ADAudit Plus User Logon Reports, Part 1: Logon Failures

ManageEngine ADAudit Plus is a real-time change auditing and reporting software that fortifies your Active Directory (AD) security infrastructure. With over 250 built-in reports, it provides you with granular insights into what's happening within your AD, such as all the changes made to objects and their attributes. This can include changes to users, computers, groups, network shares, and more. ADAudit Plus accomplishes this by monitoring privileged user activities in the domain, tracking logons and logoffs on workstations, and providing visibility into AD account lockouts.
In this ADAudit Plus Reports blog series, we will be looking at the numerous reports the product provides.
The User Logon Reports category features 16 pre-configured reports that provide granular details through audit information related to user logons, logon failures, users logged into multiple computers, and more.
In our first blog of this series, we will talk about the first report in the User Logon category, the Logon Failures report.

It is crucial for any IT admin to audit the logon events in AD, as a failed logon attempt can indicate a potential threat. A simple-looking logon failure could result from either:
an employee who genuinely forgot their login credentials
an adversary attempting to brute-force the network through a legitimate but compromised user account
It is of paramount importance to monitor failed logon attempts in AD.
Let's meet James, an IT admin who wants to track all users with failed logon attempts, and find out the source and details behind these events.Problem: How to track failed logon attempts, find their source, and review key details
Solution: ADAudit Plus helps James pull up a report on all the failed logon attempts with information like who and from where they attempted to log on, the reason for their logon failure, when they tried logging on, and much more.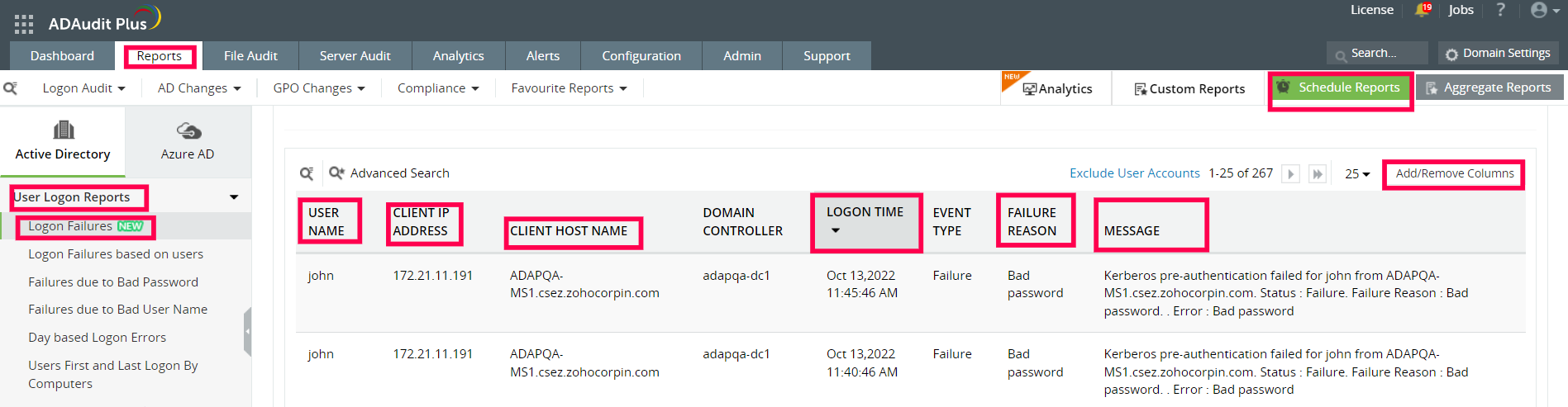
Figure 1. This screenshot shows the Logon Failures report in ADAudit Plus
The report also provides James with:
The username of the account that had a logon failure.
The IP address of the user.
The computer on which the failure took place.
The reason for the failed logon, for instance, bad password.
The time when the logon failure happened.
A message that gives granular details on the failure. For example, specific details about the "bad password" such as the failure of Kerberos pre-authentication.
