Passwords on spreadsheets put client networks at risk, along with Managed IT service providers’ credibility and trustworthiness.
Managed IT Service Providers (MSPs) deliver a variety of IT and network management services to their clients. In particular, small and medium organizations are increasingly relying on MSPs to manage part or all of their IT services. Why? Because MSPs can help such organizations by saving costs, offering outside expertise, and meeting business demands quickly, among other critical points. Usually, tasks such as software development, network management, IT infrastructure management, customer support, and data center management are outsourced to MSPs.
MSPs that manage clients’ IT and network infrastructure typically get access to the clients’ enterprise application, servers, databases, firewalls, and other network devices as well as a lot of other equipment. In some cases, clients entrust the responsibility of managing their entire network or data center to MSPs. In other cases, MSPs get remote or shared access.
Clients’ network resources and other IT infrastructure are accessed and controlled by administrative passwords. Because MSPs typically manage the resources belonging to several clients, the access pattern becomes quite complex and sensitive, and the ever-increasing number of privileged passwords swamps the MSPs.
And in the absence of an appropriate management tool, password management can become quite cumbersome. Administrative passwords, which grant unlimited access privileges to IT assets, might be stored in plain text on volatile sources such as sticky notes, spreadsheets, printouts, and text documents. The passwords might also be shared among technicians without relevant protection. Such practices leave client organizations vulnerable to security attacks.
Identity Thefts & Haphazard Password Management: The Root of Cyber Attacks
Identity theft often lies at the root of modern-day cyber attacks. To gain access to IT resources, cyber criminals use various techniques to obtain employee login credentials and administrator passwords. Because MSPs manage the IT infrastructure for many clients, the risks involved are quite high. Especially, passwords kept on spreadsheets result in a host of security issues. Here are some high-risk factors and scenarios:
- Unrestricted or uncontrolled access — There is rarely any internal control on password access or usage. Technicians at the MSP have unrestricted access to all the passwords of all the clients managed by the MSP.
- Unaudited access with no trace of “who” accessed — Privileged passwords remain impersonal in shared environments. Mistakes, whether accidental or deliberate, can never be traced to the offender. There is generally no way to track “who” accessed “what” and “when.” This allows people to remain unaccountable for their actions.
- Temporary access becomes permanent — Passwords are given out orally or by emails to any contractor at the MSP who needs a privileged password on a temporary basis. Such a practice can be huge security hazard when there is no process to revoke temporary access and reset the password after usage.
- MSP technician leaves the organization, takes the passwords — When a technician leaves the MSP organization, the tech may take a copy of all the passwords. The only solution to such a scenario is to change all the privileged passwords of all the clients.
- Passwords fall into malicious hands — If the text file or spreadsheet that contains the administrative passwords reaches a malicious individual, client networks could be in jeopardy.
- Passwords remain unchanged for ages — Passwords of even the most sensitive resources like firewalls remain unchanged at the MSP to prevent lockouts. Manually changing the passwords of thousands of resources can be time-consuming. Worse, most resources are assigned the same, non-unique password for ease of coordination among administrators.
Such flawed password management practices make the MSP a paradise for hackers, both inside and outside the organization. Many security incidents and data breaches actually stem from lack of adequate password management policies and internal controls.
Earning and sustaining the trust of customers is essential for all businesses, more so for MSPs. Lack of proper password management could destroy the very foundation of trust.
Privileged Access Mandates: Control, Monitor, Audit, and Automate
With clients concerned about cyber security, MSPs should accord top priority to secure passwords and control privileged access. In fact, privileged password management is the foundation for IT security. Access to each client’s network and resources should be based on job roles and responsibilities, and all access must be monitored closely.
The MSP should be in a position to find and tell who has access to which resources. All activities performed by the MSP technicians should be audited. Only an automated privileged password management solution that caters to the specific needs of MSPs can fulfill all these requirements.
