
Since March 2020, millions of employees have been plunged into a global work-from-home experiment. This poses serious security concerns for organizations because:
1. The responsibility to ensure data security now leans more on individual employees, rather than as a shared concern between employees and the security team.
2. Endpoint devices are more prone to phishing attacks, malware, and spyware attacks now that they are connecting from open and personal networks.
3. Virtual private networks (VPNs) tend to get clogged with everyone connecting at the same time prompting people to turn off their VPN. This means endpoint devices may not receive patches or security updates on time, leaving them exposed to critical vulnerabilities.
4. An ever-expanding umbrella of endpoint devices, made up of personal and corporate-issued devices, requires constant attention from security and IT teams.
With the new normal adding several more challenges and variables to the security layer, how do you ensure your data is safeguarded without increasing the workload or the headcount of your security team? Using advanced analytics, in tandem with endpoint monitoring applications such as ManageEngine’s Mobile Device Manager Plus and Desktop Central, will help you better visualize and analyze your endpoint data, identify patterns, and establish correlations. This way, you can easily keep an eye on your endpoints, look for and confirm unusual activity, and buy time to secure your endpoints without increasing headcount.
Here’s a simple, three-step guide for using advanced analytics to ensure endpoint security while your organization is working remotely.
1. Discover
Discovering endpoint devices is the first line of defense because it would be impossible to secure a piece of hardware unless you know what and how many of them there are in existence. When they’re working remotely, more and more employees are using a variety of personal gadgets for work. This poses a challenge for IT teams, as they have to manage various devices running on different operating systems (OSs). Say you’re planning a patch update for personal Android devices, it helps to know the number of devices to formulate a solid software patch update plan.
The graph below is a sample report showing the distribution of corporate-owned and personal, or bring your own devices (BYOD), running on various OSs.
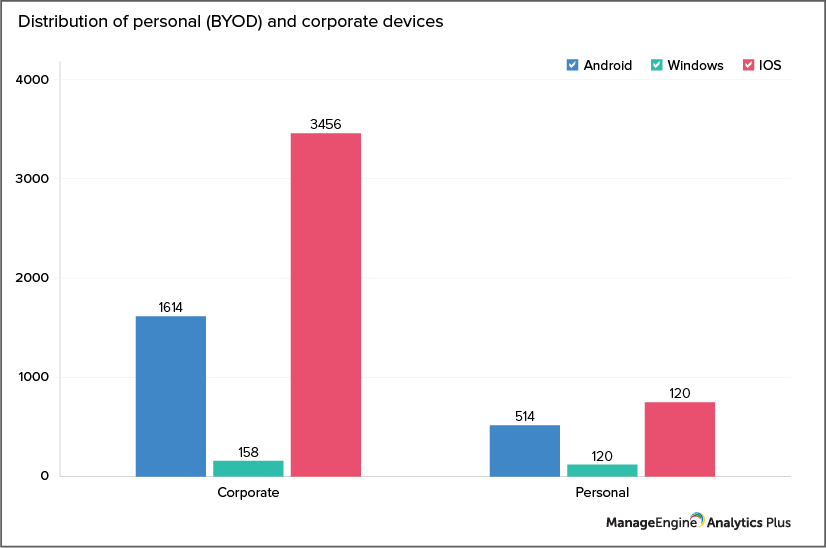
When your employees are working remotely, the probability of mobile devices getting lost, stolen, or damaged is astoundingly high. So, it’s crucial to closely track these devices to ensure their security.
While you can easily track the geographical location of devices by modifying the remote security settings in your Mobile Device Manager Plus application, it helps to pin down the location of these devices on a map.
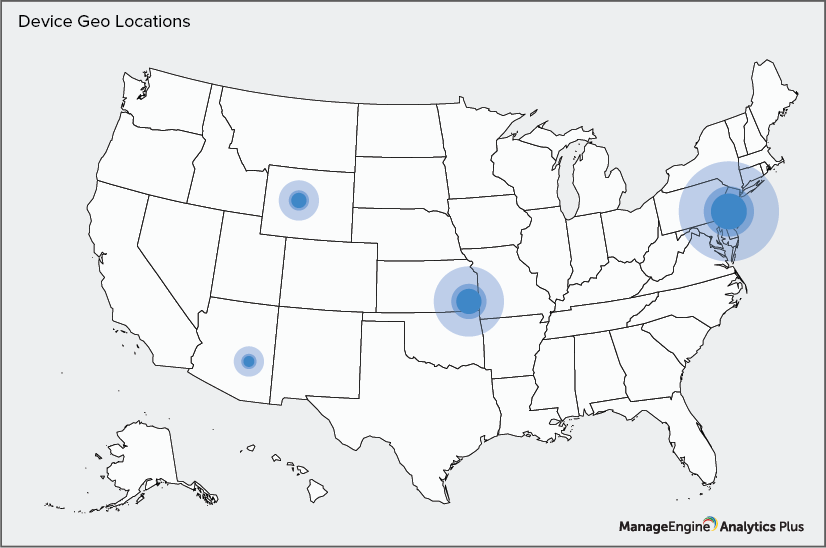
This graph gives a sample spatial location view of the various endpoint devices currently in use. Tagging each device in a map view makes it easier to raise an alarm when a device leaves its designated area, enabling you to lock it remotely or selectively wipe it clean of all corporate data.