Further, James can perform the following actions on the generated report:
1. Select Export As to generate the report in any of the preferred formats (CSV, PDF, HTML, and XLS).
2. Schedule these reports to run at a preferred time for automatic periodic reporting and send it to his email address.
3. Use the Add and Remove column links available in the report to select additional attributes.
4. Generate reports by selecting multiple domains.
The Logon Failures report can be further classified based on three categories:a) Logon Failures based on users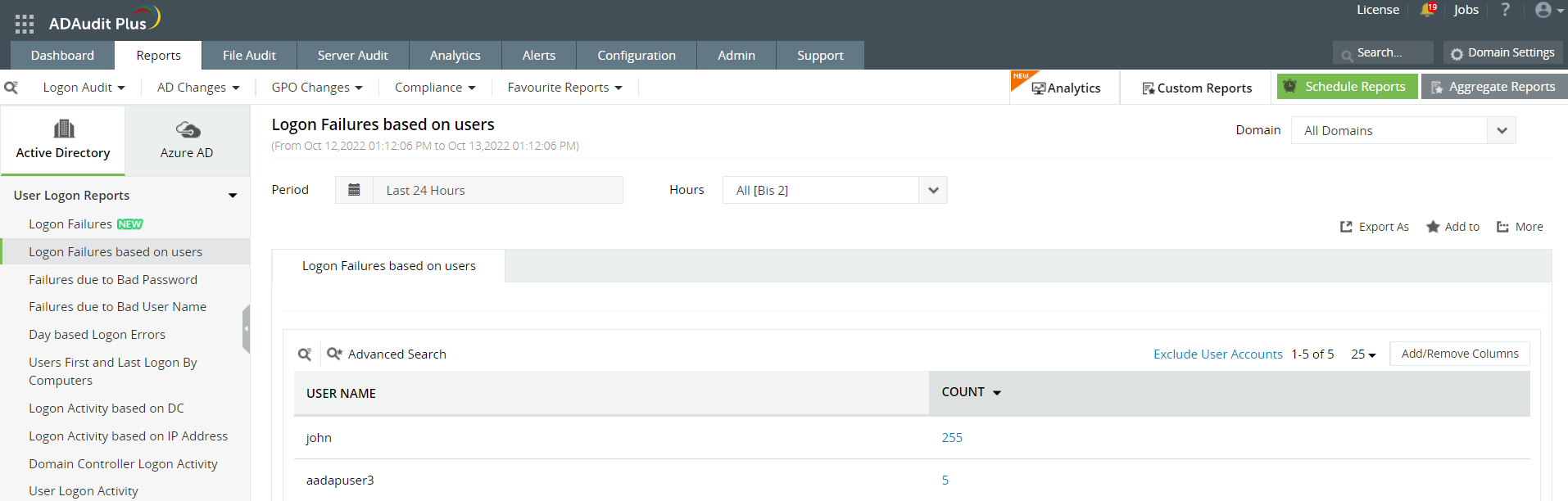 This report pulls out all the logon failure events based on the users. You can click on the "Count" associated with individual user and further deep dive into the details associated with their logon failure event such as User Name, Client IP address, Client Host Name, Domain Controller, and Logon Time.b) Failures due to Bad Password
This report pulls out all the logon failure events based on the users. You can click on the "Count" associated with individual user and further deep dive into the details associated with their logon failure event such as User Name, Client IP address, Client Host Name, Domain Controller, and Logon Time.b) Failures due to Bad Password 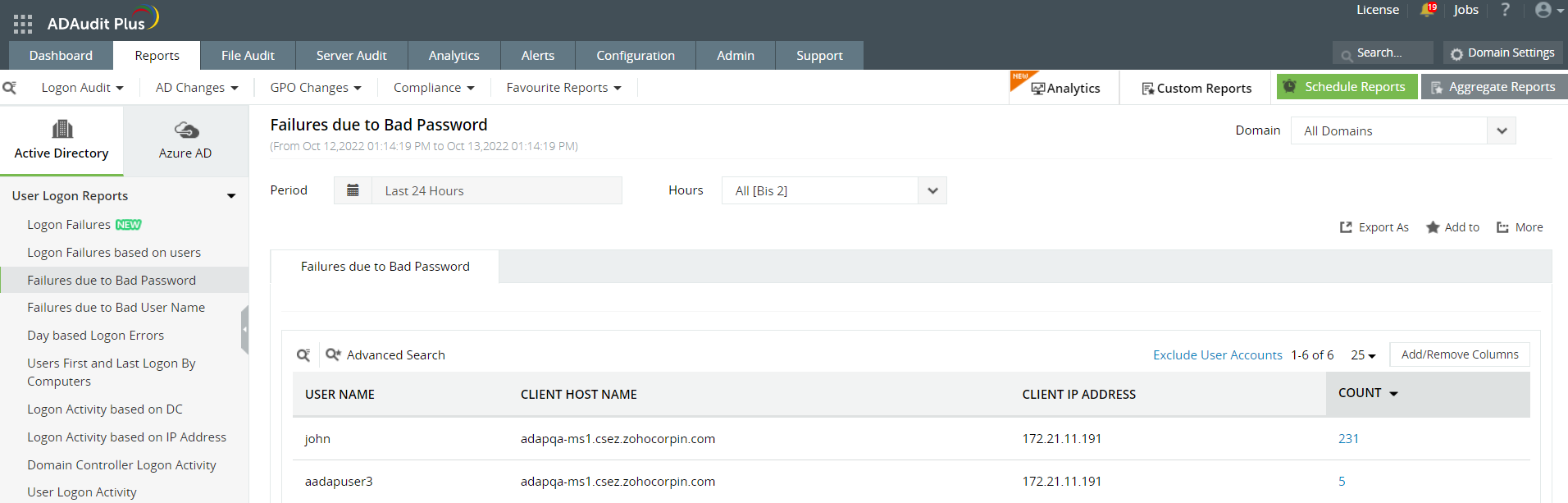
In this report, after clicking Count the report will pull out all the logon failure events where the Failure Reason is Bad Password, along with other attributes like User Name, Client IP address, Client Host Name, Domain Controller, and Logon Time.
