A ransomware attack is a bug that we can’t shake off. Or perhaps, it can even be called a shape-shifter that somehow finds a way into networks, no matter how many armed sentries you’ve deployed in and around your perimeter.
The line between ransomware and a data breach is slowly fading. Threat actors prefer ransomware over other modes of attack because they work. Cybercrime Magazine forecasts a new ransomware attack every 11 seconds in 2021, up from every 40 seconds in 2016, and every 14 seconds in 2019. Ransomware attacks are easy to launch, extremely difficult to trace back to the source, and yes, they’ve evolved. Here’s why ransomware attacks will be worse in 2021.
It’s not just encryption anymore, it’s double extortion
An example of a typical ransomware attack:
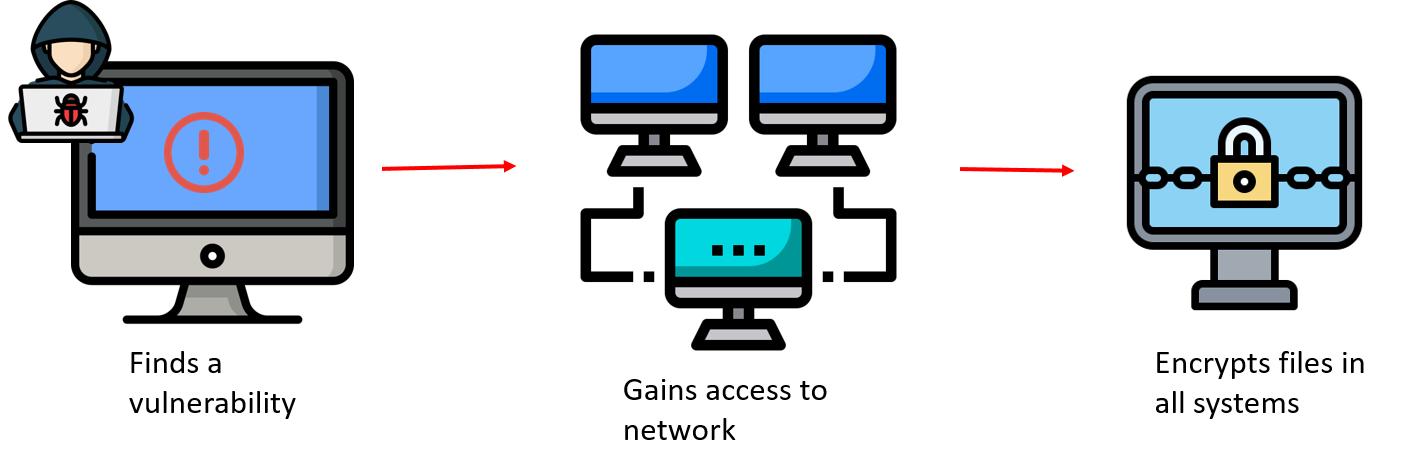
Many victims have survived devastating ransomware attacks, thanks to their backups stored in a secure location that couldn’t be encrypted by the ransomware. Using the backups, the victims just restore the files and go on with life; there is no reason to even engage with the threat actor. Now, threat actors have escalated their attacks. Cybercriminals have devised a new strategy where they not only hold the machines hostage, they also siphon sensitive data from these machines and threaten to release it to the world if the targets fail to meet their terms.
