
More organizations than ever before have shifted to a hybrid work culture to reduce the impact of COVID-19. This unprecedented change has not only given rise to new security challenges, but has also considerably increased the surface area available for an attack. A blend of personal and corporate endpoints in use, geographical spread of resources, and a sharp spike in the overall number of security threats have further complicated the already labor-intensive security landscape.
Given that the hybrid work culture is considered the future of the digital workforce, it’s imperative that organizations adapt quickly to combat these new security challenges. Fortunately, there’s a solution: Creating a resilient cybersecurity framework.
If there’s one thing we can learn from the long history of cyberattacks, it’s that it’s nearly impossible to attain complete cybersecurity with virtual walls alone—walls such as, firewalls, anti-spyware, anti-malware. It is, however, possible to attain cyber resilience. This involves building processes and systems to be easily traceable, rendering them difficult to attack and minimizing the impact when attacks do occur.
IT teams and security teams
Building a resilient security framework begins with understanding how security is handled in most organizations. Traditionally, cybersecurity has been the responsibility of security teams while IT teams handle break/fixes in hardware and software components. Some organizations give IT teams security-related tasks that include managing passwords or general device security; but now that these tasks have either become automated or shared with end users, it’s time for IT teams to shift their focus away from redundant tasks and focus on more challenging security tasks.
Other factors that make it ideal for IT teams to take on security is that they already plan, manage, and maintain hardware and software, networks, and data storage facilities. So, they’re already well versed in how these systems work. With just a little training, IT teams can learn to tackle security challenges by focusing on vulnerability scanning and threat discovery. This frees up security teams to focus on performing security information and event management (SIEM), centralizing security and risk assessment, and establishing strategies to combat new and evolving threats.