c) Failures due to Bad User Name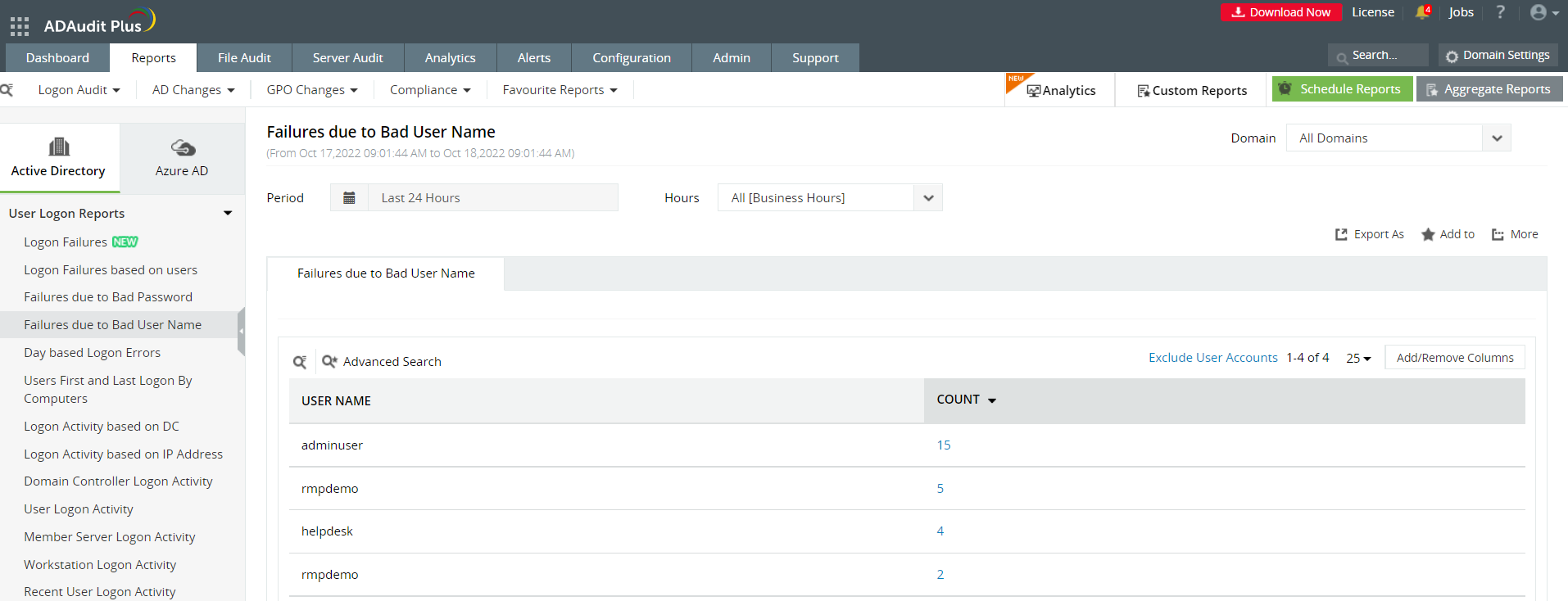
In this report, on clicking Count the report will pull out all the logon failure events where the Failure Reason is Bad User Name along with other attributes like User Name, Client IP address, Client Host Name, Domain Controller, and Logon Time.
Sign up today for a personalized demo with our product experts to learn how ManageEngine ADAudit Plus can help you monitor and secure your AD environment.
How to resolve the issue Bad password failure of Kerberos pre-authentication