2. Monitor
With most of your workforce going remote, a primary concern for organizations is to ensure employees have access to corporate resources (servers, networks, applications) without interruption so they can stay productive. However, this should not come at the cost of data security. A VPN can help a device securely connect to and download corporate data, but it’s important to ensure the data downloaded through a VPN stays secure.
For example, a device that allows other devices nearby to use its mobile data freely without a password (through a hot spot) is at a higher risk of getting hacked. To avoid such mishaps, look into devices that are missing critical restrictions, such as setting up hot spots, public Wi-Fi networks, or Bluetooth tethering. Once you identify the number and the owners of devices that are missing critical restrictions, it is easier to secure them.
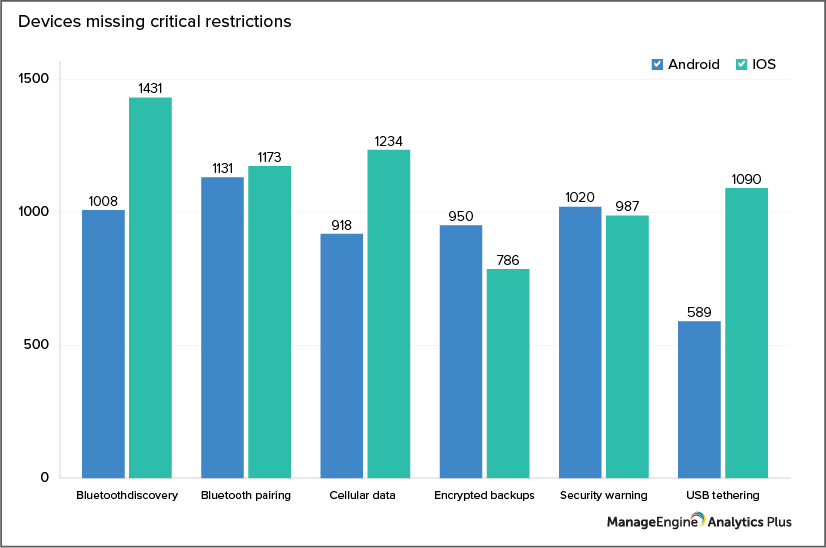
The example graph above shows the number of devices missing critical restrictions such as Bluetooth pairing, Bluetooth discovery, sharing cellular data, encrypted backups, etc.
Another notable high-risk behavior is installing and using blacklisted applications on mobile devices. Many mobile apps request access to the phone book, call history, camera, files and folders, and logs that might expose corporate data to an unintended audience. Since mobile devices in a BYOD environment are also meant for your employees’ personal use, your best bet is to track devices with blacklisted applications and take steps to remove these applications.
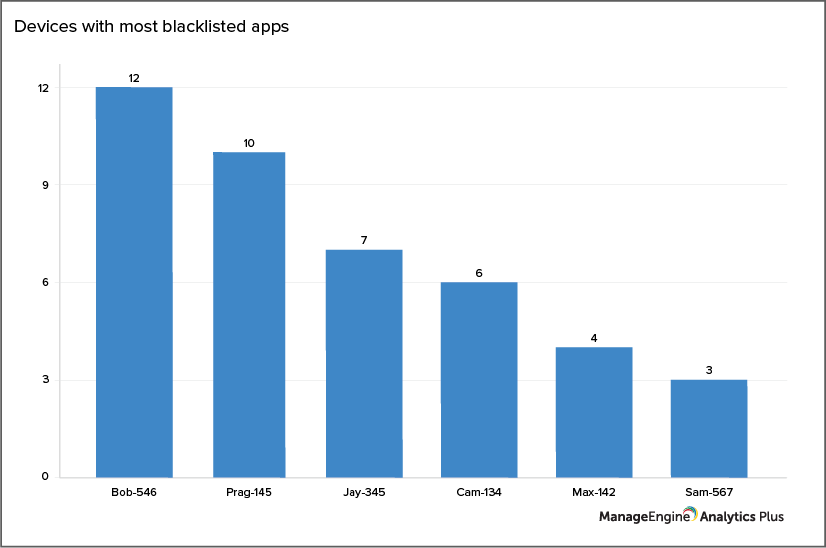
The sample graph above gives a list of devices in an organization that have installed the most number of blacklisted applications.
