Imagine all your online activity being put out in the open—as private as a billboard in Times Square. Before SSL, your private internet information was vulnerable to exposure. However, with the advent of SSL, encryption became part of how the data was transferred between web browsers and servers, ensuring privacy and security.
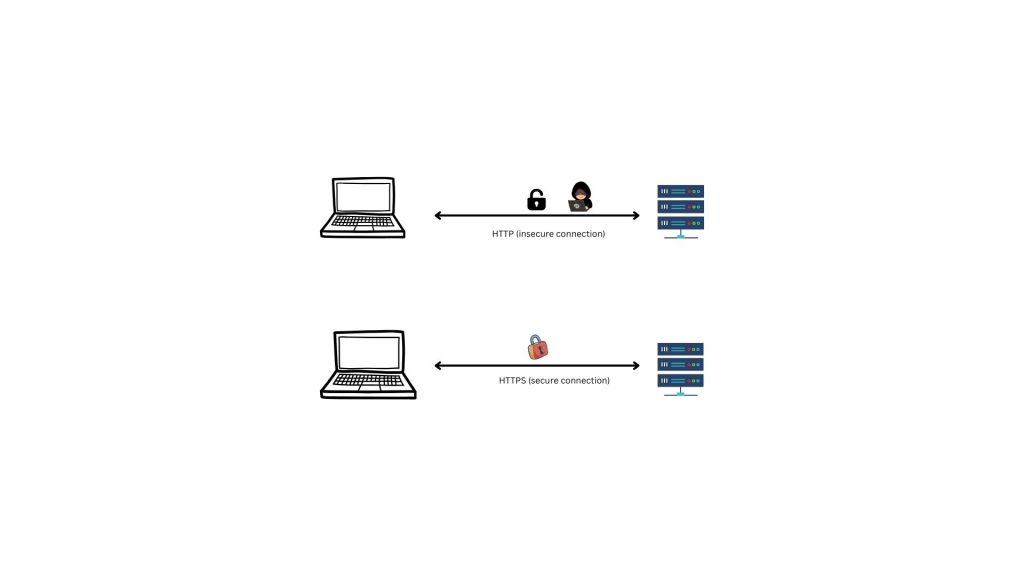
SSL transforms regular HTTP into the more secure HTTPS, safeguarding your online activities.
So, next time you see that little lock icon in your browser, know that SSL is protecting your online escapades. Also, SSL is the older version of TLS and is different in terms of version history, handshake protocols, etc. Click here to read more about the key differences of TLS and SSL.
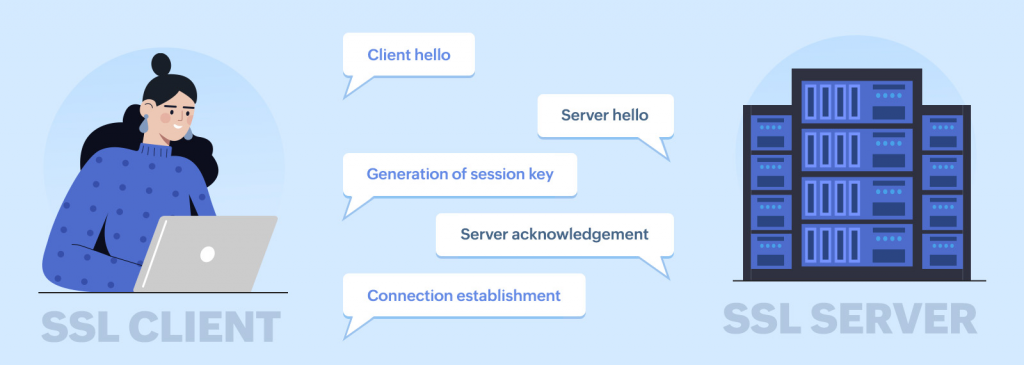
How does SSL work?
SSL turns your data into an unreadable code in three easy steps that leaves eavesdroppers scratching their heads.
Step 1: Encryption
Your data gets turned into a jumbled mess of characters that is impractical to decode. The data can be decoded only with a session key that is exchanged between the server and the client.
Step 2: Authentication
SSL initiates a handshake between devices to make sure they’re not impostors. It’s like a password exchange to confirm: “You are who you say you are, right?”
Step 3: Data integrity
SSL digitally seals your data to make sure no one tampers with it. This ensures what you sent is exactly what you received, like a digital “Do not open until delivery” label.
SSL protocols:
1. SSL Record protocol:
The SSL Record protocol is like the secret agent of the SSL connection. The two components of the protocol are:
Confidentiality: Making sure your online activity is nobody else’s business
Message integrity: Ensuring your data doesn’t get tampered with on its way
2. Handshake protocol:
The client and server ping-pong messages back and forth to establish a secure session, like a digital version of the secret handshake, but with certificates and key exchanges instead.
Round 1: The client and the server exchange secret codes and protocols.
Round 2: The server presents its SSL certificate and provides the client with the key to encrypt its data then dramatically exits the stage with a “server-hello-end” message.
Round 3: The client eagerly responds by flashing its certificate and executing some impressive client-exchange-key moves.
Round 4: The change cipher suite marks the end of this exhilarating handshake protocol. This stage confirms that the data transferred has been sent securely.
3. Change-Cipher protocol:
This is where the SSL record output changes from the pending state to the current state, like flipping a switch from maybe secure to definitely secure.
4. Alert protocol:
It is responsible for conveying SSL-related alerts you if a certificate is sketchy.
SSL certificate
This is the digital bouncer of the internet, making sure only legit websites and services get in. Issued by a trusted third party, certificate authority, the SSL certificate is used to secure and verify the identity of a website. Its characteristics include:
Encryption: A secret code that scrambles your sensitive information.
Authentication: The website’s identity gets a thumbs-up or thumbs down.
Integrity: With the power of message authentication codes (MACs), no cybercriminals can mess with your data in transit.
Non-repudiation: Ensures that no party can deny that it sent or received a message via encryption.
Public-key cryptography: SSL facilitates a secure exchange of encryption keys, making sure that only the right folks can decode your encrypted data.
Session management: Your secure cyber hangout, so you can pick up where you left off without the hassle of starting a new security handshake every time.
Key differences between SSL and TLS:
|
|
SSL |
TLS |
|
Version history |
SSL is replaced with TLS. |
TLS has moved through versions 1.0, 1.1, 1.2, and 1.3. |
|
Activity |
It is now outdated. |
TLS versions 1.2 and 1.3 are actively used. |
|
Alert messages |
Has only two types of alert messages and are unencrypted. |
Alert messages are encrypted and more diverse. |
|
Cipher suites |
Supports older algorithms with known security lapses. |
Uses advanced encryption algorithms that are impossible to decode. |
|
Handshake |
Complex and slow. |
Has fewer steps with faster connection. |