Let’s take a closer look at ways IT teams can help security teams in their quest to establish a resilient cybersecurity model.
Increase endpoint visibility to monitor compliance and risks
Mobile applications and endpoints are primary attack surfaces due to the combination of devices in use—corporate, BYOD, rented, and DAAS devices. With so many devices and device types, IT teams might feel overwhelmed at first. However, since the IT teams also act as facilitators for these devices to enable employee productivity—by installing software or applications required by employees for their work—they are in a better position to enforce the security of these devices.
With complete visibility on endpoints, IT teams can monitor all endpoints, restrict the use of non-compliant, compromised, and jailbroken devices, and ensure only healthy and compliant endpoints access secure corporate networks.
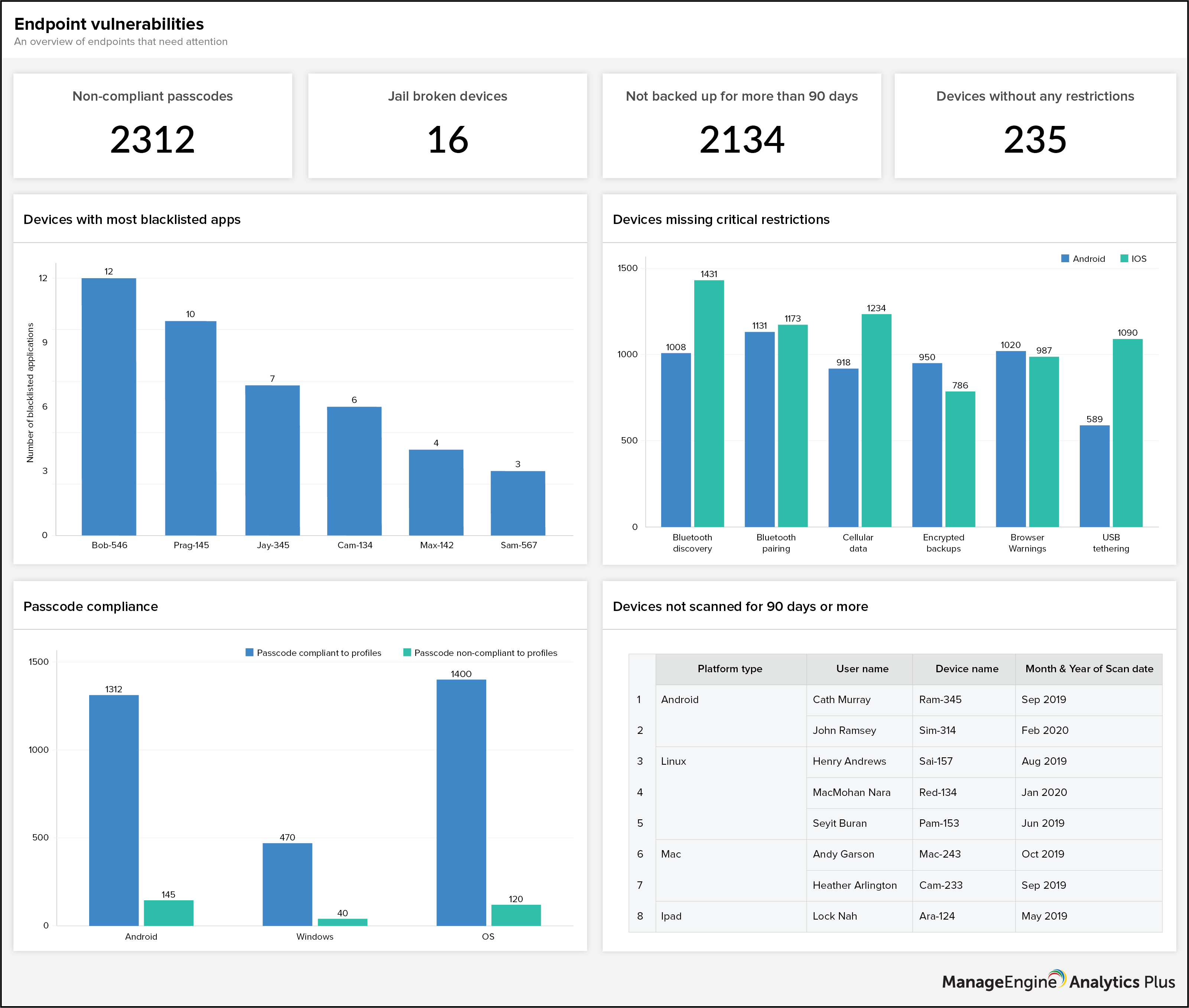
The dashboard above sheds light on the compliance and security status of endpoints, prompting IT teams into action. By tracking and monitoring devices with blacklisted apps, devices with missing critical restrictions, and devices that are non-compliant with passcode policies, IT teams can enforce policy controls to make sure data leaks or security breaches don’t happen through these endpoints, thereby reducing the potential surface area available for attack.
Conduct frequent threat assessment to identify critical systems
The de-facto rule for high-performing security teams is to perform frequent threat assessment and identify critical systems. The blunt reality is the volume of threats keeps mounting. The only option for security teams is to patch their systems and devices to keep them protected from new and emerging threats. Additionally, a thorough threat assessment allows IT teams to prioritize risks and identify systems that need to be patched first.