3. Control
The best way to prevent a security breach is to enforce stringent security policies for using endpoint devices. Start with passcode compliance. Audit all your devices and take stock of those that are non-compliant; then, impose strict measures to ensure passcode compliance.
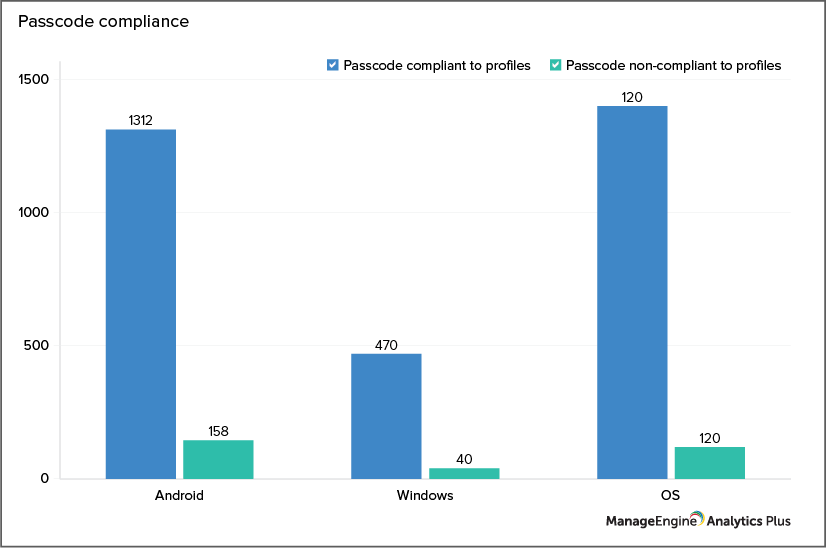
The graph above shows the number of Windows, Android, and iOS devices that are in compliance and non-compliance with the organization’s passcode policies.
Most mobile devices offer a variety of authentication methods, such as number or pattern lock, fingerprint or retinal scan, or voice recognition, that can be used to ensure security. Better yet, your organization can opt for multi-factor authentication to ensure these mobile devices don’t become easy gateways to your business-critical data.
The current remote work situation has turned endpoint devices into moving targets now that they are outside the security blanket of your corporate network. Meaning, the devices are outside firewalls, security and threat detection systems, and spam filtering processes that can protect them from threats. A solution is to ensure these devices are always in frequent contact with your Mobile Device Manager Plus server, and that you are notified anytime these mobile devices go out of contact for longer than 30 days.
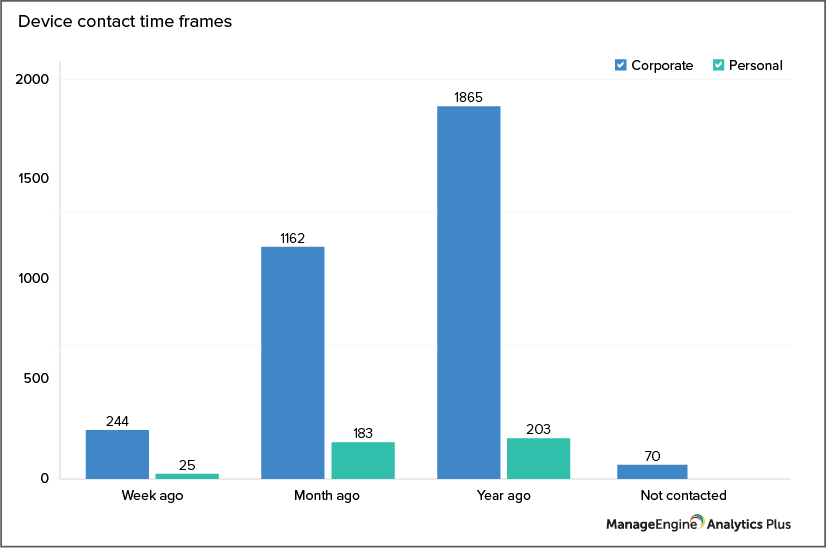
The report above shows a sample of the number of devices and the time span when they were last contacted. Using Analytics Plus, you can create threshold-based alerts on key metrics and get notified of the latest updates in your data via email or in-app alerts.
While some of the steps above might appear simple and some challenging, they should all be part of your security infrastructure. Remember, with the right security steps in place, your devices will be well-protected against threats, and your employees can take advantage of the many benefits of working from home without worrying about security.
Analytics Plus offers out-of-the-box integrations with Desktop Central, Mobile Device Manager Plus, Patch Manager Plus, Password Manager Pro and PAM360.
If you’re looking for an IT analytics solution, start your free, 30-day trial now.
If you’re already an Analytics Plus user, please upgrade to the latest version to enable new features and updates.

