Active Directory (AD) administrators are heading into 2019 with security on their minds. The attacks of the past combined with the movement toward hybrid environments...
azure
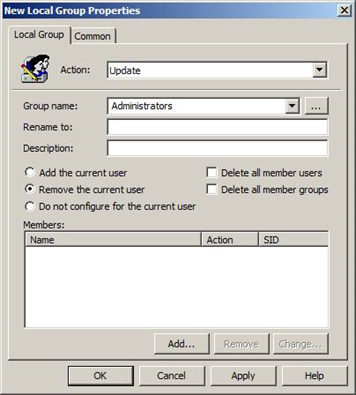
Minimizing membership in the local Administrators group on workstations
If you have a long list of users with administrative rights, there’s a good chance you’ve offered excessive amount of privilege to accounts that don’t...
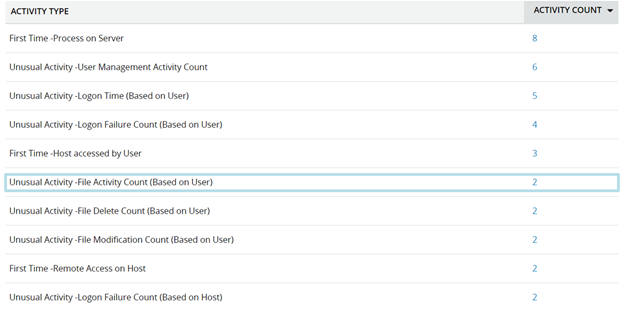
Monitoring users for unusual file activity
As we discussed in a previous blog, the user behavior analytics (UBA) engine of ADAudit Plus can help administrators identify anomalies by establishing a baseline...
Leveraging logic and AI to detect malicious behavior in Active Directory [Webinar]
Active Directory is still vital for every organization that’s staying on-premises or moving to a hybrid environment. Protecting Active Directory from attacks is also essential, but many of the...
Monitoring Active Directory and Windows computers to detect attacks [Webinar]
If organizations and administrators can be alerted when they’re under attack, then they can take immediate action to negate the attack. The issue with alerts...
User behavior analytics for streamlined threat detection
Cyberthreats are on the rise and breaches are becoming more common. Many businesses rely on technology to protect themselves, but attackers also use technology to...
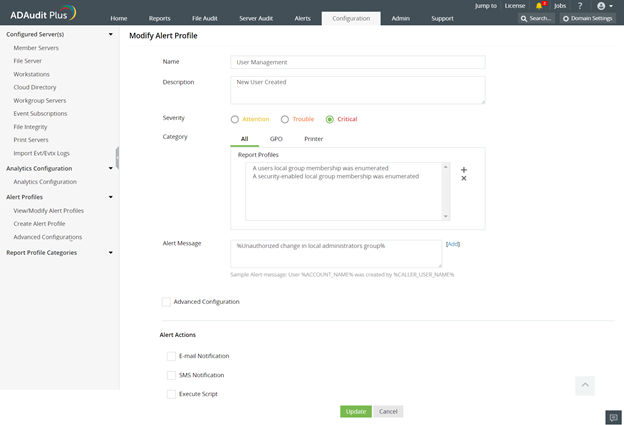
Secure workstations by monitoring and alerting on membership changes in the local Administrators group, Part 2
In Part 1, we touched on how routine monitoring of object life cycle changes in the local Administrators group can help strengthen your organization’s overall...
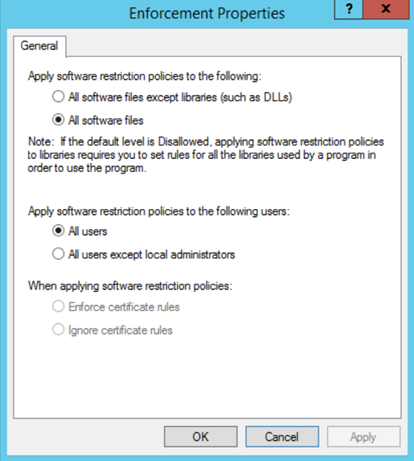
Application whitelisting using Software Restriction Policies
Software Restriction Policies (SRPs) is a Group Policy-based feature in Active Directory (AD) that identifies and controls the execution of various programs on the computers...
Secure workstations by monitoring and alerting membership changes on Local Administrators Group, Part 1
Imagine you’re an admin in a company that prides itself on its security practices, which includes using firewalls, IDP systems, and IPS systems. You have...