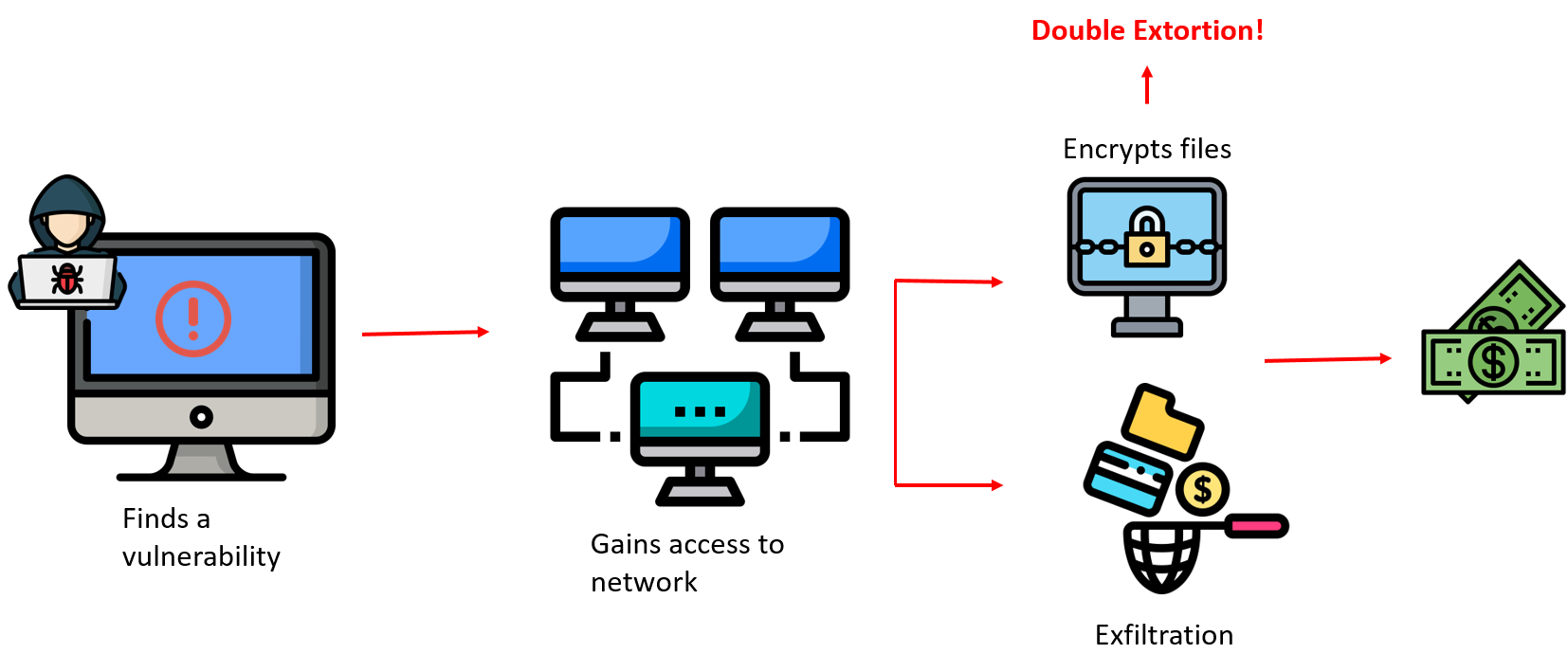
Almost 50 percent of ransomware cases in 2020, in addition to encrypting the data, also included the threat to release exfiltrated data. Studies about ransomware state that that “as little as 5GB and as much as 400GB of compressed data are being stolen from a victim prior to deployment of the ransomware.”
Ransomware operators don’t always oblige when ransom is paid
Surprise, surprise! Attackers cannot be trusted. Although victims may decide there are valid reasons to pay—to either prevent the public exposure of stolen data or to restore their encrypted data, it is important to note:
-
Threat actors might not return the pilfered files even after the ransom is paid.