Privileged Password Management for MSPs: Critical Considerations
MSPs must expect the following in a privileged identity management solution:
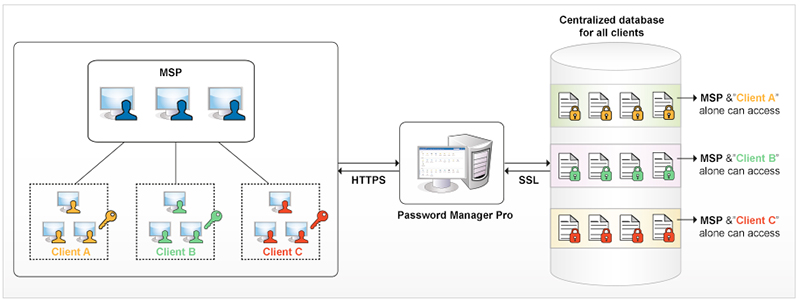
- Ability to securely store and manage client passwords from a centralized console with clear data segregation — the solution should have the provision for managing the privileged passwords of the IT assets of all clients from a single console. You should also be able to achieve complete segregation on data storage. A multi-tenant architecture is necessary to provision this.
- Provision to selectively share among MSP technicians and clients — The very business model of MSPs demands concurrent access to IT resources and applications, both by MSPs and administrators at the client site. There should be a provision to selectively share passwords between MSP technicians and their respective clients with granular access restrictions based on job roles and responsibilities.
- Control access to privileged accounts and, thereby, to client network — Access to the privileged passwords of client networks should be limited to a select few technicians and access should be strictly based on job roles and responsibilities. Users should get access only to the passwords they need to perform their duties.
- Visibility on password access — MSPs should be able to easily find out who has access to which passwords and which technician is managing the infrastructure of a client. A complete picture on the access scenario should be readily available to gain complete control and also to safeguard client data.
- Provision to automatically reset/randomize passwords — Security best practices demand that passwords be reset and randomized periodically. The password management solution should support a wide range of target systems for remote password reset. In addition, when a technician leaves the MSP organization, all the passwords accessed by that user should be randomized.
- Grant remote access without revealing passwords in plain text — A robust mechanism that allows users to launch a secure, direct connection with remote IT resources — without revealing the underlying passwords in plain text — is an absolute must. This mechanism will be necessary when you need to provide access to the client’s data center to select MSP technicians without exposing the credentials.
- Record activities as audit trails and session videos — All password management activities done by the MSP technicians should be audited and monitored. Auditing alone is not sufficient. Privileged activities on sensitive resources should also be monitored in real time. Privileged operations done on remote resources should be video recorded for forensic analysis.
- Provision for administrator approvals and password release workflow — Users requiring access to highly sensitive passwords should be directed to go through a password request-release workflow for tighter access controls. Passwords will be released on-demand to MSP technicians by MSP administrators for a limited time period. At the end of the usage period, access should be revoked and passwords should be automatically reset.
- Provision for uninterrupted access — With all passwords stored inside the vault, uninterrupted access to the password vault is essential for MSPs to run their businesses. The password management solution should have a high-availability architecture built in.
- Instantly provision, deprovision — When a new technician joins the MSP, passwords should be provisioned immediately. Similarly, when a technician quits the organization, access should be removed instantly.
- Demonstrate security to win trust — MSPs should be able to generate reports on clients’ passwords to see access details, enforcement of policies, and adoption of best practices. For MSP customers, the reports demonstrate that their data and the MSP’s infrastructure are being securely handled. This is essential for winning the trust of clients.
To combat ever-increasing cyber attacks, MSPs should focus on securing privileged identities, controlling and monitoring privileged access, and adopting stringent security best practices. MSPs can easily achieve a high level of security by using privileged password management solutions.
While there are many good enterprise-class privileged password management solutions on the market, only a few cater to the specific needs of the MSPs. ManageEngine Password Manager Pro offers a full-fledged MSP edition, which has been designed specifically for MSPs. Password Manager Pro MSP Edition is completely aligned with the business goals of MSPs, requires no configuration effort, and is affordable and highly secure.
Cyber threats are looming large and no organization is immune to attacks. Lack of proper attention to privileged password management increases the probability of attacks. Meticulous planning and tighter internal controls can help dramatically limit the risk of attacks.
(This is a repost of my article published in Network Middle East)
Bala
Password Manager Pro – Quick Video | Free Trial Download | White Papers | Success Stories