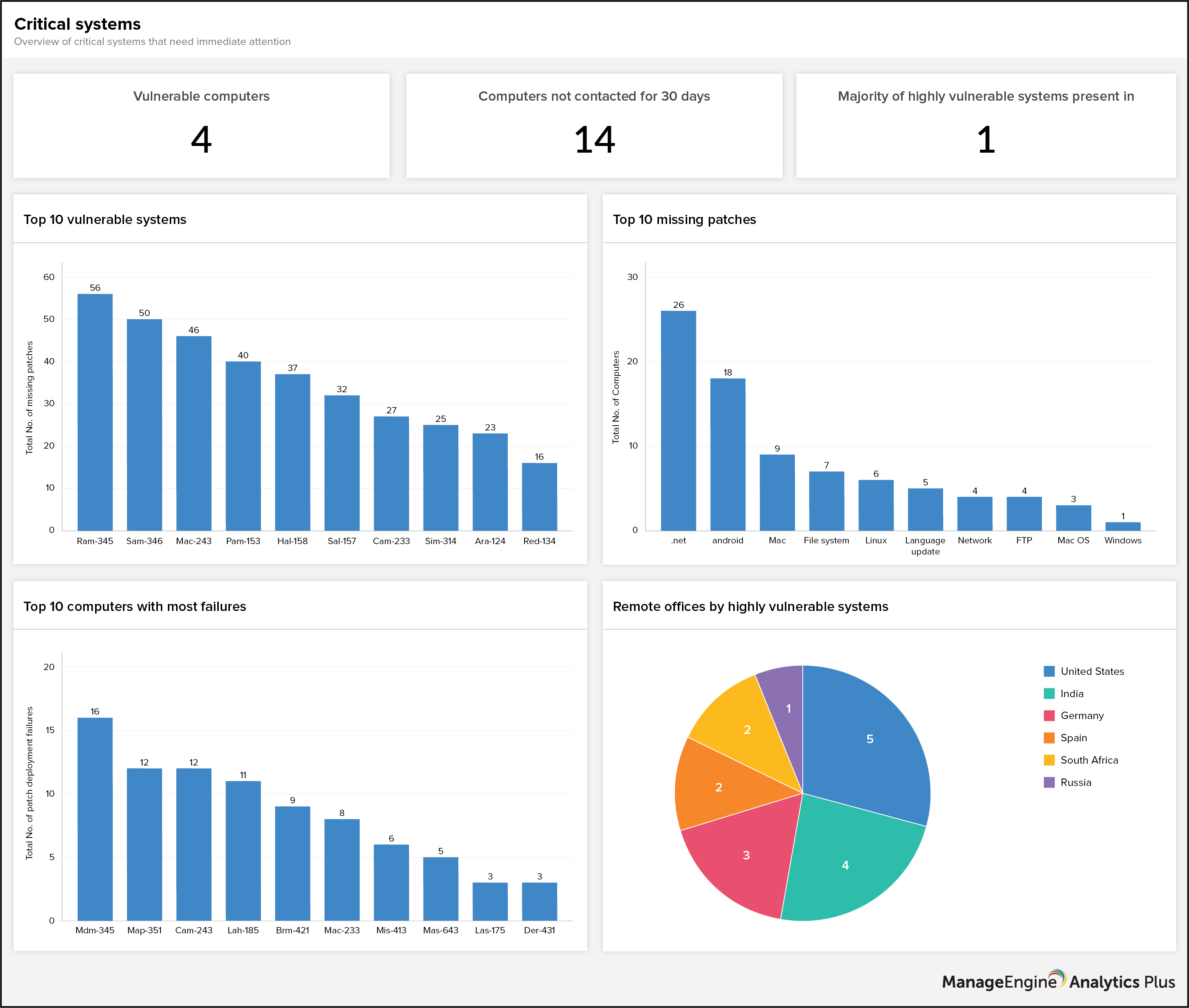
The dashboard above is a good way to identify systems that are most vulnerable. Typically, systems missing the latest patch updates are prone to security breaches. In fact, the Top 10 missing patches report highlights that four of the top 10 missing patches are security related. Performing these security scans frequently will provide IT teams with valuable information that they can use to prioritize and fast-track patch updates, and prevent security threats and black swan events.
Integrated solutions are the need of the hour
Despite the hyper-awareness to security among organizations, a lack of integrated systems that offer a comprehensive view of IT infrastructures prevents IT teams from identifying threat signals and signatures, leaving them vulnerable. A highly flexible and customizable analytics solution like Analytics Plus, can integrate with all your IT security applications, and present a unified view of your security status in a single console.
With Analytics Plus, organizations can:
-
Assess multiple vulnerabilities simultaneously to identify the ones that need immediate attention.
-
Leverage the power of artificial intelligence, machine learning, and natural language processing to identify hidden patterns in IT data.
-
Use trend forecasting to predict resource requirements to combat seasonal changes in the security landscape.
-
Create meaningful alerts, and get notified whenever immediate action is required.
-
Have real-time conversations with other users over shared reports and dashboards without ever leaving the Analytics Plus console.
Get started with a free, 30-day trial of Analytics Plus.
If you’re an existing user, click here to upgrade.