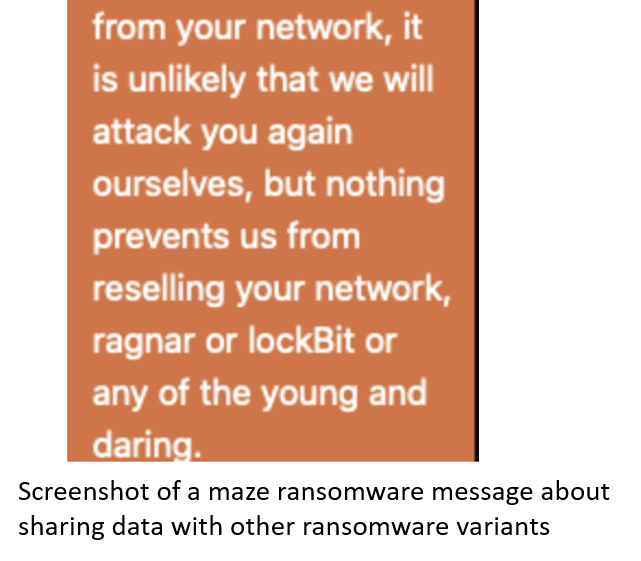
The data could be traded to other threat actors, sold, held for a future extortion attempt, or exposed even before the ransom is paid. For instance, here’s an extract of a message maze ransomware operators gave to the victimized organizations. The phrase “young and daring” refers to other ransomware variants or families.
What was the most prominent reason for ransomware in 2020?
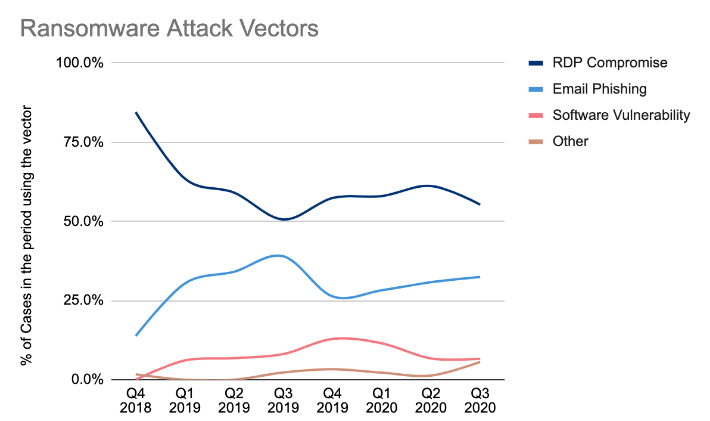
This illustration, from a recent survey, shows the combined aggregate data of ransomware cases. Exposed remote desktop protocol (RDP) credentials was a major factor in ransomware incidents in 2020. According to the survey, “the supply of already compromised RDP credentials is so large, that the price is actually decreasing. This is an alarming sign as it signals that supply is outstripping demand.”
The attack vectors also vary based on the size of companies. Since smaller companies cannot pay millions of dollars in ransom, hitting them fast and hard with exposed RDP credentials is a threat operator’s best bet. Email phishing and software vulnerabilities are viable for larger companies because these techniques are more involved and the payout justifies the effort on the attacker’s part. After the initial infection, the next step is to obtain domain admin privileges, and infect the entire network with the ransomware virus.
In a nutshell, the new ransomware attack strategy of 2021 looks like this:
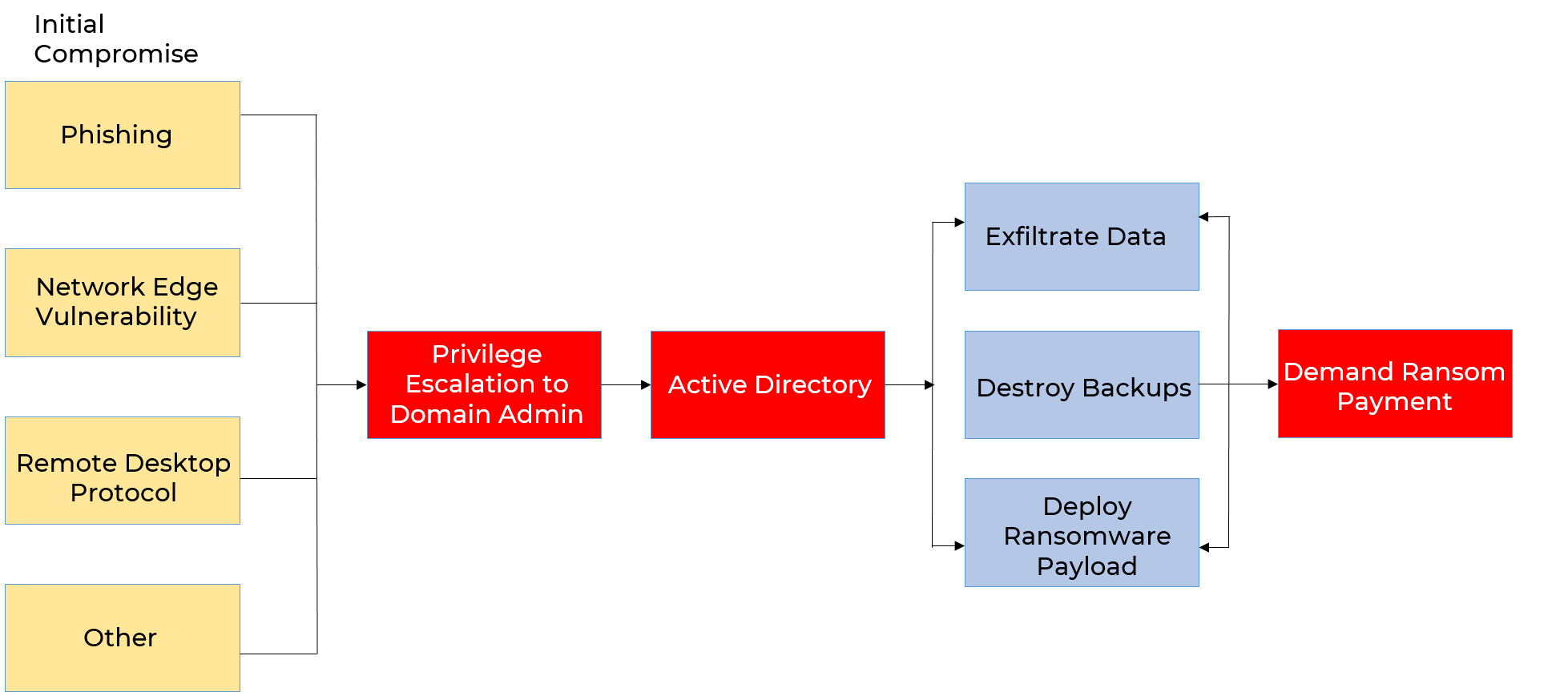
