The previous blog was on ASAM will have given you an idea about the class “Scan and Probes” available with NetFlow Analyzer. Now that we know how the events are triggered we need to narrow it down, that the specific events or unwanted events can be ignored.
When I say unwanted events, I mean the events that are deemed trusted or allowed network activities for certain resources and problems. To white list these kinds of events we have to fine tune this module.
To customize or fine tune the module we can make use of the following
1) White List: The White List option allows you to ignore specific events and discard specific flows.
1.a) Ignore Events: Allows you to ignore specific events of problems for any resource
1.b) Discard Flows: Allows you to discard flows for a specific problem.
2) Manage: The Manage option allows you to manage Problems, Algorithms, and Resources.
2.a) Manage Problem: Allows you to enable or disable a specific or set of problems
2.b) Manage Algorithm: Allows you to enable or disable a specific or set of Algorithms. If a specific algorithm is disabled, ASAM will not use the algorithm to generate events.
2.c) Manage Resource: Allows you to enable or disable resources for a specific resource type.
3) Algorithm Settings: Allows you to set the threshold value and the field type to be displayed in the offender and target column in the event list report.
3.a) Threshold Settings: Allows you to set threshold values for an algorithm
3.b) Offender/Target settings: You can select specific Offender/Target field to be displayed in the Event List report using this option
4) Location: The Location option allows you to manage the geographical and topological locations for offenders and target. Using this you can load/update geographical location, configure topological location, view/edit topologica
l location list, and configure location mode settings.
4.a) Load Geolocation: Allows you to load/update the geographical location of the IP addresses.
4.b) Add Topolocation: Allows you to configure the topological location for IP addresses
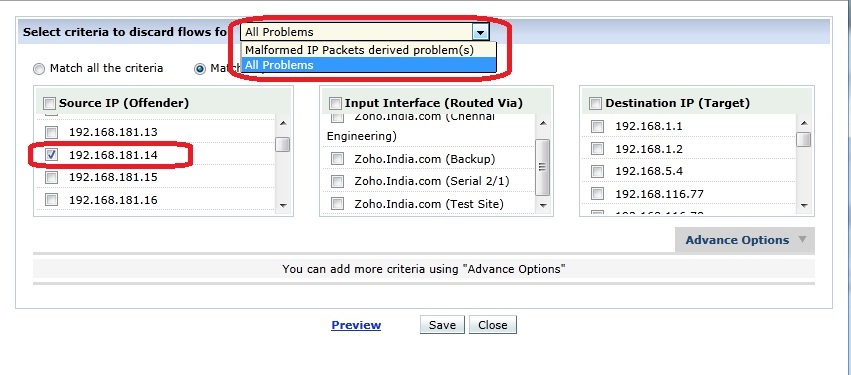
Now let me explain in the white listing with an example. Consider that I am using a server (say 192.168.181.14) for testing. I will be doing lots of ping to other destinations and doing a TCP header testing from this server. Hence I do not want the events to be generated for traffic from this server.
For this, first I will select an event generated from the IP address of the server and click on Whitelist. Here I will select the option discard flows which will open a new page. In this page I will be setting the needed criteria. In my case I will be setting “Select criteria to discard flows” to “All problems” and “Source IP (Offender)” to “192.168.181.14”. Once I have saved the settings, no events will be created with the source 192.168.181.14.
Once we have customized the ASAM module we are all set to go. We can monitor the anomalies in the network with the ASAM module and do the bandwidth monitoring with the help of NetFlow Analyzer.
You can download the 30 day trial from here.
Praveen Manohar
NetFlow Analyzer Technical Team
Download | Interactive Demo | Twitter | Customers
