There’s a new shapeshifting strain of Android malware in the mix. It replaces legitimate apps with compromised ones and is imaginatively named Agent Smith after the iconic villain in The Matrix.
Yet another malware attack targeting Android—so what’s the big deal?
Agent Smith is similar to other malware campaigns such as Gooligan, HummingBad, and CopyCat with respect to the destruction it can cause via fraudulent ads. However, Agent Smith goes a step further than these other “agents” in how it infects devices, and that’s cause for concern.
With Google constantly trying to improve Android’s security standards, attackers are rebooting their malware campaigns so they’re intelligent enough to escape Google’s stringent measures.
Agent Smith combines three different loopholes—the Janus vulnerability, Bundle, and a man-in-the-disk attack—to create an army of botnets. According to Check Point Research, which discovered Agent Smith, this three-pronged attack is the first of its kind in the malware world.
Let’s quickly go through how Agent Smith attacks devices.
- A compromised app or set of apps is voluntarily installed by the user from third-party app stores.
- The app comes bundled with an encrypted malware kit that initially prevents Agent Smith from being identified.
- The malware kit then unpacks itself and the core malware is installed on the device.
- Agent Smith identifies the list of apps present in the device and cross-checks the installed apps with its prey list (either hardcoded in the app or dynamically obtained from a server).
- Once it identifies a target app, Agent Smith adds a malicious advertisement module to the original app.
Yeah, so just adware?
Well, not exactly. What started off as adware can supposedly also steal your banking credentials and even eavesdrop. As Agent Smith is a completely new malware campaign, the possibilities might be endless.
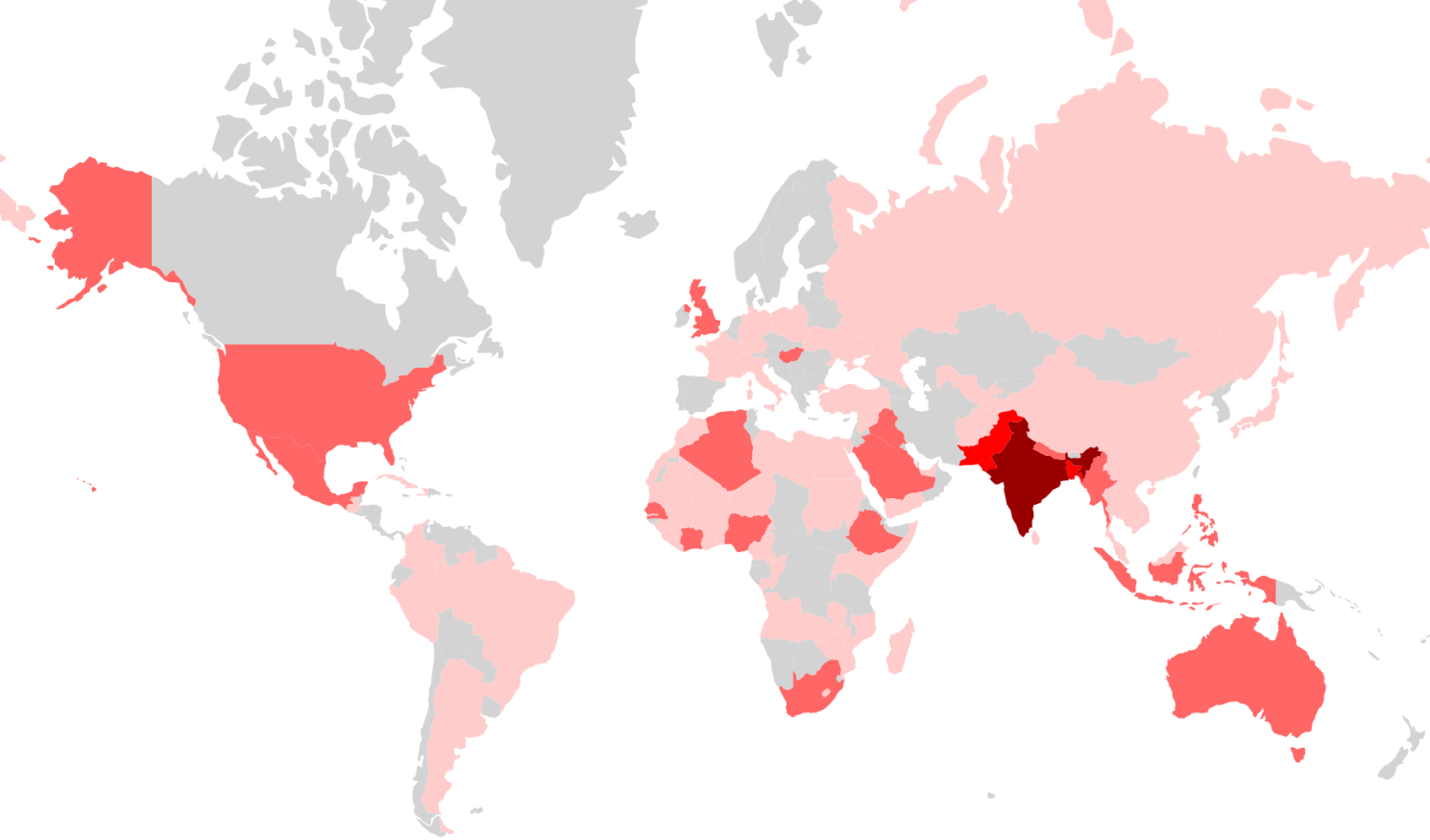
What all countries have been affected?
The image below, taken from Check Point Research, shows the countries affected by Agent Smith. More attacks have been reported in the countries displaying darker tints of red.
While India seems to be the most impacted, parts of the US, Europe, and Australia have fallen victim to Agent Smith. Check Point estimates around 2.8 million infections globally, with 303,000 in the US alone.
Which apps are acting as vectors?
While the list of affected apps is ever expanding, some of the apps that are acting as vectors for Agent Smith include WhatsApp, Xender, Opera, AppLock, and Truecaller.
Do enterprises need to worry?
