En cybersécurité, l’écoute de session (ou session sniffing)—une méthode d’attaque où les attaquants reçoivent et utilisent des données de session—est un danger récurrent. Les impacts...
Introducing the Zia Code Generator for Custom Functions in the cloud version of ServiceDesk Plus
We are thrilled to announce the latest GenAI capability in the cloud version of ServiceDesk Plus: Zia Code Generator for Custom Functions, powered by ChatGPT....

Top tips: Four ways organizations can reduce their attack surface
Top tips is a weekly column where we highlight what’s trending in the tech world today and list ways to explore these trends. This week,...

McLarens achieves 24/7 availability and uptime with Applications Manager
Uptime and IT resources availability are critical metrics for maintaining efficiency, flexibility, and scalability in the financial services industry. The continuous operation of financial technology...
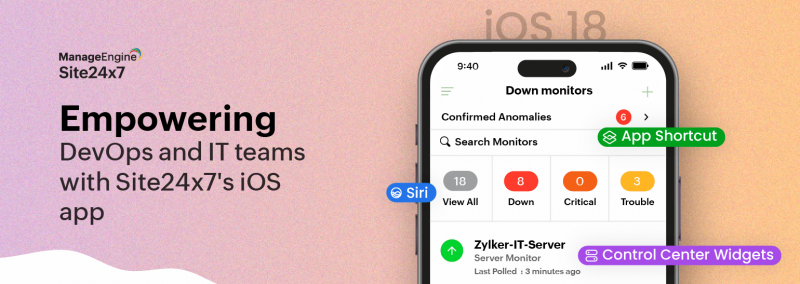
Empowering DevOps and IT teams with Site24x7’s iOS app
With the release of iOS 18, Apple has once again pushed the boundaries of innovation. At Site24x7, we’re committed to providing our users with the...
ManageEngine named as a Challenger again in the 2024 Gartner® Magic Quadrant™ for Privileged Access Management
We are elated to announce that ManageEngine has again been recognized as a Challenger in the 2024 Gartner® Magic Quadrant™ for Privileged Access Management. We...

Top tips: How to Marie Kondo your digital life
Top tips is a weekly column where we highlight what’s trending in the tech world today and list ways to explore these trends. This week,...

[Webinar series] Boost your MRR and ROI: MSP essentials with ManageEngine
The MSP market is projected to grow at a CAGR of 6.2% over the next five years. However, this growth depends on balancing customer acquisition...
Applications Manager mobile app: More secure than ever
We are thrilled to announce that Applications Manager now integrates with Microsoft Intune to make your application performance monitoring (APM) experience from your mobile device...