Threat actors don’t just target on-premise environments; but also target the public cloud, like Azure AD or Amazon Web Services.
Check out the short video below to learn more, and sign up at our page to learn how to build a defense against ransomware attacks, both on-premises and cloud!
How can we put an end to the reign of ransomware?
While the attack vectors mentioned earlier are among the most common and useful for stopping a ransomware attack in its tracks, intrusion may happen via other vectors too. Numerous ransomware-struck victims realized a terrible surprise when an attack occurred due to a vector that they never considered.
A ransomware attack is divided into various stages. At every stage, changes are made to your network. These changes must be must be discovered and correlated on time, so that the presence of ransomware can be detected. Take a look at the attack chain below:
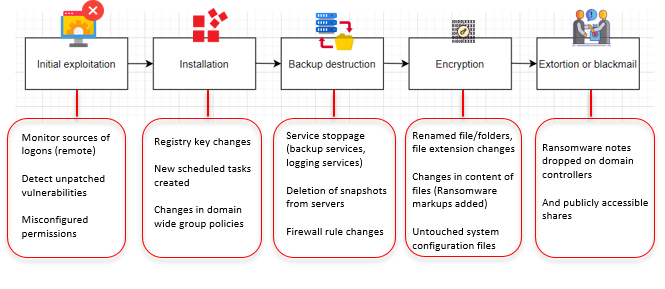
ManageEngine Log360 monitors various components of your network for the presence of ransomware (refer to the illustration above), and delivers alerts in real time.
Want to learn more? Sign up on our IT security under attack page, discover from a technical perspective how ransomware attacks occur, watch video simulations of attacks, and check out the Solution tab to learn how Log360 can help.
Leave a comment below if you’d like to start building your defense against ransomware and security breach attempts on your network. The Log360 team will reach out to you shortly.