Enterprises most certainly need to worry about Agent Smith for two reasons: one, the permeation of BYOD in the enterprise space, and two, the trend of newer malware campaigns to unleash seemingly infinite destructive capabilities. For instance, a newer version of WannaLocker that bundles spyware, a remote access Trojan (RAT), and a banking Trojan, recently targeted four banks in Brazil. As Google tries desperately to retain a semblance of security in Android, malware attacks are leveraging many different campaigns to affect millions of devices.
What’s the solution?
The solution lies in a mobile device management (MDM) tool. Although they’re predominantly used for device management, MDM solutions act as an excellent baseline configuration for device security as well. MDM solutions come with many policies that help you proactively protect your devices against security threats.
In enterprises with corporate-owned, personally-enabled (COPE) and/or bring your own device (BYOD) guidelines, there is an even greater need to manage apps, as these can become primary vectors for spreading malware.
- To start, you can restrict device users from installing apps from unauthorized third-party stores. If you want further security, you can completely prevent users from installing any apps.
- But how will employees install the apps they need for work? You can use an MDM solution to silently install applications, even if such restrictions are in place.
- Next, blacklist apps that your organization doesn’t approve of; aside from preventing subsequent installations of blacklisted apps, your MDM solution should also remove existing installations of unwanted apps.
- Similarly, MDM solutions let you predefine permissions for apps and ensure users cannot modify the permissions they’re granted. This ensures there is no chance of unwarranted granting of permissions, which can lead to unauthorized data access.
- MDM solutions also let you enable Google Play Protect on devices. Google Play Protect constantly scans the apps available on a device for security anomalies (no matter where the app was installed from) and keeps your data secure by ensuring the device has the necessary security updates.
- Having spoken of proactive solutions, let’s focus on a couple of reactive ones. If you discover infected apps on one of your organization’s devices and updating these apps is the best way to stop the attack, you can initiate silent app updates from your MDM tool.
- Once you’ve realized a device has been affected, it is imperative that confidential data available on the device be removed. With an MDM solution, you can choose to either completely wipe the device or at least remove the corporate data available on it.
You can use Mobile Device Manager Plus to proactively protect your devices against app-based malware like Agent Smith. Click here to get your fully-functional 30-day trial.