The Firewall Analyzer team is constantly working on enhancements to improve its product offering. Here’s an overview of all the new vendors, log formats, and reports...

Cyberattacks are coming—is your firewall ready?
In HBO’s hit series Game of Thrones, the Seven Kingdoms had the Wall to keep out White Walkers, and for many generations, it did exactly that. But even the strongest fortifications can fall...

Is global expansion crippling your hold on network security?
Globalization and foreign investments have completely changed the way enterprises are run today. Enterprises are expanding geographically to diversify their risk portfolio, but this expansion hasn’t...
Spate of shocking cyber attacks on universities jolt academia
It is hauntingly clear – cyber criminals have set their eyes firmly on universities, research institutions, and centers of higher learning in the United States...
Your Net Worth Is Online – And Less Safe Than Ever
The Black Hat USA 2013 conference, which kicks off tomorrow in Las Vegas, brings together the brightest minds in IT security each year — those who are...

IT outsourcing: When outsiders become insiders, how do you ensure information security?
Organizations outsource a part or whole of their IT services to third-party service providers for various reasons, such as cost savings, leveraging outside expertise, need...
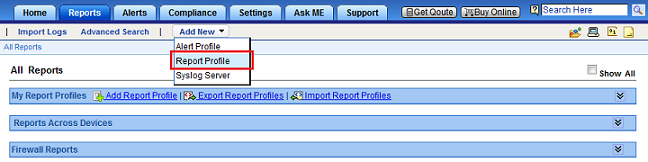
How companies can implement Internet fair use policy for corporate users?
Internet fair use policy or acceptable use policy defines the appropriate Internet usage behavior expected from employees in their workplace. The policy aims to protect the employees...
2013 SC Awards: Cast Your Vote for Firewall Analyzer
Cast your vote for ManageEngine Firewall Analyzer which is nominated for the Best Security Information Event Management (SIEM) Solution in the SC Awards 2013 US...
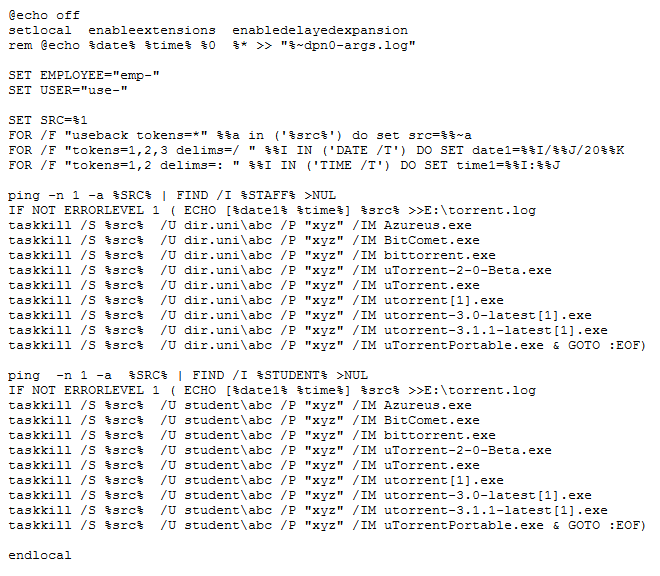
Security Event Management: Real-time Alerts and Instant Remediation
You may come across a situation, where there was a virus attack on you IT network. In another situation some of the corporate users may...