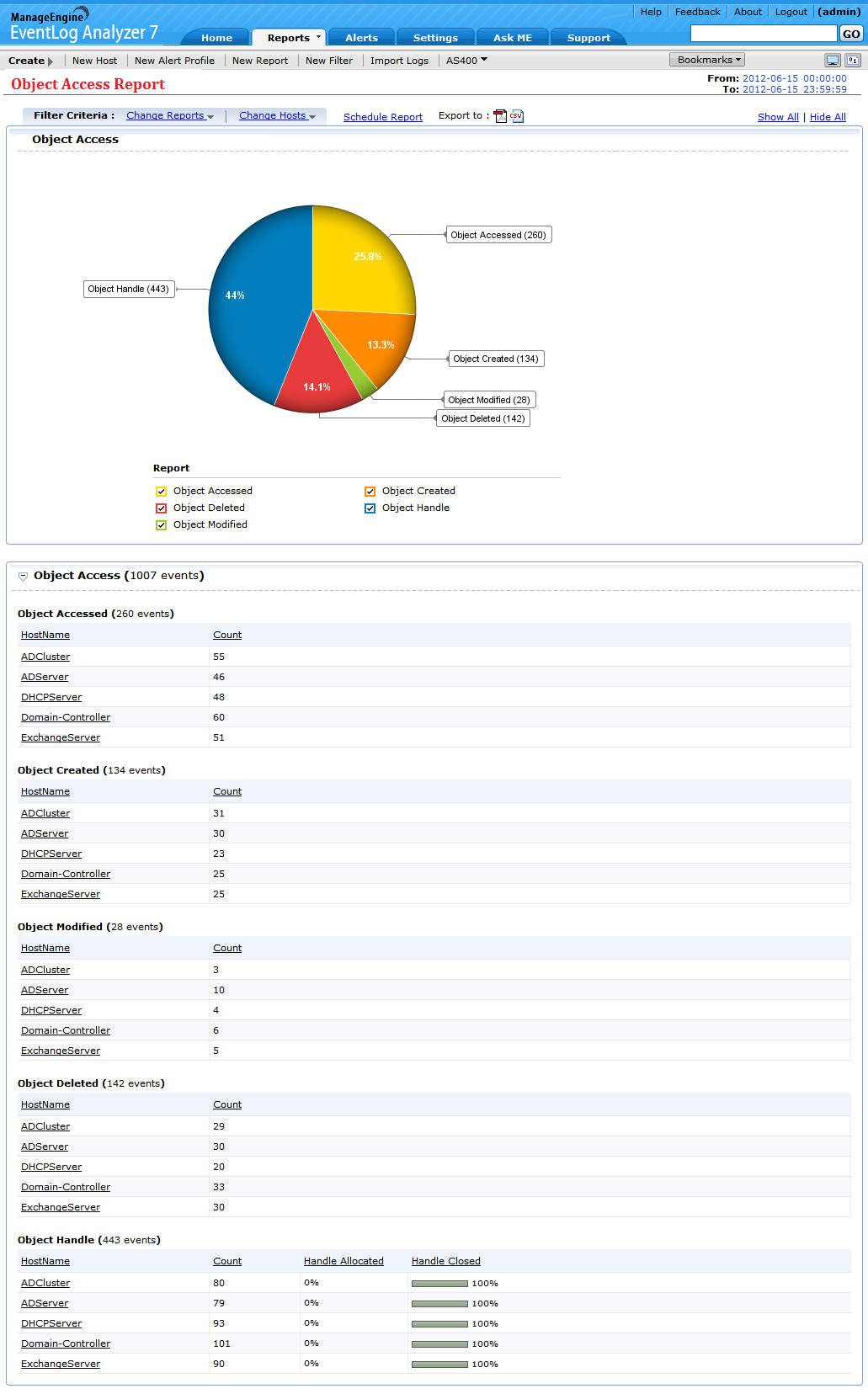
Figure 4: Object access auditing dashboard in EventLog Analyzer
The EventLog Analyzer dashboard and reports cover all the aspects of object access auditing in detail. You can drill down on the event data available on the object access dashboard and reports to get more precise information such as UserName, Domain, Severity, Event ID, Object Name, Object Type, and Time (see screenshot below).
 Figure 5: Object access analysis in EventLog Analyzer
Figure 5: Object access analysis in EventLog Analyzer
Create reports and alerts using object access audit event IDsEventLog Analyzer allows you to create reports and alerts using object access audit event IDs. In simple words, these Event IDs give detailed information on accessed, created, modified, deleted, and handled objects.
Read more on event IDs used for object access auditing.Object access event IDs for Windows OS560, 562, 563, 564, 565, 566, 567 and 568- Windows 2000
- Windows Xp
- Windows 2003
4656, 4658, 4659, 4660, 4661, 4662, 4663 and 4664- Windows Vista,
- Windows 7
- Windows 2008 and Windows 2008 R2
EventLog Analyzer allows you to create object access audit reports using the above mentioned event IDs (see screenshot below).
 Figure 6: Object access auditing reports using object access event IDs
Figure 6: Object access auditing reports using object access event IDs
Similarly, EventLog Analyzer allows you to create object access auditing alerts using the above mentioned object access event IDs (see screenshot below).
 Figure 7: Object access auditing alert configuration
Figure 7: Object access auditing alert configuration
With EventLog Analyzer, you can detect anomalous behavior in real-time, mitigate loopholes in network security, and prevent data breaches by creating a trail of user activity that happened on your files and folders. You can also use this user activity trail for
log forensic analysis.
Download the Free Edition of EventLog Analyzer now!

 Figure 1: Enabling object access auditing in Windows
Figure 1: Enabling object access auditing in Windows Figure 3: Windows Event Viewer
Figure 3: Windows Event Viewer Figure 5: Object access analysis in EventLog Analyzer
Figure 5: Object access analysis in EventLog Analyzer Figure 6: Object access auditing reports using object access event IDs
Figure 6: Object access auditing reports using object access event IDs Figure 7: Object access auditing alert configuration
Figure 7: Object access auditing alert configuration 


Hi Joel... do you know the event code for Shared Folder Access Failure? I have tried but could not find it. Thanks