DLL sideloading: The invisible attack
The state of today's threat landscape is like the two sides of a coin: on one side, you have organizations enforcing strong security measures, and on the other side, you have cyberattackers constantly developing new techniques to circumvent them. One technique commonly used by attackers to avoid detection is DLL sideloading. In this stealthy attack, attackers slip malicious code right under an organization's security radar.
Understanding DLL sideloading attacks
First, let's cover the basics. A dynamic link library (DLL) is a shared library that contains code and data used by multiple programs simultaneously. Applications rely on DLL to share common functions instead of having to include those functions within their own code. For instance, many applications rely on DLL to handle common tasks like displaying graphics. DLLs are particularly helpful for adding updates and improvements to an application, as DLL files can be easily replaced to provide updates instead of reprogramming the entire application. However, attackers have learned to use DLL as a backdoor entry into systems.
In DLL sideloading, attackers replace the DLL files with malicious code, infecting the application when it loads the DLL. The attackers make subtle changes to these files in such a way that the execution flow does not get affected, and it is easily overlooked.
Why doesn't antivirus software detect malware introduced by DLL sideloading? While antivirus solutions are designed to detect malicious files, static analysis in antivirus often relies on signature-based detection to identify malware patterns. In DLL sideloading, since the attackers encrypt the malicious code, it evades signature detection. Moreover, when the malicious code runs from within a trusted application, the behavior deviation is minimal, making it harder to detect.
This is where a next-gen antivirus solution steps in. Unlike traditional antivirus tools that focus on scanning files stored on a disk, next-gen antivirus actively monitors process memory in real time. This allows it to spot malicious code after it has been decrypted and loaded into the memory, enabling the detection of DLL sideloading attacks.
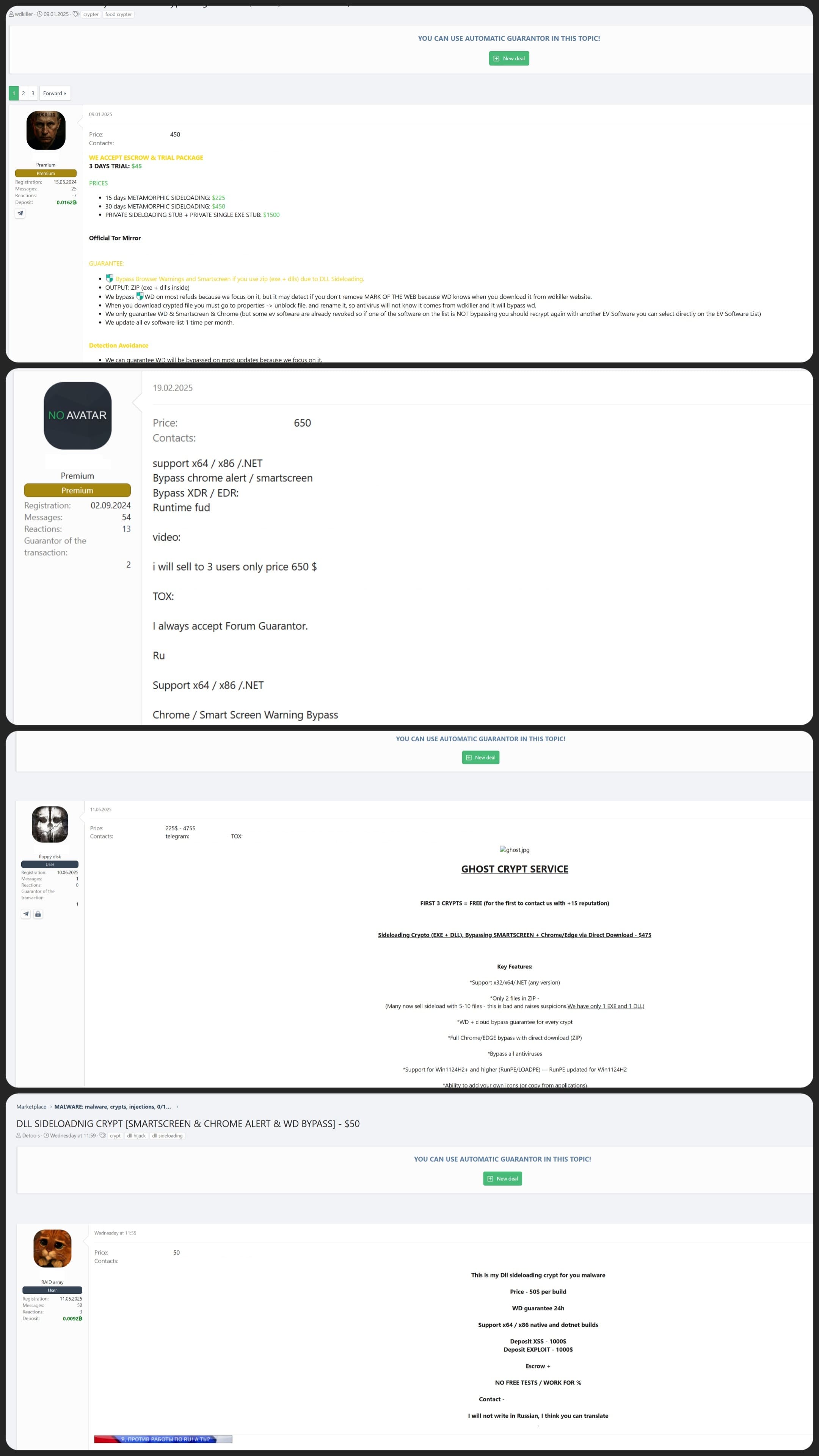
The growing popularity of DLL sideloading attacks
A not-so-surprising fact is that detection evasion is available as a service on the dark web. Within the first half of 2025 alone, there are four new services in the dark web providing DLL sideloading, highlighting its growing popularity. With evasion being handled by these underground services, attackers can more easily focus on the later stages of attack, such as data exfiltration.
To reduce the risks of DLL sideloading, organizations should implement application control, which allows only trusted applications run in the network. While this does not directly block DLL sideloading, it limits the attackers' options by preventing them from executing unauthorized applications that could be used to load malicious files, reducing the overall attack surface. In addition, organizations can turn to next-gen antivirus solutions, which utilize AI and ML algorithms to detect and block threats.
Want to check out these features at no cost? Start your 30-day, free trial of ManageEngine Endpoint Central.