Among the different types of cyberattacks, insider threats are the hardest to track and have the highest rate of success. This can be attributed to...

Detecting first time processes on member servers to protect against attacks
In a previous blog, we saw how ADAudit Plus’ user behavior analytics (UBA) capabilities allow administrators to monitor user logon activity to identify compromised accounts....

Monitoring user logon activity to identify compromised accounts
In a previous blog, we saw how ADAudit Plus’ user behavior analytics (UBA) capabilities allow administrators to monitor the file activity of users to identify anomalies. UBA in ADAudit...

Unmask malicious insiders with user behavior analytics
Insider threats are both the most successful way to exfiltrate sensitive business data and the hardest cyberattack to detect. This is because these attacks are carried out using...

[Infographic]Three tips to simplify Active Directory compliance and auditing
In the previous blog of this series, “[Infographic] Still manually onboarding users into Active Directory? There’s a better way!“, we discussed the tips and tricks to...

Quick tips to ensure your Azure AD is safe from threats
Being the gatekeeper of Microsoft’s cloud solutions, Azure AD comes with a wide range of default security measures; these include insights on risky sign-ins and user accounts that...
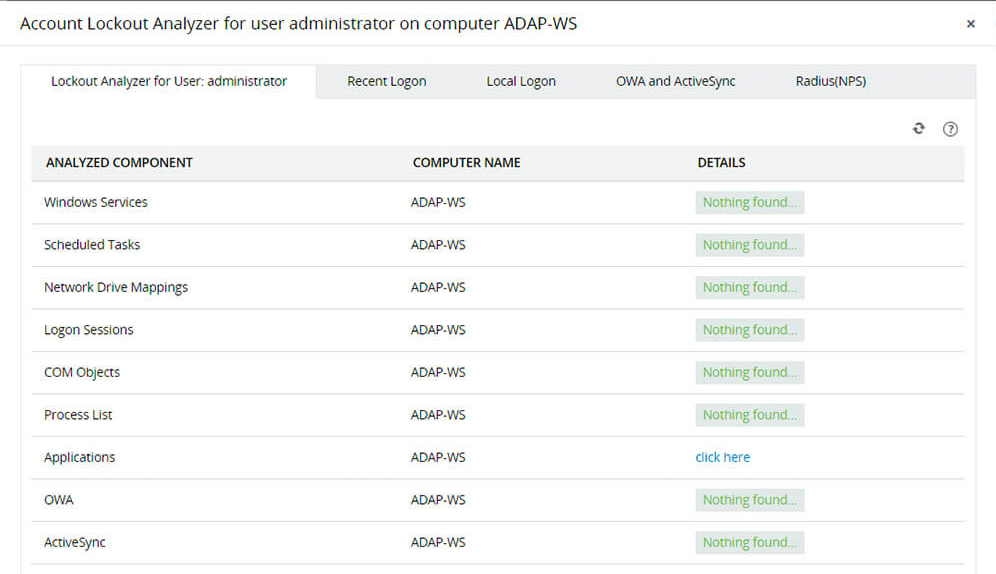
Account lockout and management tools
.whatSection a {
background: #e9142b;
border-radius: 3px;
color: #fff;
font-size: 14px;
font-weight: 300;
padding: 15px 40px;
text-decoration: none;
transition: all 1s;
}

ADAudit Plus Voted WindowSecurity.com Readers’ Choice Winner
Talk about a wonderful holiday gift: Leading Windows security resource site, WindowSecurity.com, recently announced that ManageEngine ADAudit Plus was voted the winner in the Network Auditing...


